KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





The new BotenaGo malware botnet has been discovered using over thirty exploits to attack millions of routers and IoT devices.
BotenaGo was written in Golang (Go), which has been exploding in popularity in recent years, with malware authors loving it for making payloads that are harder to detect and reverse engineer.
In the case of BotenaGo, only six out of 62 AV engines on VirusTotal flag the sample as malicious, and some identify it as Mirai.
Also Read: How PII Data Works In Businesses And Its Advantages
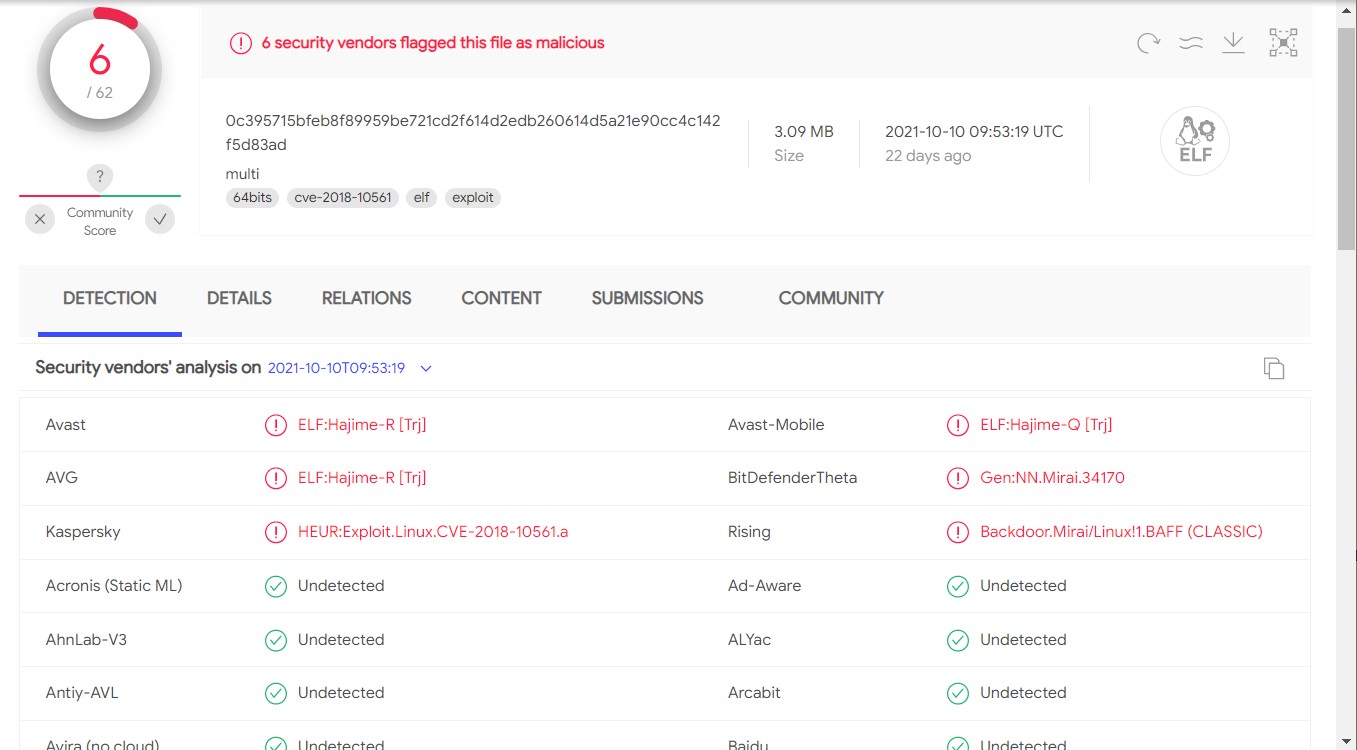
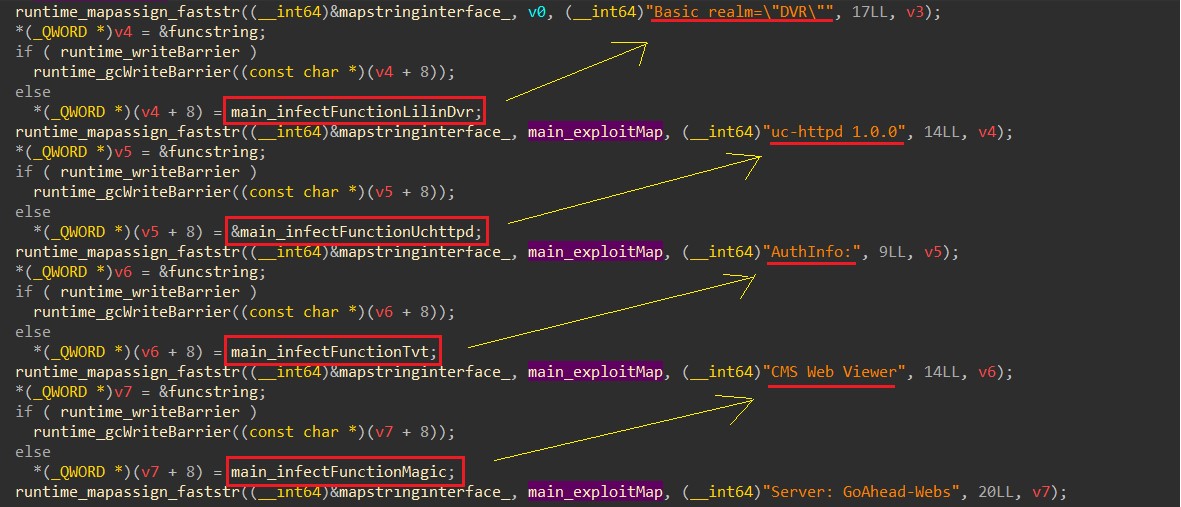
BotenaGo incorporates 33 exploits for a variety of routers, modems, and NAS devices, with some notable examples given below:
Researchers at AT&T who analyzed the new botnet found that it targets millions of devices with functions that exploit the above flaws.
