KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







As more and more networks are implementing Resource Public Key Infrastructure (RPKI) validation and signing of their BGP routes—to protect themselves against route hijacks and leaks, what should happen in case the critical RPKI goes down?
This is the thought process behind the latest announcement from the American Registry for Internet Numbers (ARIN), which operates critical RPKI infrastructure relied on by many.
ARIN plans on performing unannounced maintenance of its RPKI, sometime in July, for about thirty minutes to check if networks are adhering to BGP best practices.
RPKI is a cryptographic framework designed to secure the Internet’s routing infrastructure, primarily Border Gateway Protocol (BGP).
Last month, as reported by BleepingComputer, one of America’s largest broadband providers, Comcast implemented RPKI on its network to block BGP hijacking attacks and leaks.
In April this year, a major BGP leak had disrupted thousands of networks globally, prompting the need for networks to strengthen BGP route security.
This week, ARIN announced that they plan on taking down their RPKI by surprise, for about 30 minutes, sometime in July this year.
The rationale behind this drill is that, should ARIN’s critical RPKI, which is relied on by many, ever face disruptions or outages, networks should be prepared to fall back to routing on unvalidated announcements.
This is one of the many best practices, described in RFC 7115:
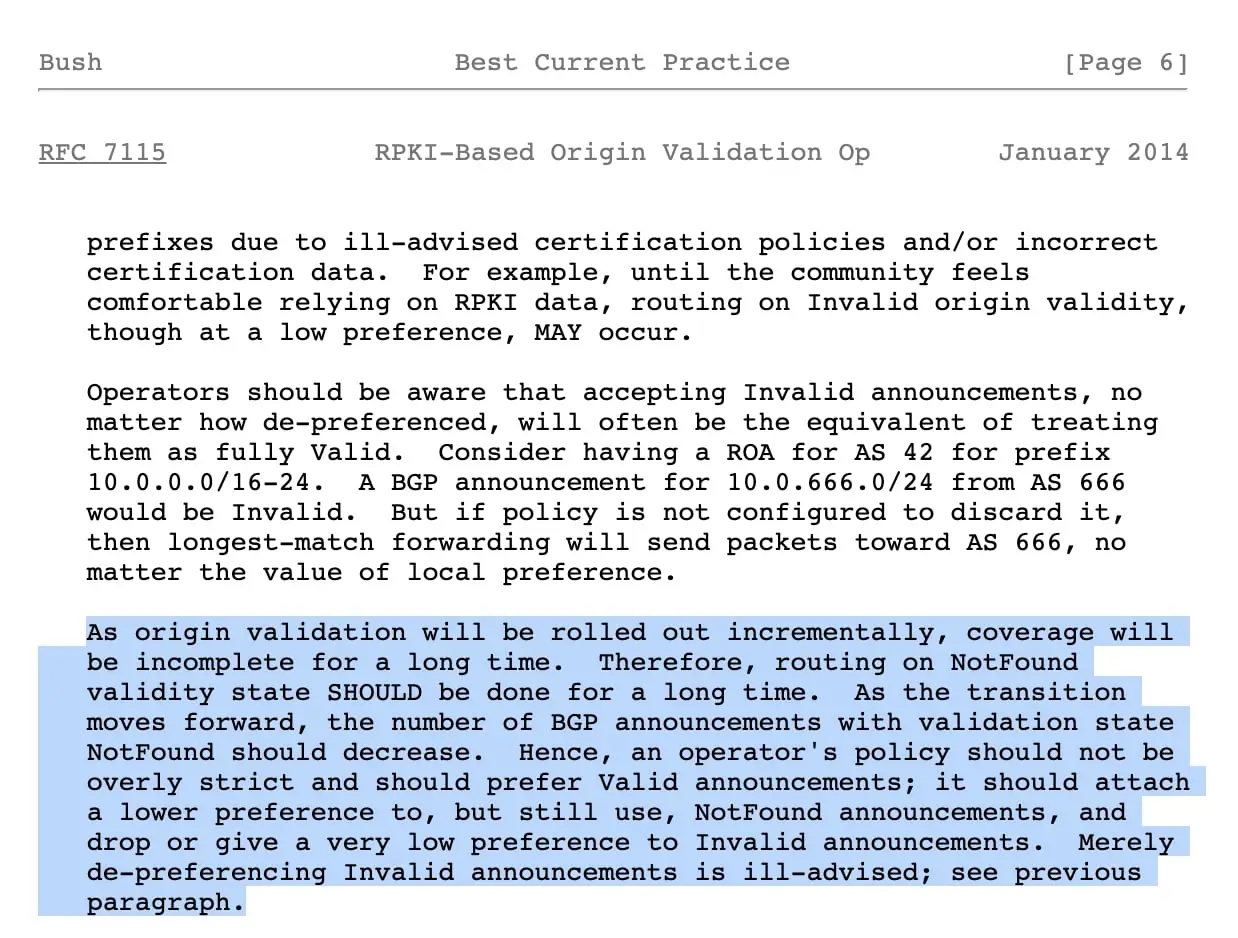
“We want to ensure that ARIN and the greater RPKI community are prepared in the unlikely event that access to ARIN’s RPKI repository becomes unavailable.”
Also Read: The 5 Phases of Penetration Testing You Should Know
“To that end, we encourage operators utilizing ARIN’s RPKI repository data to follow the best practices as described in RFC 7115 / BCP 185 – specifically falling back to routing on unvalidated announcements (i.e. NotFound validity state) in the absence of RPKI data availability,” says Brad Gorman, Senior Product Owner, Routing Security at ARIN.
