





Cloudflare has released a new feature that aims to protect websites from Magecart and other malicious JavaScript-based attacks.
A typical cyberattack is introducing malicious JavaScript onto a website to redirect visitors to malicious sites, display phishing forms, exploit vulnerabilities, and steal submitted payment information.
To introduce malicious scripts on a website, threat actors will commonly add the malicious inline JavaScript to the web page, add an external malicious JavaScript dependency file under their control, or compromise an existing third-party script in a supply-chain attack.
When JavaScript is loaded from an external location as a dependency, in many cases, they go unnoticed for a long time, especially when there is no outward change in a site’s user experience.
For example, Magecart attacks are conducted by introducing malicious JavaScript that steals credit card information submitted on a website. As this data is quietly transmitted to a remote location and purchases continue, as usual, users will not notice anything strange that they should report to the site.
Due to this, Magecart attacks can quietly steal credit cards from visitors for many months, if not years, before they are detected and resolved.
Also Read: What Does A Data Protection Officer Do? 5 Main Things
Today, Cloudflare announced a new security feature called Page Shield that will detect attacks in end-user browsers caused by malicious JavaScript dependencies.
“Our mission is to help build a better Internet. This extends to end-user browsers, where we’ve seen an alarming increase in attacks over the past several years. With Page Shield, we will help applications detect and mitigate these elusive attacks to keep their user’s sensitive information safe,” Cloudflare announced today.
With today’s unveiling of Page Shield, Cloudflare is starting with a ‘Script Monitor’ tool that will report to Cloudflare every time a visitor on a protected site executes a JavaScript dependency file in their browser.
Using these reports, Cloudflare will build a history of known scripts utilized on the site. When a new one is detected, alert the website administrator so they can investigate further.
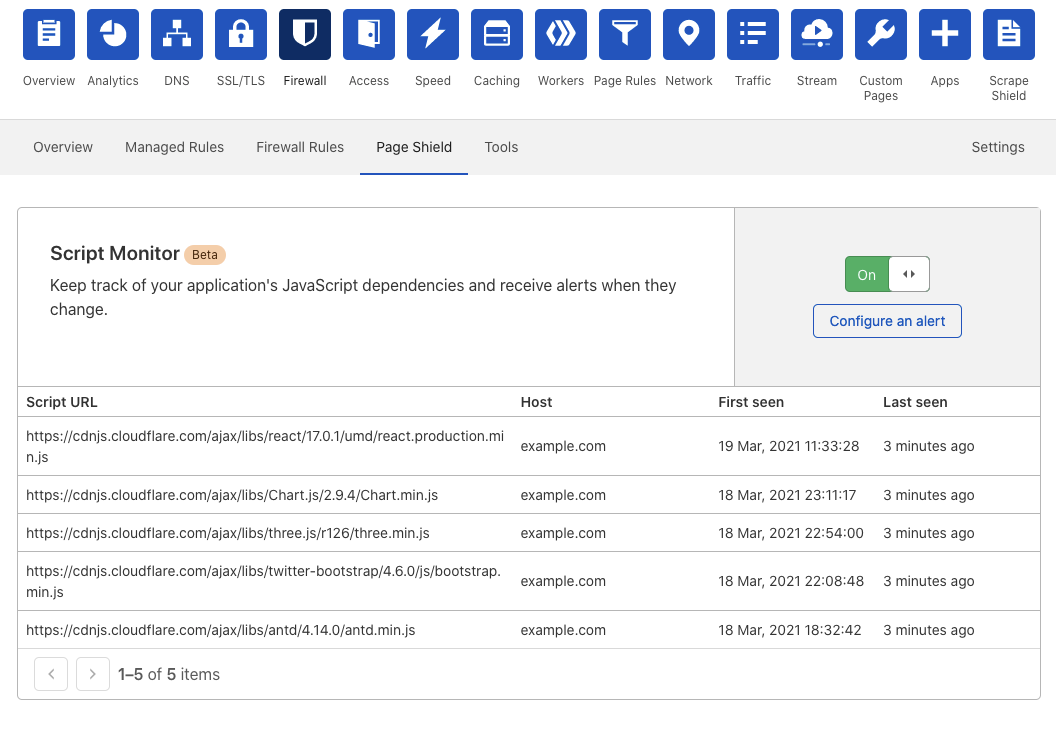
Using the Script Monitor, web admins can spot suspicious JavaScript files being loaded by visitors on their sites and quickly investigate whether they are malicious.
While a good start, this does not protect visitors from existing JavaScript dependencies that have been modified in a supply-chain attack.
For example, if a site has historically loaded a JavaScript file from https://www.example.com/js/harmless.js and a threat actor modified that file on example.com, Script Monitor would not detect the change, and the malicious code would be allowed to execute in a supply-chain attack.
In the future, Cloudflare states that they plan on adding additional features that will issue alerts when the content of a script has changed of contains malicious signatures.
Overall, this is an exciting tool for Cloudflare users to help detect if your site has been hacked to load malicious JavaScript files.
However, this feature is only coming to Business and Enterprise subscriptions, and those in the Pro or Free services levels will not be able to benefit from the service.
Also Read: The DNC Registry Singapore: 5 Things You Must Know
If you are interested in testing the new Page Shield feature, you can signup to join Cloudflare’s beta test.