KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







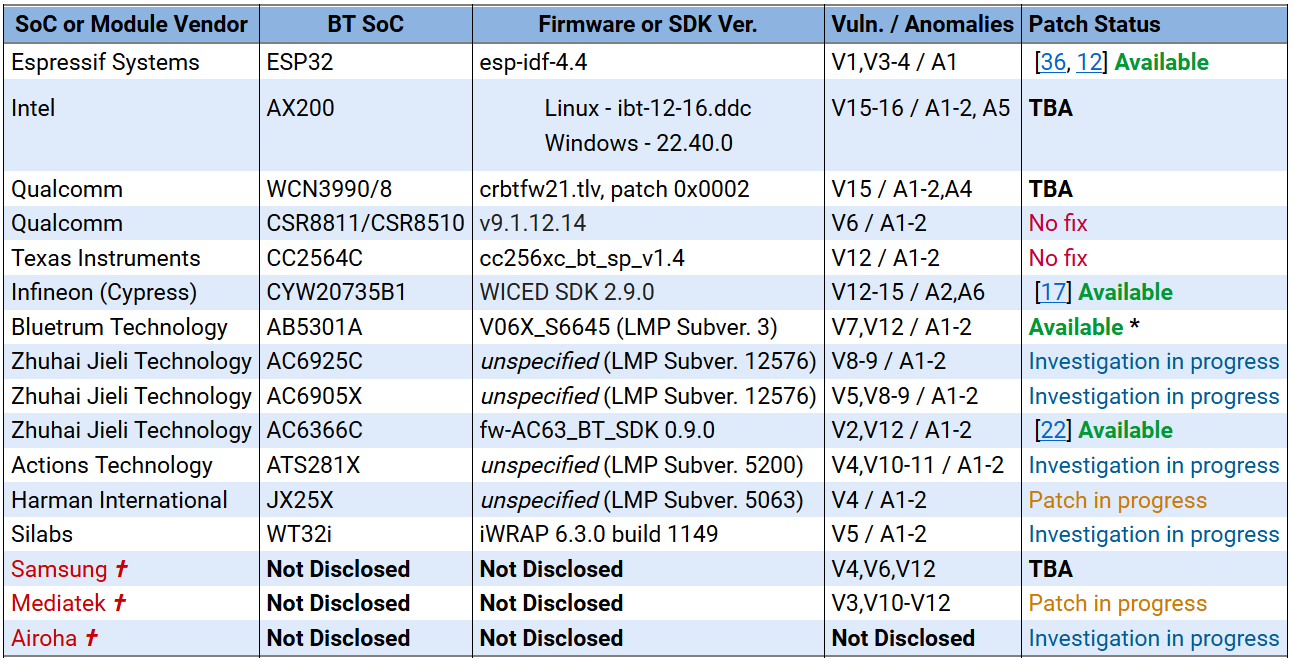
Researchers have released public exploit code and a proof of concept tool to test Bluetooth devices against System-on-a-Chip (SoC) security bugs impacting multiple vendors, including Intel, Qualcomm, Texas Instruments, and Cypress.
Collectively known as BrakTooth, these 16 flaws impact commercial Bluetooth stacks on over 1,400 chipsets used in billions of devices such as smartphones, computers, audio devices, toys, IoT devices, and industrial equipment.
Also Read: 15 Best Tools For Your Windows 10 Privacy Settings Setup
The list of devices with vulnerable SoCs includes Dell desktops and laptops, MacBooks and iPhones, multiple Microsoft Surface laptop models, Sony and Oppo smartphones, Volo infotainment systems,
CISA asked vendors Thursday to patch these vulnerabilities after the security researchers released the proof of concept tool to test Bluetooth devices against BrakTooth exploits.
The federal agency also encouraged manufacturers and developers to review the vulnerability details published by researchers in August and “update vulnerable Bluetooth System-on-a-Chip (SoC) applications or apply appropriate workarounds.”
The impact associated with the BrakTooth bugs ranges from denial-of-service (DoS) by crashing the device firmware or freezes via deadlock conditions that block Bluetooth communication to arbitrary code execution that can lead to complete takeover depending on the vulnerable SoC used in the targeted device.
Threat actors who may want to launch a BrakTooth attack would only need an off-the-shelve ESP32 board that costs less than $15, custom Link Manager Protocol (LMP) firmware, and a computer to run the proof-of-concept (PoC) tool.
While some vendors have already issued security patches to address the BrakTooth vulnerabilities, it will take months to propagate to all unpatched devices.
Also Read: How To Secure Your WiFi Camera: 4 Points To Consider
In other cases, vendors are still investigating the issues, are still working on a patch, or haven’t yet announced their patch status.
A list of impacted vendors tracked by the researchers and their patch status can be found here or in the table embedded below.