As such, organizations that rely on ARIN’s RPKI route classification should review their operational model before next month, which is when the surprise maintenance will occur.
ARIN is one of the five Regional Internet Registries (RIRs) making the RPKI work:

RPKI is a cryptographic framework designed to secure BGP, the internet’s routing infrastructure, and it works by signing records that associate a route with an originating AS number.
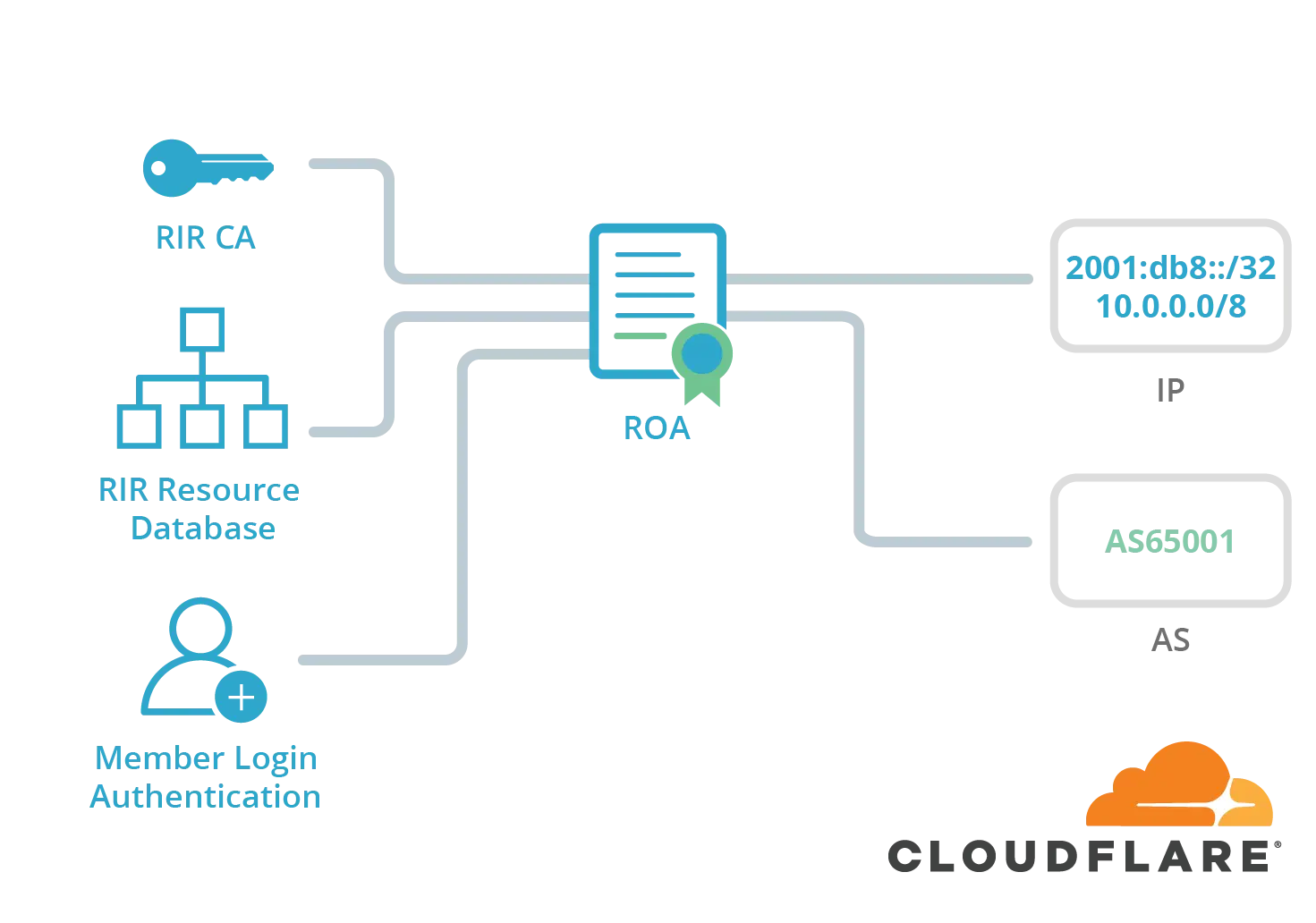
RIRs, like ARIN, provide a way for members to take an IP-ASN pair and sign an ROA (Route Origin Authorization) record.
An ROA is a digitally signed object that, as a part of the RPKI system, enables anyone to verify whether an IP address block holder has authorized an AS (Autonomous System) to originate routes to one or more prefixes within that address block:
As retired Cloudflare engineer, Martin Levy explains it himself:
“Because any route can be originated and announced by any random network, independent of its rights to announce that route, there needs to be an out-of-band method to help BGP manage which network can announce which route,” says Levy.
“That system exists today. It’s part of the IRR (Internet Routing Registry) system.”
“Many registries exist, some run by networks, some by RIRs (Regional Internet Registries) and the grand daddy of IRRs, Merit’s RADB service. This service provides a collective method to allow one network to filter another network’s routes,” Levy further explains.
Also Read: Got Hacked? Here Are 5 Ways to Handle Data Breaches
Last year, IBM suffered a global outage due to “incorrect” BGP routing, as reported by BleepingComputer. For those interested, the report also goes over the basics of BGP routing and hijacking.
As more and more networks adopt RPKI, this move by ARIN encourages networks and AS owners to investigate and become ready with a fail-safe plan.