KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The BlackCat ransomware group, aka ALPHV, has claimed responsibility for the recent cyber attack on Swissport that caused flight delays and service disruptions.
The €3 billion revenue firm, Swissport, has a presence across 310 airports in 50 countries and provides cargo handling, maintenance, cleaning, and lounge hospitality services.
BlackCat has now been seen by BleepingComputer to leak a minuscule set of terabytes of data supposedly obtained from the recent ransomware attack.
Also Read: 5 Self Assessment Tools To Find The Right Professional Fit
As reported by BleepingComputer, the cargo and hospitality services giant had earlier disclosed a ransomware attack on its systems.
Today, BlackCat (ALPHV) ransomware group has posted a small set of sample files that the group claims to have obtained from Swissport.
The threat actor has announced they are willing to sell the entire 1.6 TB “data dump” to a prospective buyer:

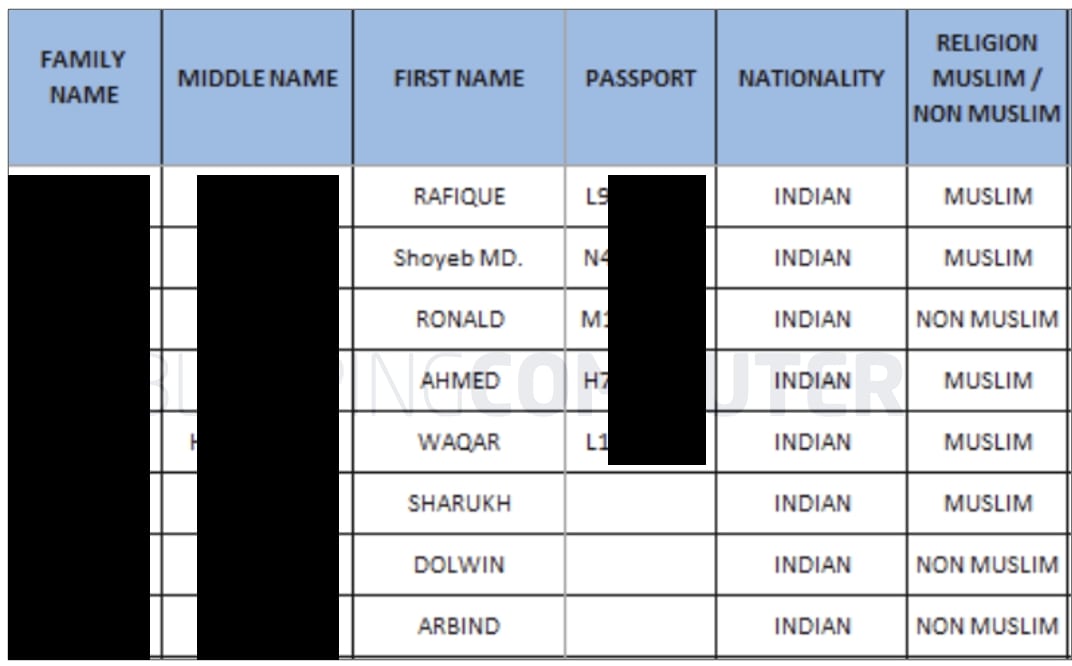
The data leak page seen by BleepingComputer today contains images of passports, internal business memos, and what appear to be details of job candidates, such as their:
BleepingComputer has reached out to Swissport to better understand what this data represents, notably the flag indicator recording the religion of job candidates:
Also Read: Website Ownership Laws: Your Rights And What These Protect
With its 66,000 employees worldwide, Swissport handles 282 million passengers and 4.8 million tons of cargo every year, making it a vital link in the global aviation travel industry chain.
As such, while the cyberattack on Swissport was “largely contained” with systems fully cleaned and restored, questions remain as to what happens to sensitive data that threat actors may have gotten their hands on.
Dubbed the “most sophisticated” ransomware group of 2021, BlackCat ransomware group emerged after BlackMatter’s shut down by law enforcement.
This month, BlackCat members confirmed they are indeed linked to the BlackMatter/DarkSide operation.
While the ransomware gang calls themselves ALPHV, security researcher MalwareHunterTeam previously named the ransomware BlackCat after the group used the image of a black cat on every victim’s Tor payment page. Since then, the ransomware operation has been known as BlackCat when discussed in the media or by security researchers.
BleepingComputer is aware of multiple victims targeted by this ransomware gang since November 2021 from numerous countries, including the USA, Australia, and India.
Ransom demands typically range between $400,000 to $3 million payable in Bitcoin or Monero. Victims paying in bitcoin incur an additional 15% fee on top of the demanded ransom.
As an additional extortion method, the BlackCat threat actors threaten to DDoS victims until they pay a ransom.
Overall, this is a highly sophisticated ransomware operation with the threat actors clearly considering all aspects of attacks.