KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Researchers at the University of Darmstadt, Brescia, CNIT, and the Secure Mobile Networking Lab, have published a paper that proves it’s possible to extract passwords and manipulate traffic on a WiFi chip by targeting a device’s Bluetooth component.
Modern consumer electronic devices such as smartphones feature SoCs with separate Bluetooth, WiFi, and LTE components, each with its own dedicated security implementation.
However, these components often share the same resources, such as the antenna or wireless spectrum.
This resource sharing aims to make the SoCs more energy-efficient and give them higher throughput and low latency in communications.
As the researchers detail in the recently published paper, it is possible to use these shared resources as bridges for launching lateral privilege escalation attacks across wireless chip boundaries.
The implications of these attacks include code execution, memory readout, and denial of service.
Also Read: Do Not Call Registry Penalty: Important Tips To Consider
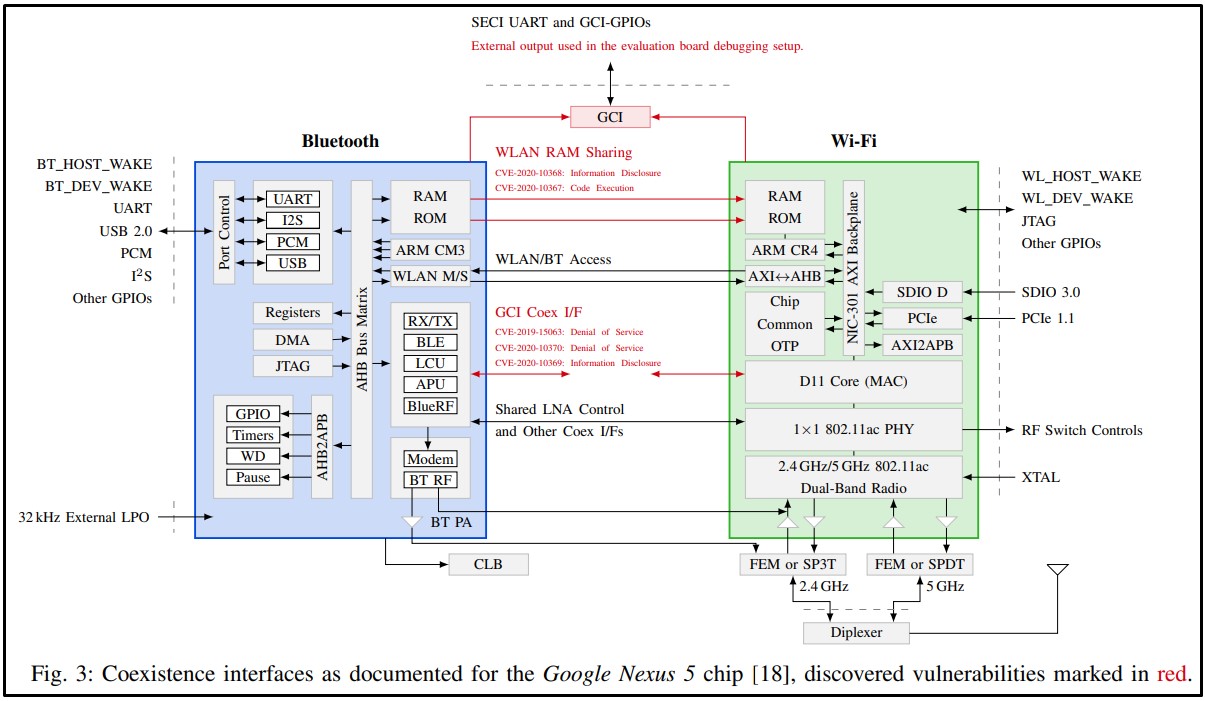
To exploit these vulnerabilities, the researchers first needed to perform code execution on either the Bluetooth or WiFi chip. While this is not very common, remote code execution vulnerabilities affecting Bluetooth and WiFi have been discovered in the past.
Once the researchers achieved code execution on one chip, they could perform lateral attacks on the device’s other chips using shared memory resources.
In their paper, the researchers explain how they could perform OTA (Over-the-Air) denial of service, code execution, extract network passwords, and read sensitive data on chipsets from Broadcom, Cypress, and Silicon Labs.
