KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Two Android apps available on the Google Play store have been found to contain malware this week.
These apps are called ‘Smart TV remote’ and ‘Halloween Coloring’, with the former having been downloaded at least 1,000 times.
Also Read: Management Training PDF for Effective Managers and Leaders
This week, Tatyana Shishkova, Android malware analyst at Kaspersky disclosed the names of two Google Play apps that are laced with Joker malware.
At least one of these apps, ‘Smart TV remote’ has been installed over 1,000 times thus far since its publication on October 29th.
According to Shishkova, these apps are trojanized with the Joker malware:
As previously reported by BleepingComputer, the threat actors behind the Joker malware hide malicious code in seemingly benign apps and publish these to official app stores. Earlier this year, over 500,000 Huawei Android devices were found to be infected with Joker.
Also Read: PDPA Laws And Regulations; A Systematic Guidelines In Singapore
The malware is known to subscribe users to premium mobile services without their consent or knowledge.
To better analyze the malicious code, BleepingComputer obtained the Android apps and decompiled these APKs.
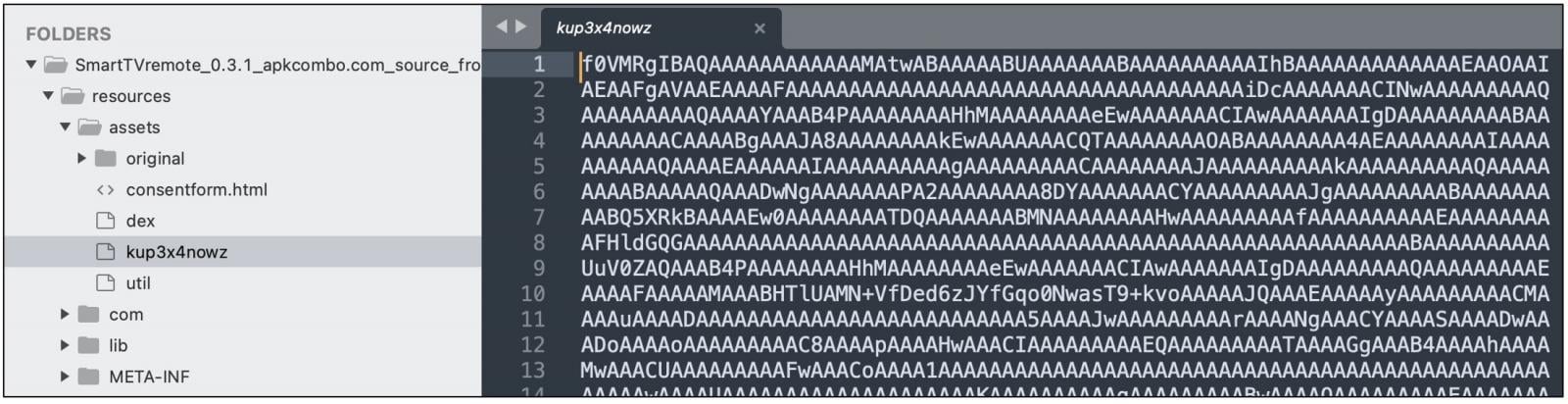
As also confirmed by Shishkova, the malicious code exists in the “resources/assets/kup3x4nowz” file within the Smart TV remote app. For the Halloween Coloring app, an identical file named “q7y4prmugi” exists at the same location.
These files contain base64 code, shown below, packing a Linux ELF binary:
This ELF binary further downloads second-stage payload hosted on an Amazon AWS instance. The URLs contained in the ELFs to second-stage payload are:Smart TV remote app: https://50egvllxk3.s3.eu-west-3.amazonaws[.]com/yr41ajkdp5
Halloween Coloring app: https://nwki8auofv.s3.sa-east-1.amazonaws[.]com/vl39sbv02d
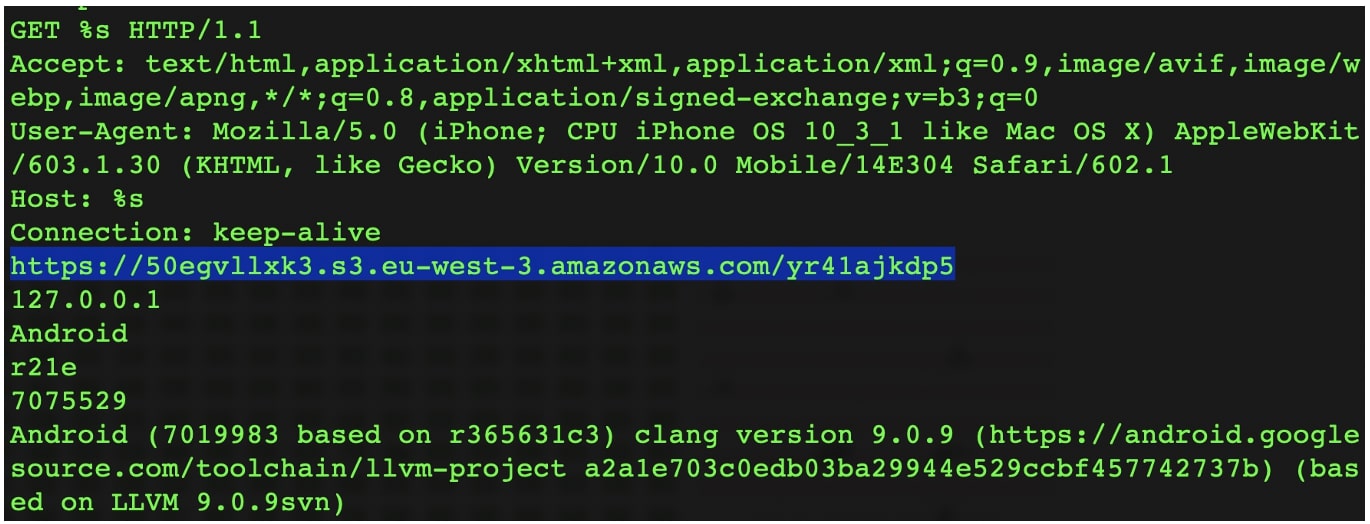
As checked by BleepingComputer, these files yr41ajkdp5 and vl39sbv02d being XOR-encrypted themselves, are not detected by any of the leading antivirus engines thus far.
Decoding these files with an XOR key ‘0x40’ however, produces APK archives. In essence, the quasi-benign ‘Smart TV remote’ and ‘Halloween Coloring’ apps are a front for downloading malicious apps onto your Android devices.
Last month, malicious “photo editor” apps were also caught sitting on the Google Play store by Shishkova and Maxime Ingrao, a security researcher at mobile payments cybersecurity firm Evina.
BleepingComputer has reported the malicious ‘Smart TV remote’ and ‘Halloween Coloring’ apps to Google Play prior to publishing.
It is plausible, Google Play Protect might eventually catch these apps and offer automatic protection to affected users, despite the initial miss leading to the apps’ publication on Play store.
“Google Play Protect checks apps when you install them. It also periodically scans your device. If it finds a potentially harmful app, it might send you a notification,… disable the app until you uninstall it, [or] remove the app automatically,” state Google’s official docs.
In the meantime, users who have installed either of these apps should uninstall the app immediately, clean up their smartphone, and check for any unauthorized subscriptions or billing activity initiated from their accounts.
Update 11 Nov 13:14 ET: A Google spokesperson told BleepingComputer, “Both apps have been removed and the developers have been banned.”