KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Cisco has addressed a new critical severity remote code execution (RCE) vulnerability affecting several versions of Cisco Jabber for Windows, macOS, and mobile platforms after patching a related security bug in September.
Cisco Jabber is an instant messaging and web conferencing desktop app built using the Chromium Embedded Framework (CEF).
The app delivers messages between users using the Extensible Messaging and Presence Protocol (XMPP) and also provides them with presence and desktop sharing features.
Cisco released security updates in September to address a critical RCE security vulnerability tracked as CVE-2020-3495 stemming from a Cross-Site Scripting (XSS) bug in Cisco Jabber.
Since then, a new wormable RCE vulnerability was found by researchers at Watchcom who reported it to Cisco after checking if the September patch fully mitigated CVE-2020-3495.
“During this audit, we discovered that the most severe vulnerabilities, including the RCE vulnerability, have not been properly mitigated and that users remain vulnerable,” Watchcom says.
“Patches are now available and we urge all Cisco Jabber users to update as soon as possible!”
In all, the researchers reported four Cisco Jabber client vulnerabilities in September and, as they found, three of them were not insufficiently mitigated by Cisco’s patches.
This allowed them to spot new vulnerabilities that could be abused to exploit all currently supported Cisco Jabber versions, from 12.1 up to 12.9.
Also Read: 10 Practical Benefits of Managed IT Services
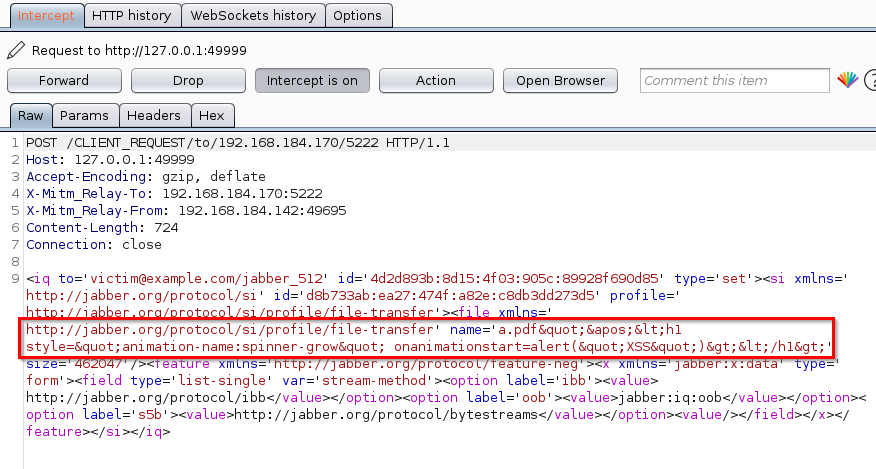
Just as the previous flaw, the newly discovered RCE vulnerability tracked as CVE-2020-26085 is an XSS bug that can allow attackers to execute arbitrary code remotely by escaping Cisco Jabber’s CEF sandbox.
Just as CVE-2020-3495, it is also caused by improper input validation of incoming messages’ contents and it received an almost maximum 9.9 CVSS base score.
“This vulnerability does not require user interaction and is wormable, since the payload is delivered via an instant message,” Watchcom says. “This means that it can be used to automatically spread malware without any user interaction.”
Watchcom’s researchers also spotted a second bug (CVE-2020-27132), a password hash stealing information disclosure vulnerability that can allow attackers to harvest NTLM password hashes from targets using vulnerable Cisco Jabber versions.
The third and last vulnerability (CVE-2020-27127) discovered while auditing Cisco’s September patches is caused by a command injection bug in the app’s custom protocol handlers that can enable attackers to take over the browser embedded in the targets’ Cisco Jabber client.
“Since some of the vulnerabilities are wormable, organizations should consider disabling communication with external organizations through Cisco Jabber until all employees have installed the update,” Watchcom warns. “This can be done by disabling XMPP federation or configuring a policy for XMPP federation.”
This can be done by initiating file transfers containing malicious .exe files and forcing the victims to accept them using an XSS attack.
This further allows the attackers to execute the malicious file on a target’s computer without requiring any user interaction.
A video of how attackers could use the Cisco Jabber vulnerabilities patched in September 2020 is embedded below.
However, for the newly discovered vulnerabilities, “the attacker’s code would be added to a file-sharing message instead of a regular message,” as Watchcom ‘s Olav Sortland Thoresen told BleepingComputer.
Also Read: Limiting Location Data Exposure: 8 Best Practices