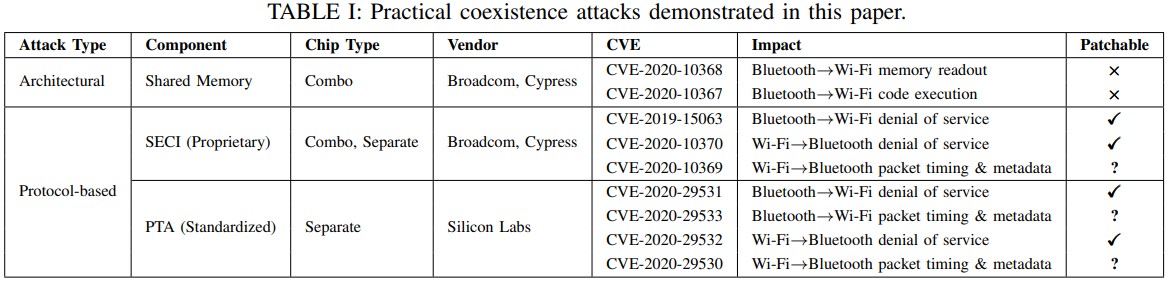
These vulnerabilities were assigned the following CVEs:
Some of the above flaws can only be fixed by a new hardware revision, so firmware updates cannot patch all the identified security problems.
Also Read: Facts About Accountability PDF That You Need to Know About
For example, flaws that rely on physical memory sharing cannot be addressed by security updates of any kind.
In other cases, mitigating security issues such as packet timing and metadata flaws would result in severe packet coordination performance drops.
The researchers looked into chips made by Broadcom, Silicon Labs, and Cypress, which are found inside billions of electronic devices.
All flaws have been responsibly reported to the chip vendors, and some have released security updates where possible.
Many though haven’t addressed the security problems, either due to no longer supporting the affected products or because a firmware patch is practically infeasible.
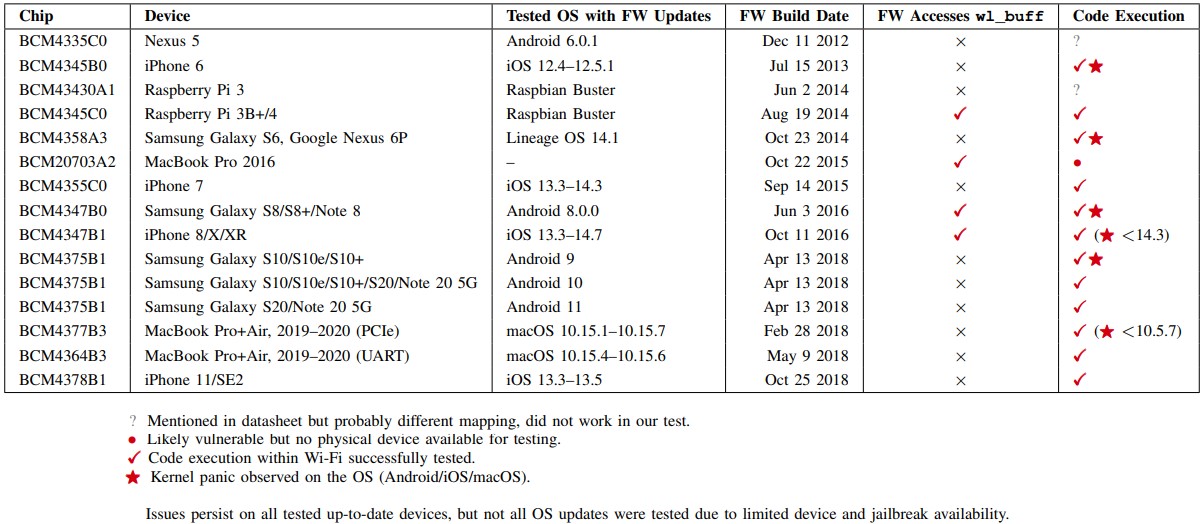
As of November 2021, more than two years after reporting the first coexistence bug, coexistence attacks, including code execution, still work on up-to-date Broadcom chips. Again, this highlights how hard these issues are to fix in practice.
Cypress released some fixes in June 2020 and updated the status in October as follows:
According to the researchers, though, fixing the identified issues has been slow and inadequate, and the most dangerous aspect of the attack remains largely unfixed.
“Over-the-air attacks via the Bluetooth chip, is not mitigated by current patches. Only the interface Bluetooth daemon→Bluetooth chip is hardened, not the shared RAM interface that enables Bluetooth chip→WiFi chip code execution. It is important to note that the daemon→chip interface was never designed to be secure against attacks.” – reads the technical paper.
“For example, the initial patch could be bypassed with a UART interface overflow (CVE-2021-22492) in the chip’s firmware until a recent patch, which was at least applied by Samsung in January 2021. Moreover, while writing to the Bluetooth RAM via this interface has been disabled on iOS devices, the iPhone 7 on iOS 14.3 would still allow another command to execute arbitrary addresses in RAM.”
Bleeping Computer has reached out to all vendors and asked for a comment on the above, and we will update this post as soon as we hear back.
In the meantime, and for as long as these hardware-related issues remain unpatched, users are advised to follow these simple protection measures:
As a final note, we would say that patching responses favor the more recent device models, so upgrading to a newer gadget that the vendor actively supports is always a good idea from the perspective of security.