KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The developer of the 16Shop phishing platform has added a new component that targets users of the popular Cash App mobile payment service.
Deployment of the new 16Shop product started as soon as it became available, luring potential victims into providing sensitive details that would give fraudsters access to the account and the associated payment information.
16Shop is a complex phishing kit from a developer known as DevilScream, who set up a protection mechanism against unlicensed use and research activity.
The kit is commercially available and localized in multiple languages. Until recently, it provided code and templates to steal login credentials and payment card details for PayPal, Amazon, Apple, and American Express.
Towards the end of February, though, a new option became available in the 16Shop store with a $70 tag that targets the Cash App accounts. The app is immensely popular, with more than 10 million installations on Android and over 1.6 million ratings giving it 4.7 out of 5 stars in the App Store.
Security researchers from cybersecurity company ZeroFOX obtained the new Cash App phishing kit on February 25, which was just a day after the final compile time.
Also Read: 4 Considerations In The PDPA Singapore Checklist: The Specifics
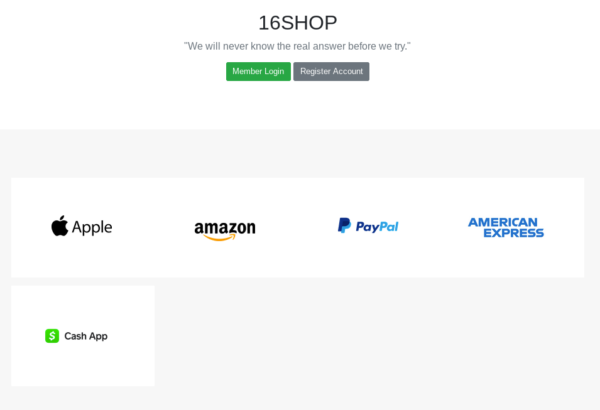
It appears that fraudsters rushed to get it and to deploy it as researchers spotted multiple deployments within a day from 16Shop offering the Cash App phishing kit.
This is a strong indication that the fraud store has plenty of customers that trust 16Shop enough to jump at every opportunity it provides to steal sensitive information from widespread services.
ZeroFOX says that the kit has the same base code as the others, and the template mimics the legitimate Cash App site and login workflow as closely as possible.
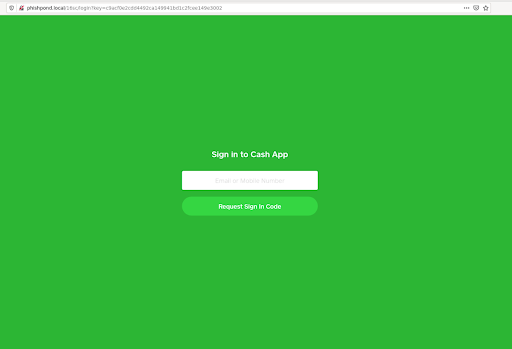
Getting victims to the phishing page is done through emails and SMS messages that alert on a security issue that led to locking the Cash App account.
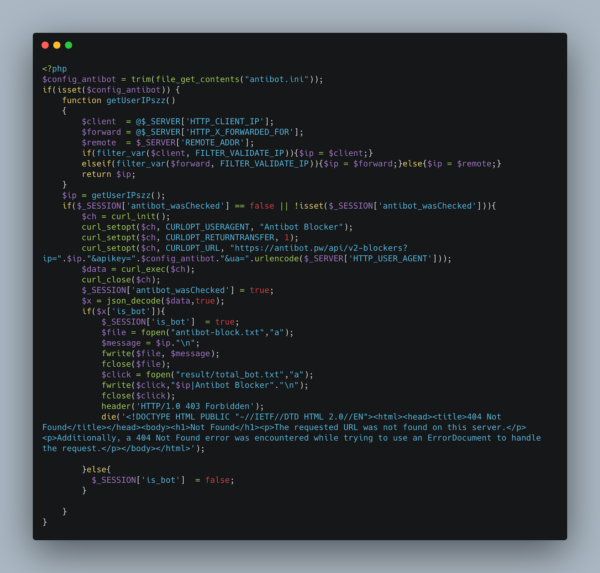
A click on the fraudulent link triggers a series of checks before loading the phishing page. The visitor’s IP address, their user agent, and ISP details are collected and processed to determine an association with an automated action (security checks, web crawlers) or a potential victim.
DevThe defenses against bots and indexing activity are present in the Cash App phishing kit as in the other 16Shop kits. The image below shows how the PHP code calls the antibot service, which provides blocking controls for bots and web crawlers.
If the victim takes the bait and provides their email address only to see a security notification about unusual activity that led to locking the account.
