KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Black Cat ransomware gang, also known as ALPHV, has confirmed they are former members of the notorious BlackMatter/DarkSide ransomware operation.
BlackCat/ALPHV is a new feature-rich ransomware operation launched in November 2021 and developed in the Rust programming language, which is unusual for ransomware infections.
The ransomware executable is highly customizable, with different encryption methods and options allowing for attacks on a wide range of corporate environments.
Also Read: December 2021 PDPC Incidents and Undertaking: Lessons from the Cases
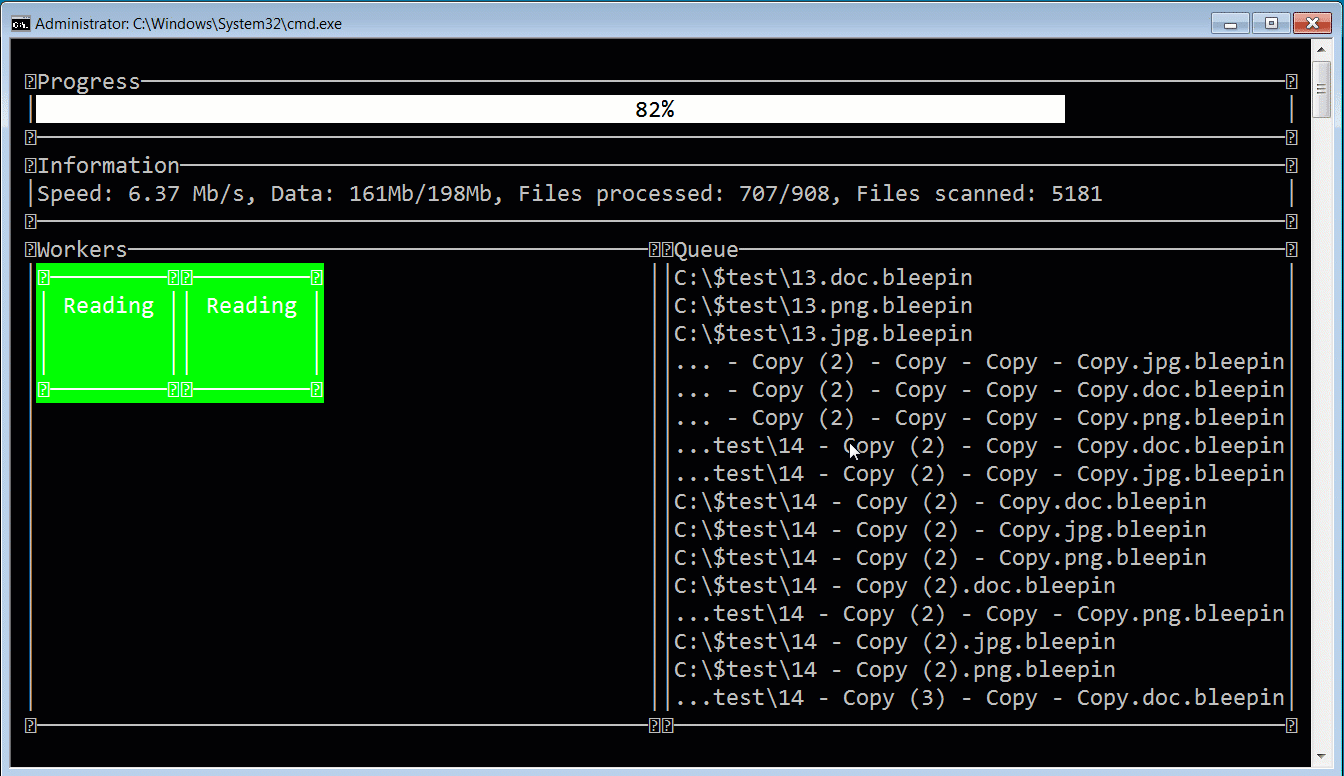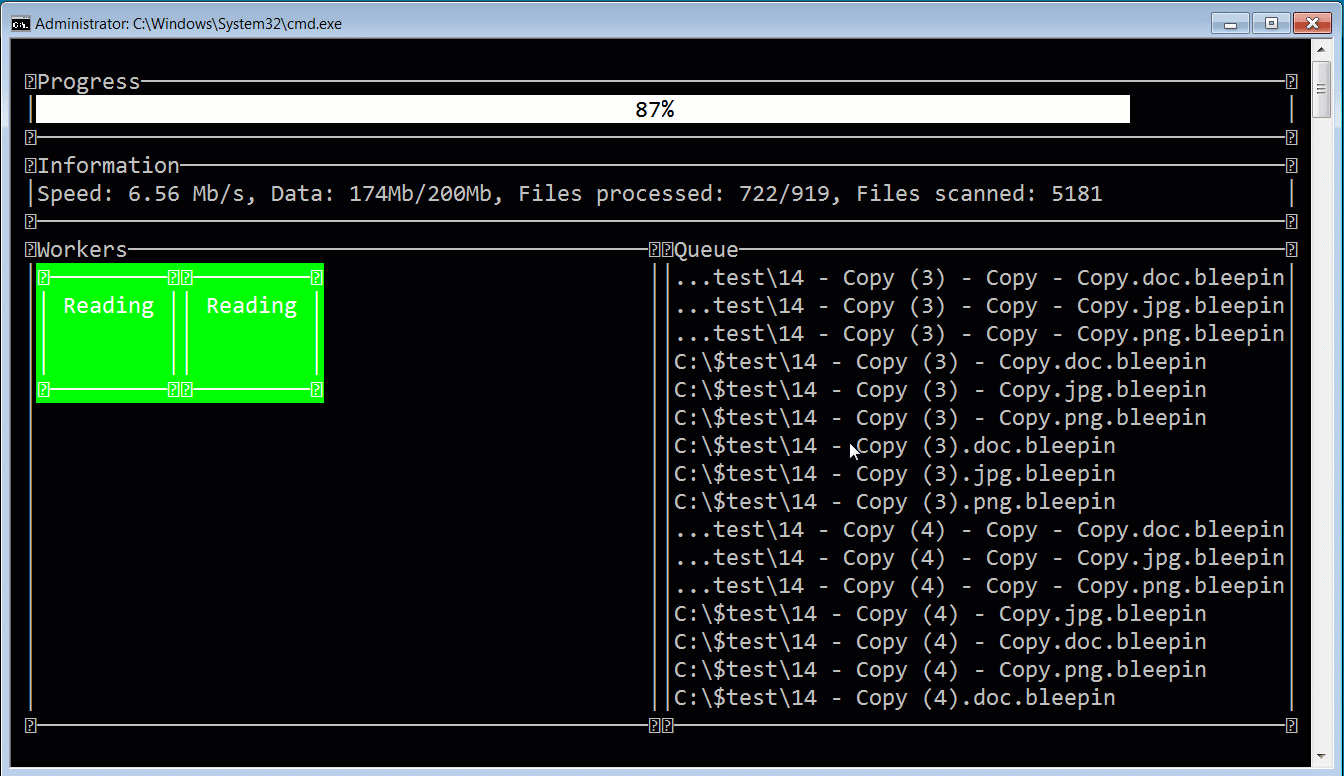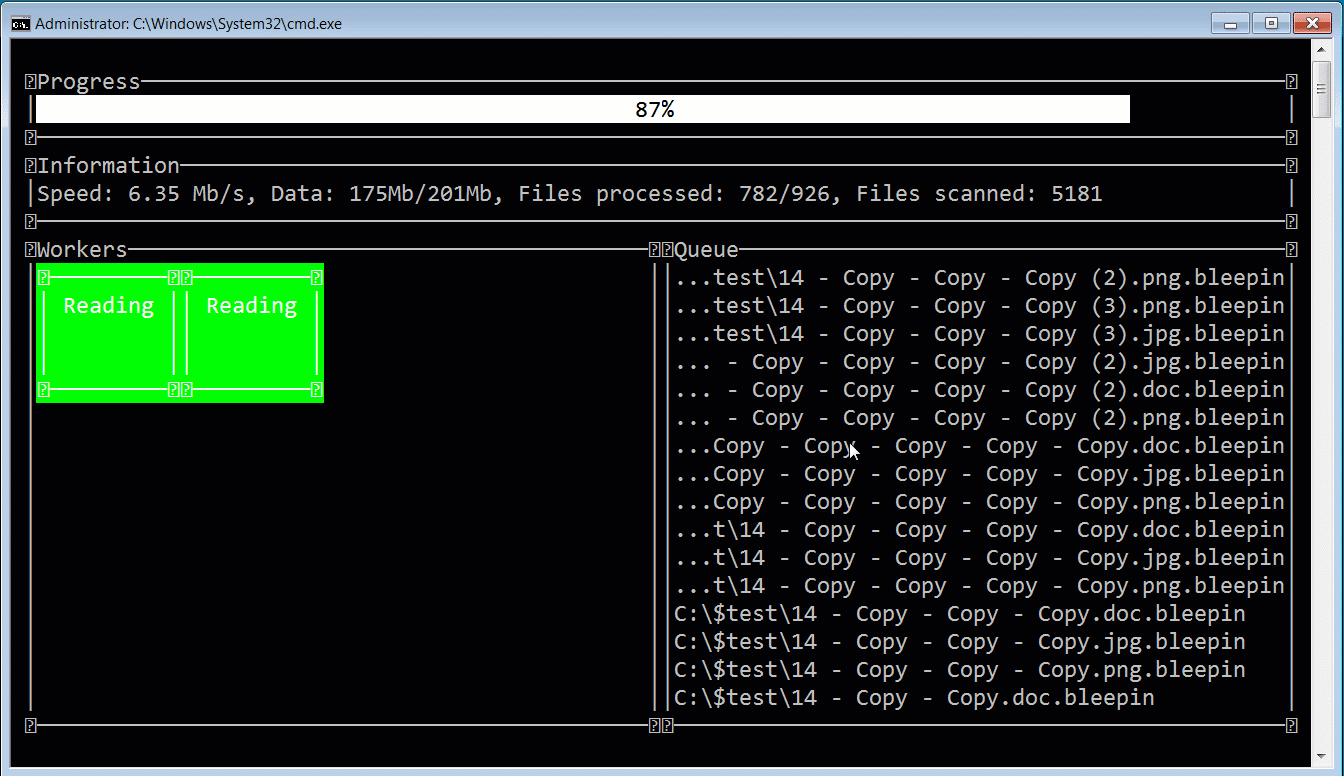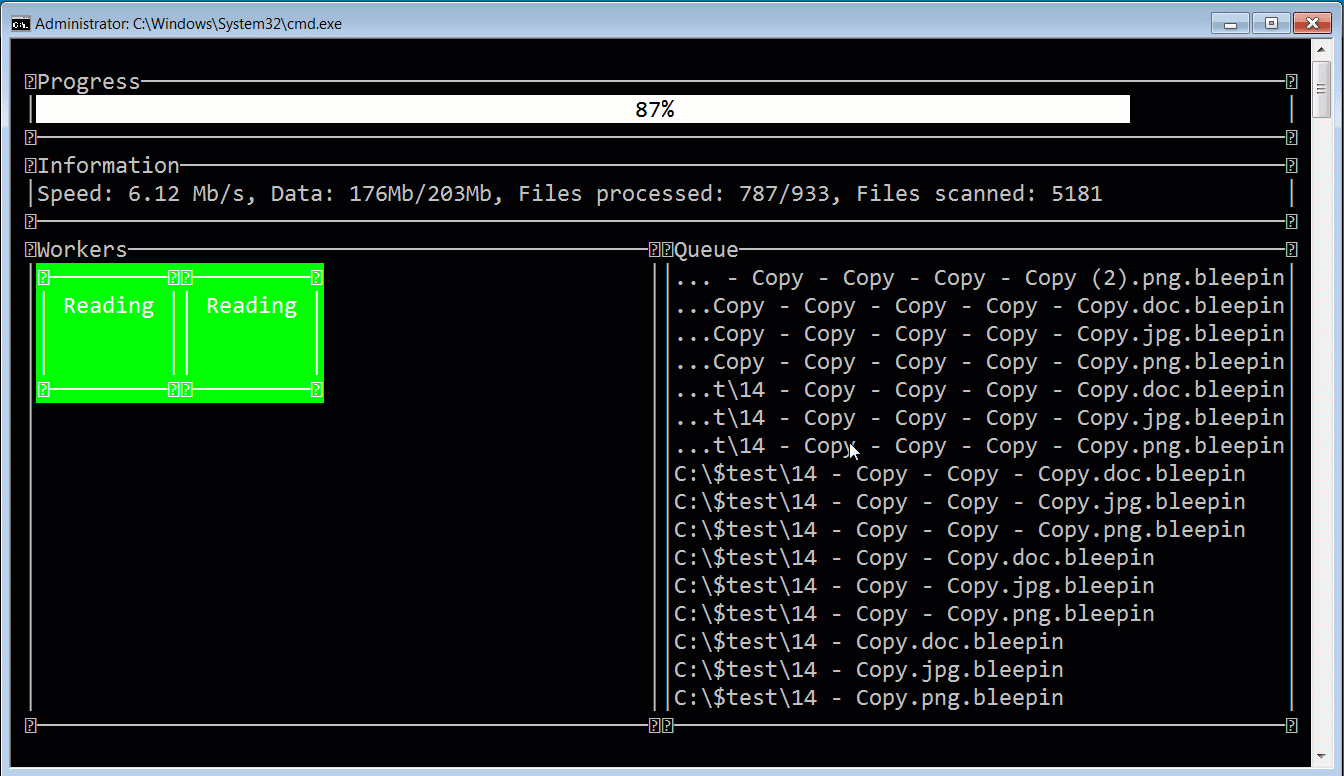
While the ransomware gang calls themselves ALPHV, security researcher MalwareHunterTeam named the ransomware BlackCat after the image of a black cat used on every victim’s Tor payment page.
Since then, the ransomware operation has been known as BlackCat when discussed in the media or by security researchers.
Many ransomware operations are run as a Ransomware-as-a-Service (RaaS), where core members are in charge of developing the ransomware infection and managing servers, while affiliates (aka “adverts”) are recruited to breach corporate networks and conduct attacks.
As part of this arrangement, the core developers earn between 10-30% of a ransom payment, while the affiliate earns the rest. The percentages change based on how much ransom revenue a particular affiliate brings to the operation.
Also Read: PDPA Compliance for the Telecommunication Sector
While there have been many RaaS operations in the past, there have been a few top-tier gangs that commonly shut down when law enforcement is breathing down their neck and then rebrand under new names.
These top-tier Ransomware-as-a-Service operations and their rebrands are:
Some believe that Conti was a rebrand of Ryuk, but sources tell BleepingComputer that they are both discrete operations run by the TrickBot Group and are not affiliated with each other.
While some affiliates tend to partner with a single RaaS operation, it is common for affiliates and penetration testers to partner with multiple gangs at once.
For example, a ransomware affiliate told BleepingComputer that they worked with Ragnar Locker, Maze, and the REvil ransomware operations simultaneously.
Since BlackCat ransomware launched in November, the representative of the LockBit ransomware gang has stated that ALPHV/BlackCat is a rebrand of DarkSide/BlackMatter.
