KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The BrazKing Android banking trojan has returned with dynamic banking overlays and a new implementation trick that enables it to operate without requesting risky permissions.
A new malware sample was analyzed by IBM Trusteer researchers who found it outside the Play Store, on sites where people end up after receiving smishing (SMS) messages.
These HTTPS sites warn the prospective victim that they are using an outdated Android version and offer an APK that will allegedly update them to the latest version.
Also Read: 5 Brief Concepts Between Data Protection Directive vs GDPR
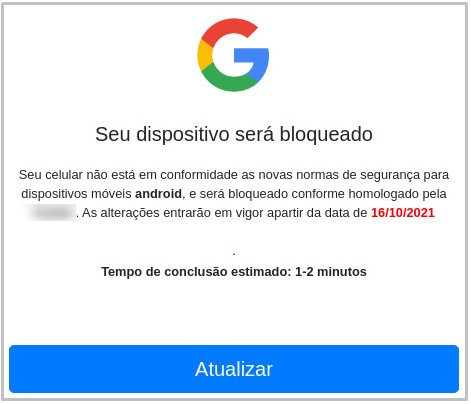
If the user approves “downloads from unknown sources,” the malware is dropped on the device and requests access to the ‘Accessibility Service’.
This permission is abused to capture screenshots and keystrokes without requesting any additional permissions that would risk raising suspicions.
More specifically, the accessibility service is used by BrazKing for the following malicious activity:
Starting on Android 11, Google has categorized the list of installed apps as sensitive information, so any malware that attempts to fetch it is flagged by Play Protect as malicious.
This is a new problem for all banking overlaying trojans that need to determine which bank apps are installed on the infected device to serve matching login screens.
BrazKing no longer uses the ‘getinstalledpackages’ API request as it used to but instead uses the screen dissection feature to view what apps are installed on the infected device.
When it comes to overlaying, BrazKing now does it without the ‘System_Alert_Window’ permission, so it can’t overlay a fake screen on top of the original app as other trojans do.
Instead, it loads the fake screen as an URL from the attacker’s server in a webview window, added from within the accessibility service. This covers the app and all its windows but doesn’t force an exit from it.
Also Read: Top 10 Best Freelance Testing Websites That Will Pay You
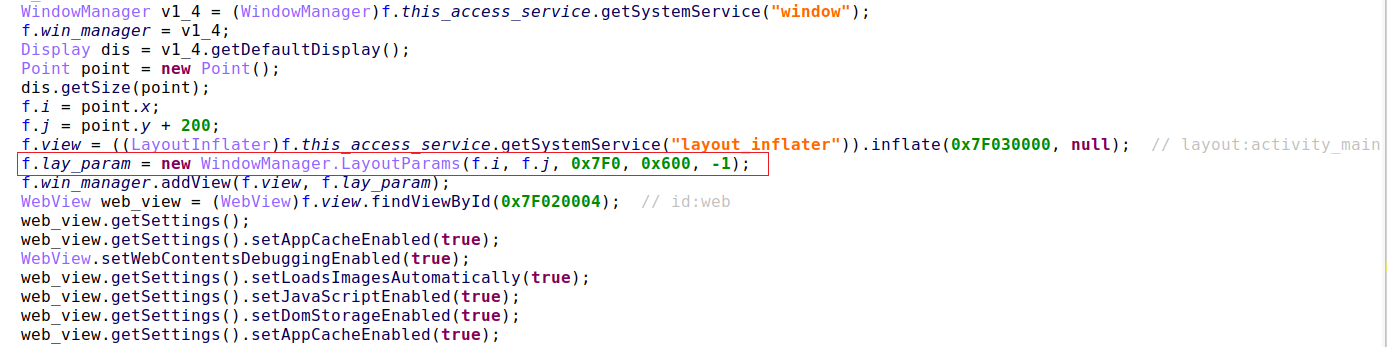
When detecting the login to an online bank, instead of displaying built-in overlays, the malware will now connect to the command and control server to receive the correct login overlay to display.
This dynamic overlay system makes it easier for the threat actors to steal credentials for a broader range of banks. Serving the overlays from the attacker’s servers also allows them to update the login screens as necessary to coincide with changes on the legitimate banking apps or sites or add support for new banks.
The new version of BrazKing protects internal resources by applying an XOR operation using a hardcoded key and then also encodes them with Base64.
Analysts can quickly reverse these steps, but they still help the malware go unnoticed when nested in the victim’s device.
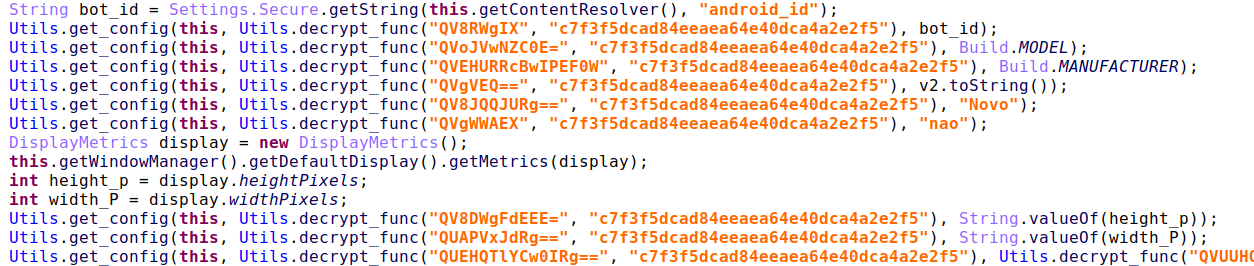
If the user attempts to delete the malware, it quickly taps on the ‘Back’ or ‘Home’ buttons to prevent the action.
The same trick is used when the user tries to open an antivirus app, hoping to scan and remove the malware within the security tool.
BrazKing’s evolution shows that malware authors quickly adapt to deliver stealthier versions of their tools as Android’s security tightens up.
The ability to snatch 2FA codes, credentials, and take screenshots without hoarding permissions makes the trojan a lot more potent than it used to be, so be very careful with APK downloads outside the Play Store.
According to the IBM report, BrazKing appears to be operated by local threat groups, as it is circulating on Portuguese-speaking websites.