





After taking over the domains for the notorious Coinhive in-browsing Monero mining service, a researcher is now displaying alerts on hacked websites that are still injecting the mining service’s JavaScript.
CoinHive was an in-browser cryptocurrency mining platform that allowed websites to inject JavaScript code into websites to mine Monero using a visitor’s browser and CPU. Any cryptocurrency mined on the site would then be shared between CoinHive and the website owner, with the owner receiving the larger share.
While Coinhive was used legitimately in a few cases, such as to raise money for charity, the majority of times, it was used to illegally mine cryptocurrency without a user’s permission.
It became so pervasive at its height that it was injected into over 200,000 routers, added to browser extensions, injected into Microsoft Store apps, and even injected on government sites through a JavaScript supply-chain attack.
While a research paper stated that CoinHive was generating $250,000 a month from its service, security companies increasingly began detecting and blocking it, making it less profitable as time went on.
Due to this loss of profitability and increasing difficulty in mining Monero, CoinHive shut down its operation on March 8th, 2019.
Also Read: How To Comply With PDPA: A Checklist For Businesses
In a new blog post released today, Have I Been Pwned’s Troy Hunt revealed that he was given coinhive.com and other related domains for free as long as he would do something useful with them.
“In May 2020, I obtained both the primary coinhive.com domain and a few other ancillary ones related to the service, for example cnhv.co which was used for their link shortener (which also caused browsers to mine Monero).”
“I’m not sure how much the person who made these available to me wants to share so the only thing I’ll say for now is that they were provided to me for free to do something useful with,” Hunt explains in a blog post published today.
As these domains are hosted behind Cloudflare, Hunt has utilized their built-in analytics to see that a tremendous amount of visitors still attempt to load JavaScript from the CoinHive domains.
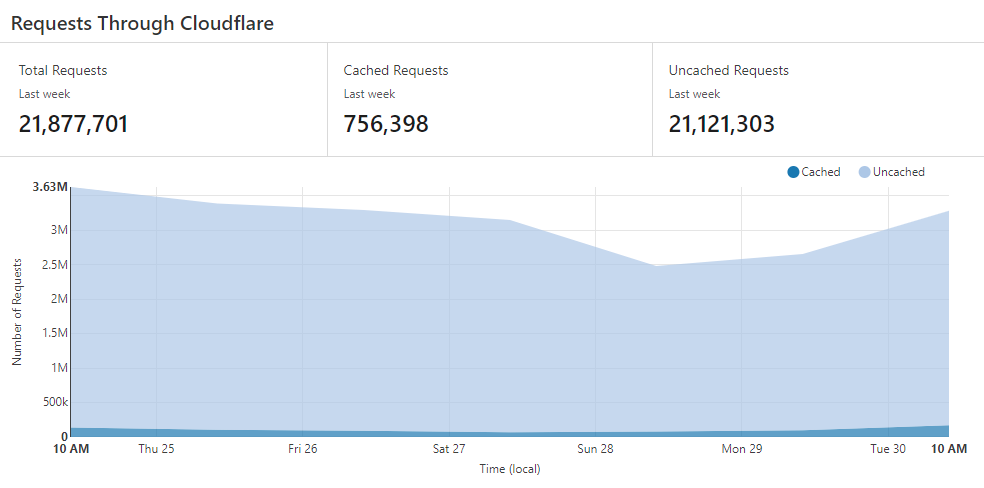
The top five countries pushing traffic to the CoinHive domains are China, Russia, United States, Georgia, and Vietnam.
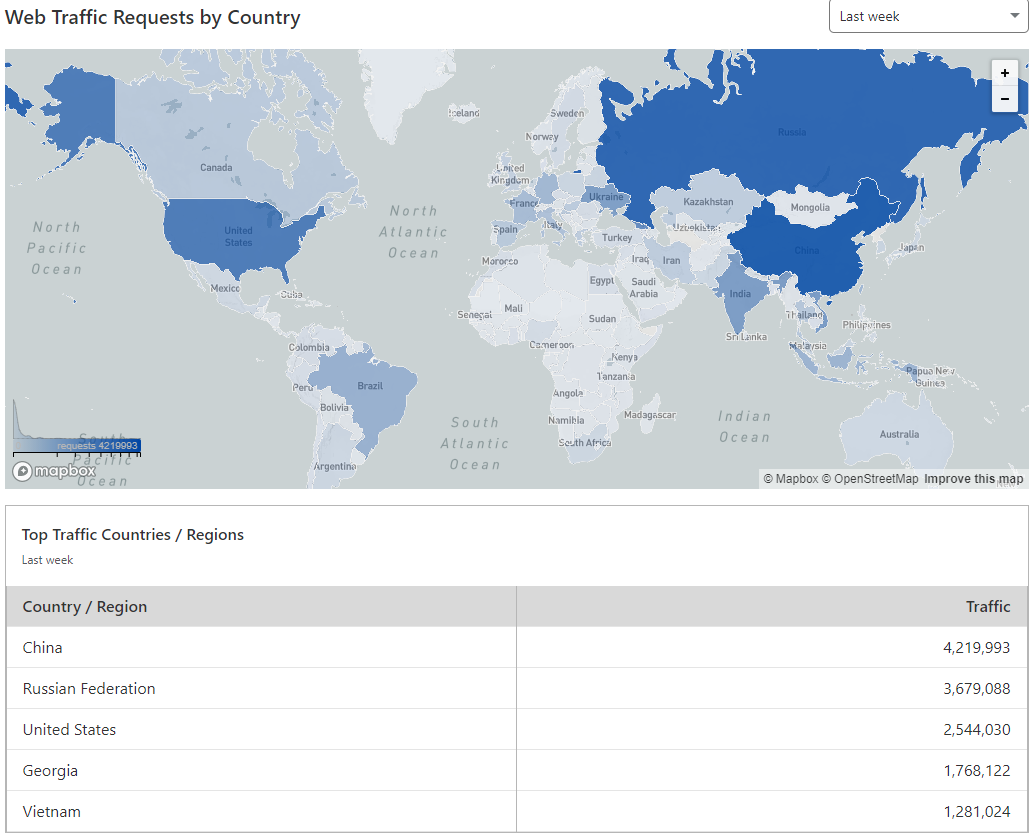
From the analysis of the sites referring traffic to the Coinhive domains, Hunt stated that CoinHive scripts are still injected mostly from China and Russia websites.
