KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The CHwapi hospital in Belgium is suffering from a cyberattack where threat actors claim to have encrypted 40 servers and 100 TB of data using Windows Bitlocker.
On Sunday, CHwapi suffered an attack that caused the hospital to redirect patients to other hospitals and delay surgical procedures.
While the hospital’s services are slowly recovering and surgical operations have resumed, CHwapi continues to cancel some services and redirect urgent cases to other hospitals.
– Information sessions for future parents on January 20 and 21 are canceled.
– The consultations are maintained;
– Surgical operations resumed this Wednesday, January 20;
– Patient data has not been compromised;
– The distribution circuit of Covid vaccines in MR / MRS is not disrupted;
– For the moment, the CHwapi no longer receives urgent cases sent by service 100. Patients are redirected to other hospitals.
According to Belgium media L’Avenir , CHwapi was attacked on Sunday at 8:46 PM when attackers encrypted 80 out of 300 servers, but the hospital did not receive a ransom demand.
If you have first-hand information about this or other unreported cyberattacks, you can confidentially contact us on Signal at +16469613731 or on Wire at @lawrenceabrams-bc.
Also Read: How To Prevent WhatsApp Hack: 7 Best Practices
On Tuesday, BleepingComputer was contacted by threat actors who state that they were responsible for the attack on CHwapi.
According to the attackers, they used Windows BitLocker to encrypt 40 servers and 100TB of data. After encrypting devices, the attackers state they left ransom notes named ransom.txt on the domain controllers and backup servers.
“We attack chwapi hospital in belgium 2 days ago.and set up a ransom notes on servers. but IT management team not give this information to hospital management.hospital management make a press release and said there is no ransom note,but this is a lie.something is going on,” the threat actors emailed BleepingComputer.
Instead of using traditional ransomware, this group uses off-the-shelf software such as Windows BitLocker and DiskCryptor to encrypt files and lock access to the disk partitions with a password.
The threat actors told BleepingComputer that they do not encrypt every device on the network and only target servers holding large amounts of files, such as file servers and backup servers.
To communicate with victims, the this hacking group creates ransom notes containing a Bitmessage ID that can be used to negotiate a ransom. Below you can see an example of this group’s ransom note from an unrelated attack.
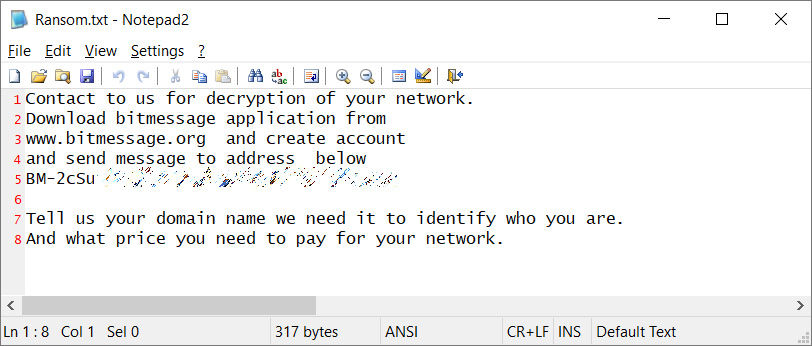
This group states that they are not part of a Ransomware-as-a-Service (RaaS) and do not steal or leak data.
Some ransomware gangs have stated that they will avoid encrypting hospitals and provide a free decryptor if they are encrypted.
When we asked the threat actors if they would follow a similar policy and provide a free decryptor to CHwapi hospital, we did not receive a clear answer.
Also Read: The 5 Benefits Of Outsourcing Data Protection Officer Service
BleepingComputer has contacted CHwapi with questions about this attack but did not receive a response.