To regain access, the victim has to provide sensitive details “to confirm identity.” This includes the following:
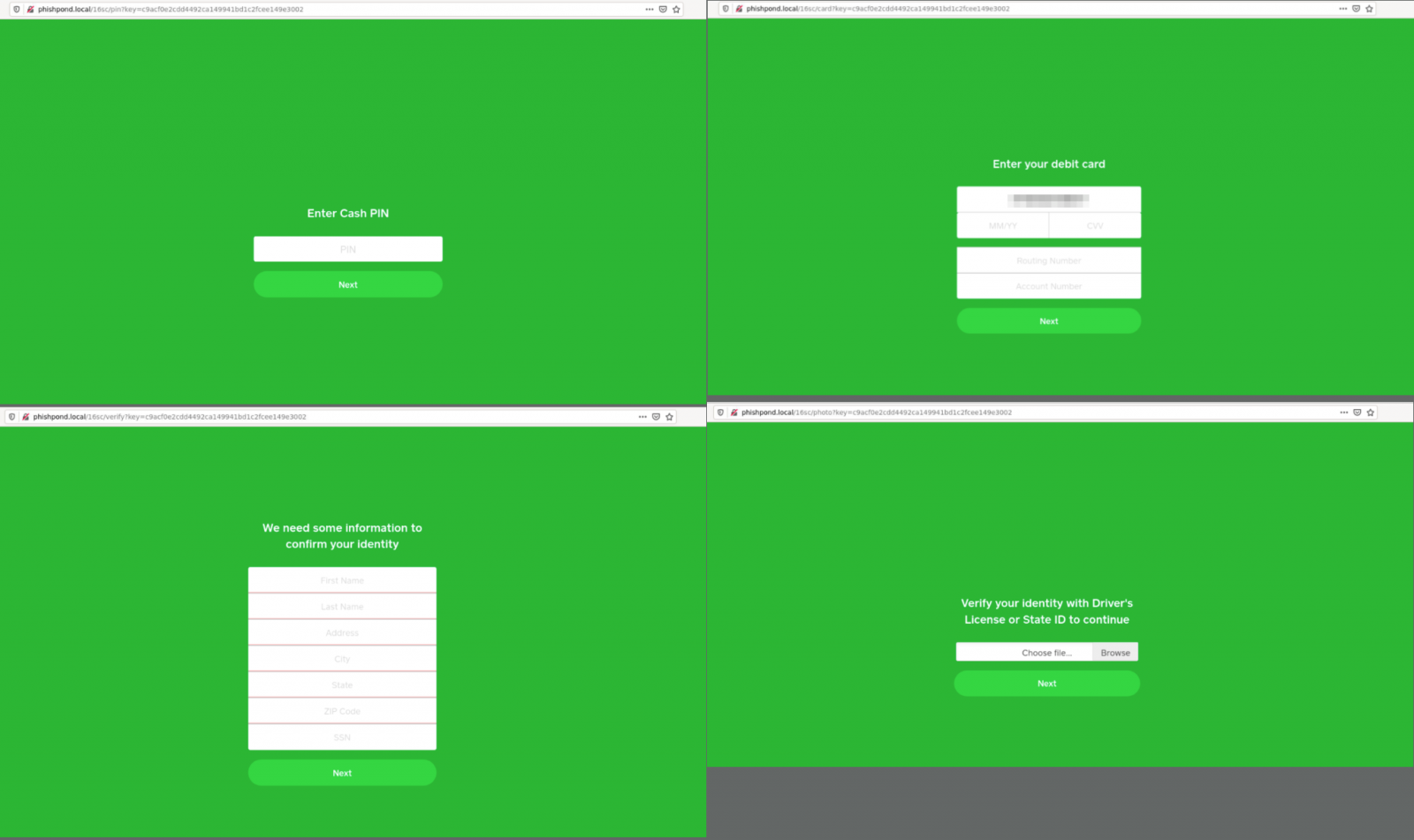
The 16Shop phishing platform appeals to low-skilled cybercriminals looking for an easy and quick way to collect sensitive accounts, which they can sell on underground forums. They get to configure the kit straight from the store with parameters for the phishing URL, defenses against security scans, and where to receive the collected data.
Details about the identity of its developer have been published in the past, based on his online trails. They all point to an Indonesian named Riswanda Noor Saputra, who has a history in defacing websites, developing other phishing kits, and releasing hacking tools.
An error from the author of the Cash App phishing kit seems to confirm the same name, ZeroFOX researchers discovered. After studying the code, they found that when the alert about unusual account activity pops up the email address of the developer is present, hidden behind the dialog.
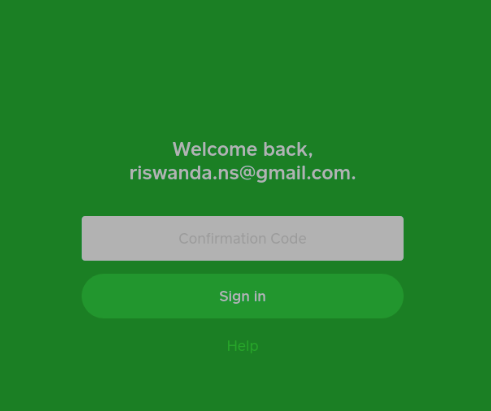
Researchers at Lookout followed the trail of opsec mistakes the 16Shop developer made and discovered that he won a website design competition in 2017. They concluded that Riswanda is either very good at inventing and maintaining a fake identity or he does a bad job protecting his real one.
A look at Riswanda’s social media activity reveals that he likes to display his wealth to the world and also posts details about upcoming updates and new kits. In the image below, he shows the development of the 16 Shop American Express kit.
Also Read: The 3 Main Benefits Of PDPA For Your Business