It is also believed that a lot of this traffic could be caused by compromised MikroTik routers that continue to inject CoinHive scripts when users visit websites.
When Hunt originally received the domains, he was asked to put them to good use.
Today, Hunt revealed that he is now redirecting the coinhive.com domain to his new blog post about Coinhive at TroyHunt.com.
When people visit sites with injected Coinhive scripts, he pushes out his own JavaScript code that displays a modal dialog stating, “This web site attempted to run a cryptominer in your browser.”
The alert is a link where users can click to learn more about the CoinHive injected on the website, as shown below.
Also Read: In Case You Didn’t Know, ISO 27001 Requires Penetration Testing
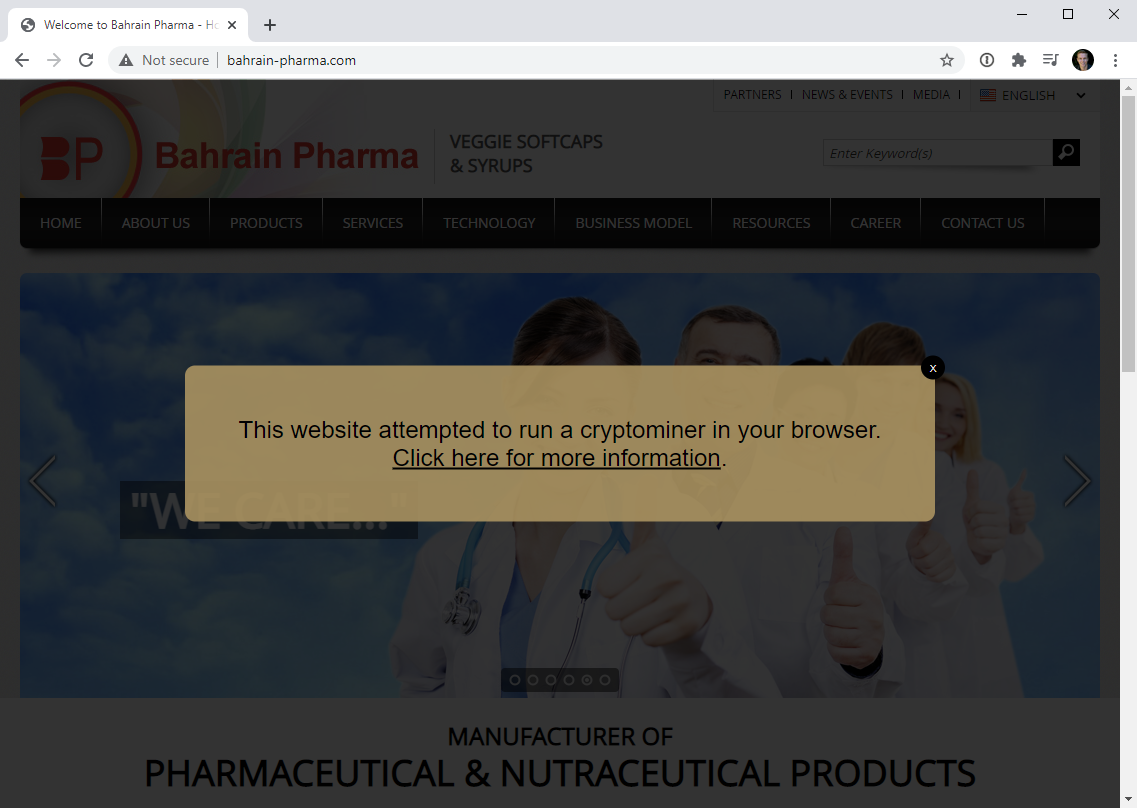
While Hunt uses the Coinhive domains for good purposes, such as warning a site’s visitors of the injected scripts, his use of the Coinhive domains illustrates how bad actors could use abandoned domains to inject scripts into unsuspecting visitor’s browsers.
“Oh – and while we’re here let’s just let that sink in for a moment: I can now run whatever JavaScript I want on a huge number of websites.”
“So, what could I do with JavaScript? I could change where forms post to, add a key logger, modify the DOM, make external requests, redirect to a malicious file and all sorts of other very nasty things.”
“That’s the power you hand over when you embed someone else’s JS in your own site and that’s precisely why we have subresource integrity,” warns Hunt.