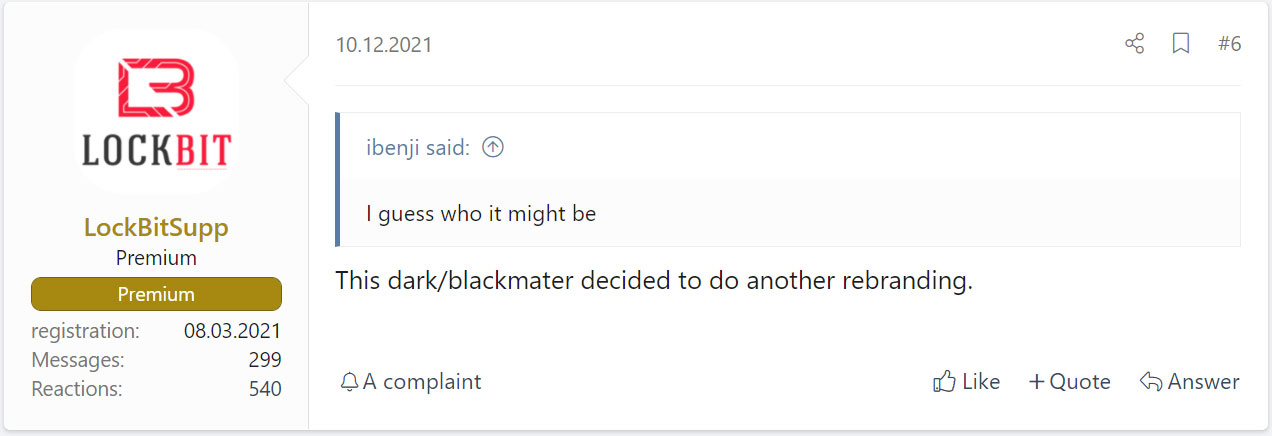
The Record published an interview with the ALPHV/BlackCat gang, who confirmed suspicions that they were affiliated with the DarkSide/BlackMatter gang.
“As adverts of darkmatter [DarkSide / BlackMatter], we suffered from the interception of victims for subsequent decryption by Emsisoft,” ALPHV told The Record, referring to the release of Emsisoft’s decryptor.
While the BlackCat ransomware operators claim that they were only DarkSide/BlackMatter affiliates who launched their own ransomware operation, some security researchers are not buying it.
Emsisoft threat analyst Brett Callow believes BlackMatter replaced their dev team after Emsisoft exploited a weakness allowing victims to recover their files for free and losing the ransomware gang millions of dollars in ransoms.
“While Alphv claim to be former DS/BM affiliates, it’s more likely that they *are* DS/BM but attempting to distance themselves from that brand due to the reputational hit it took after making an error that cost affiliates multiple millions of dollars,” Callow tweeted yesterday.
In the past, it was possible to prove that different ransomware operations were related by looking for code similarities in the encryptor’s code.
As the BlackCat encryptor has been built from scratch in the Rust programming language, Emsisoft’s Fabian Wosar told BleepingComputer that these coding similarities no longer exist.
However, Wosar said that there are similarities in the features and configuration files, supporting that it is the same group behind the BlackCat and the DarkSide/BlackMatter ransomware operations.
Regardless of whether they are just past affiliates who decided to launch their own ransomware operation or a rebrand of DarkSide/BlackMatter, they have shown to be able to pull off large corporate attacks and are rapidly amassing victims.
BlackCat is going to be a ransomware operation that all law enforcement, network defenders, and security professionals need to keep a close eye on.
Ironically, what led to the downfall of the DarkSide/BlackMatter operations may ultimately be what causes a quick demise for BlackCat/ALPHV.
After DarkSide attacked the Colonial Pipeline, the largest fuel pipeline in the United States, it began to feel the full pressure of international law enforcement and the US government.
This pressure continued after they rebranded as BlackMatter, with law enforcement seizing their servers and causing them to shut down again.
What may have thrust the BlackCat ransomware into the spotlight is ironically another attack on oil suppliers and distribution companies, leading to supply chain issues.
This week, BlackCat attacked Oiltanking, a German petrol distributor, and Mabanaft GmbH, an oil supplier.
These attacks once again affected the fuel supply chain and caused gas shortages.
The BlackCat operators, though, told The Record that they could not control who their affiliates attack and ban those that are non-compliant with the gang’s policies. These policies state that affiliates should not target government agencies, healthcare, or educational entities.
However, it seems that the Darkside gang didn’t learn from their previous mistakes and once again attacked critical infrastructure, which will likely place them firmly in the crosshairs of law enforcement.