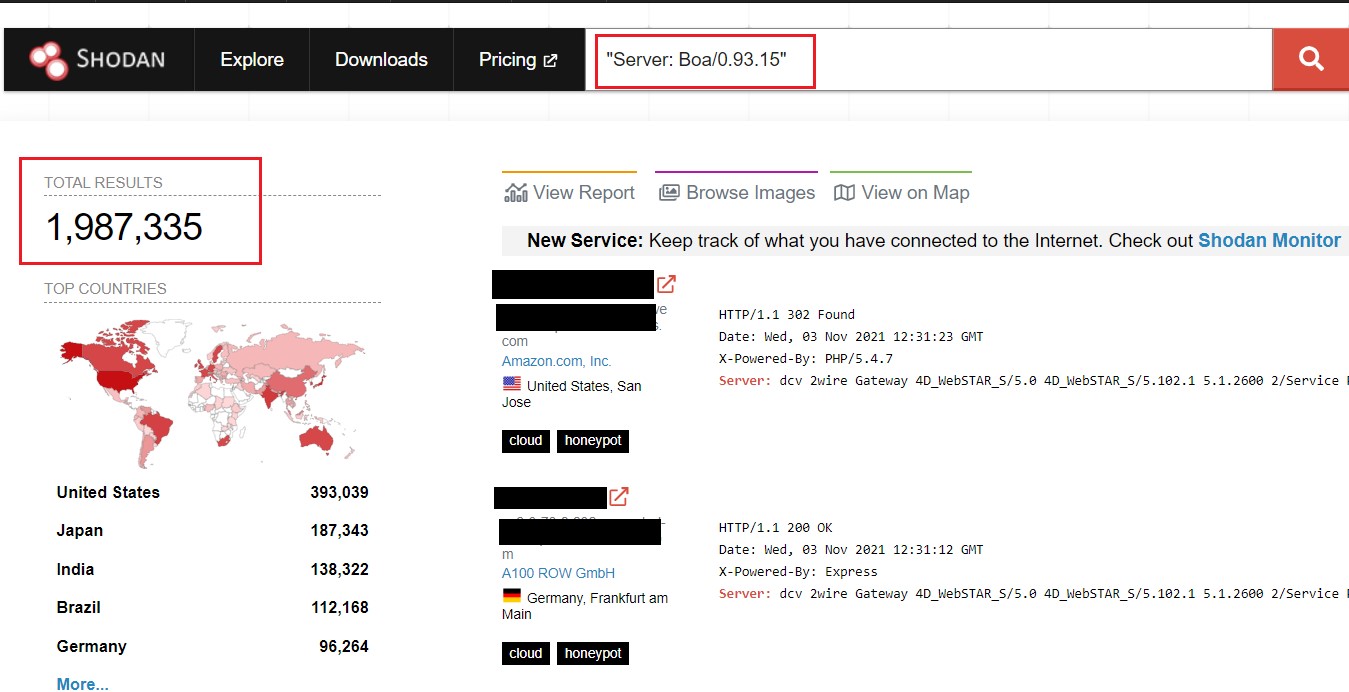
An example given is the search string for Boa, which is a discontinued open-source web server used in embedded applications and one that still returns nearly two million internet-facing devices on Shodan.
Also Read: How To Check Data Breach And How Can We Prevent It
Another notable example is the targeting of CVE-2020-10173, a command-injection flaw in Comtrend VR-3033 gateway devices, of which 250,000 are still exploitable.
When installed, the malware will listen on two ports (31412 and 19412), where it waits for an IP address to be sent to it. Once one is received, the bot will exploit each vulnerability on that IP address to gain access.
Once BotenaGo gains access, it will execute remote shell commands to recruit the device into the botnet.
Depending on which device is targeted, the malware uses different links to fetch a matching payload.
At the time of the analysis, though, there were no payloads on the hosting server, so none could be retrieved for analysis.
Furthermore, the researchers didn’t find an active C2 communication between BotenaGo and an actor-controlled server, so they give three potential explanations on how it operates:
In conclusion, the appearance of BotenaGo in the wild is unusual given its incomplete operational status, but its underlying capabilities are leaving no doubt about the intention of its authors.
Fortunately, the new botnet has been spotted early, and the indicators of compromise are already available. Still, as long as there’s a wealth of vulnerable online devices to exploit, the incentive is there for the threat actors to continue the development of BotenaGo.