KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Australian Cyber Security Centre (ACSC) warns of an increase of LockBit 2.0 ransomware attacks against Australian organizations starting July 2021.
“ACSC has observed an increase in reporting of LockBit 2.0 ransomware incidents in Australia,” Australia’s cybersecurity agency said in a security alert issued on Thursday.
According to the agency, LockBit victims also report threats of having data stolen during the attacks leaked online, a known and popular tactic among ransomware gangs to coerce their targets into paying the ransoms.
Also Read: 4 Reasons to Outsource Penetration Testing Services
“The majority of victims known to the ACSC have been reported after July 2021, indicating a sharp and significant increase in domestic victims in comparison to other tracked ransomware variants,” the ACSC added.https://www.ad-sandbox.com/static/html/sandbox.html
“The ACSC has observed LockBit affiliates successfully deploying ransomware on corporate systems in a variety of sectors including professional services, construction, manufacturing, retail and food.”
The agency also published a ransomware profile with additional information on the LockBit group, including initial access indicators, targeted sectors, and mitigation measures.
It added that these threat actors are opportunistic and could target organizations from any industry sector. Therefore, not being included in the list of already targeted sectors does not necessarily indicate LockBit’s target won’t switch to other industries.
The ACSC provides mitigations focused on LockBit TTPs (Tactics, Techniques, and Procedures), which include:
Organizations affected by these escalating ransomware attacks or who need assistance are advised to reach out using ACSC’s 1300 CYBER1 hotline.
The LockBit ransomware gang started operating in September 2019 as a ransomware-as-a-service (RaaS), recruiting threat actors to breach networks and encrypt devices.
Since its launch, LockBit has been very active, with gang representatives promoting the RaaS and providing support on various Russian-language hacking forums.
LockBit announced the LockBit 2.0 RaaS in June 2021 on their data leak site after ransomware topics were banned on cybercrime forums [1, 2].
While the alert issued by the Australian cybersecurity agency would imply that LockBit has hit never before seen levels of activity, the ransomware gang is just ramping up their engines again following a slowdown in attacks since January 2021, as shown by the number of ID Ransomware submissions.
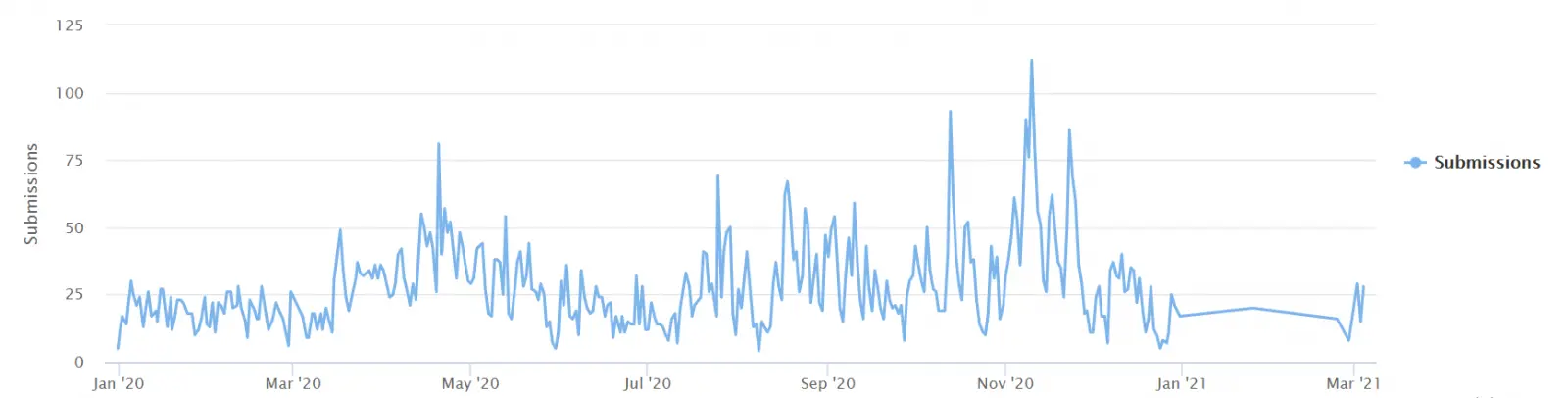
This relaunch came together with redesigned Tor sites and advanced features, including the automatic encryption of devices across Windows domains using Active Directory group policies.
With LockBit 2.0, the gang is also attempting to remove the middlemen by recruiting insiders who would provide them with access to corporate networks via Remote Desktop Protocol (RDP) and Virtual Private Network (VPN).
In related news, the ACSC and the FBI also warned in May of ongoing and escalating Avaddon ransomware attacks targeting organizations from an extensive array of sectors worldwide.
One month later, the Avaddon ransomware gang shut down operations and released decryption keys for their victims to BleepingComputer.