KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Chile’s Comisión para el Mercado Financiero (CMF) has disclosed that their Microsoft Exchange server was compromised through the recently disclosed ProxyLogon vulnerabilities.
The CMF operates under the Ministry of Finance and is the regulator and inspector for banks and financial institutions in Chile.
This week, CMF disclosed that they suffered a cyberattack after threat actors exploited the recently disclosed ProxyLogon vulnerabilities in their Microsoft Exchange servers to install web shells and attempt to steal credentials.
“The Commission for the Financial Market (CMF) updates information on the operational incident reported yesterday, caused by vulnerabilities in the Microsoft Exchange email platform.”
“The analyzes carried out by the information security and technology area of the CMF, together with external specialized support, have so far dismissed the presence of a ransomware and indicate that the incident would be limited to the Microsoft Exchange platform,” disclosed the Comisión para el Mercado Financiero.
CMF further states that they are investigating the breach and have been in contact with the Computer Security Incident Response Team (CSIRT) of the Ministry of Finance.
Also Read: The DNC Singapore: Looking At 2 Sides Better
To aid security professionals and other Microsoft Exchange administrators, the CMF has released IOCs of web shells and a batch file found on their compromised server.
While indicators of compromise (IOC) will have different file hashes for each victim, in many attacks, the file names have been the same.
Web shells using the names ‘error_page.asp’ and ‘supp0rt.aspx’ have been used in numerous ProxyLogon attacks, and for the most are part, are identical with only a few changes specific to the victim.
These files are Microsoft Exchange Offline Address Books (OAB), whose ExternalUrl setting has been changed to the China Chopper web shell. This web shell allows threat actors to execute commands on the compromised Microsoft Exchange server remotely by visiting the URL configured in the ExternalURL setting.

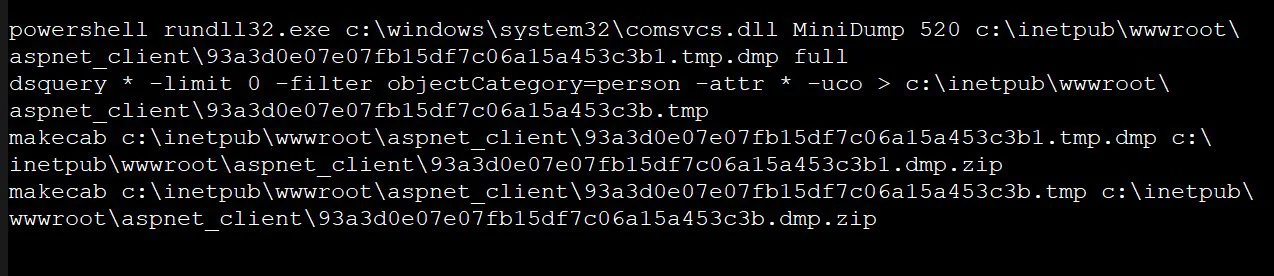
The batch file, test.bat, is also commonly seen in ProxyLogon attacks and is used to dump the LSASS process’s memory to harvest Windows domain credentials. The batch file also exports a list of users on the Windows domain.
The command shown below will use the comsvcs.dll LOLBin to dump LSASS’ memory to a file in the IIS server’s wwwroot. It then uses dsquery to export a list of users in the Windows domain to a file.
These files are then zipped up in the wwwroot to be downloaded remotely by the threat actors.
While most Microsoft Exchange attacks have been deploying web shells, harvesting credentials, and stealing mailboxes, some attacks are also installing cryptominers, and more recently, the DearCry ransomware on exploited servers.
Also Read: 4 Best Practices On How To Use SkillsFuture Credit
To help administrators find malicious files dropped in these attacks, Microsoft has released a script that searches Microsoft Exchange logs for IOCs and has updated their Microsoft Safety Scanner (MSERT) to detect known web shells.