




Android apps with over 250 million downloads are still susceptible to a severe vulnerability in a Google library that was patched in August 2020.
In August, mobile app security company Oversecured discovered a vulnerability in the Google Play Core Library that allowed malicious applications to execute code in legitimate apps.
These malicious executables would then run under the legitimate app’s security permissions, allowing it to monitor and steal data being entered into the app or transmitted by it.
This vulnerable library is used to update an app’s components at runtime through the Google API. This library is used by many popular apps, including Chrome, Edge, Facebook, Instagram, WhatsApp, and Snapchat.
Tracked as CVE-2020-8913, the vulnerability was assigned an 8.8 (High) rating and was fixed by Google in Google Play Core Library version 1.7.2.
Researchers from Check Point Research have discovered that there are still apps with millions of installs using the vulnerable library over three months later.
Also Read: A Look at the Risk Assessment Form Singapore Government Requires
“Since the publication of this vulnerability, we started monitoring vulnerable applications. During the month of September 2020, 13% of Google Play applications analyzed by SandBlast Mobile used this library, and 8% of those apps had a vulnerable version,” Check Point Research stated in their report.
This is worrisome, as according to the researchers, the Google Play Core Library vulnerability is trivial to exploit
“All you need to do is to create a “hello world” application that calls the exported intent in the vulnerable app to push a file into the verified files folder with the file-traversal path. Then sit back and watch the magic happen,” Check Point explains.
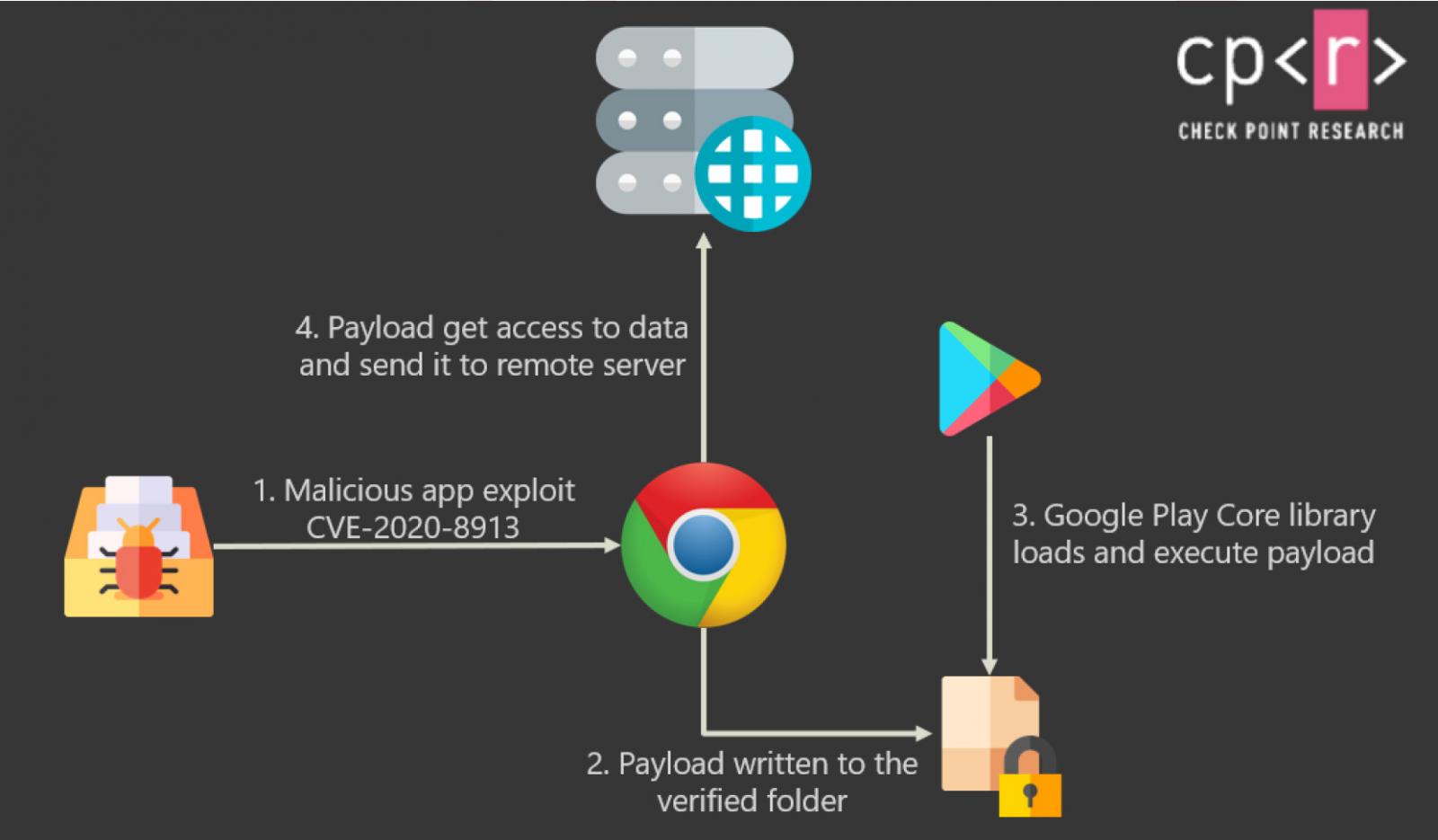
To illustrate how easy it is to exploit this vulnerability, Check Point created a video demonstrating it in action, shown below.
Below is a list of some of the vulnerable applications discovered by Check Point. As you can see, all of these apps have at least 1 million downloads, with one as high as 100 million downloads.
| App Name | Version | Download Count |
|---|---|---|
| Aloha | 2.23.0 | 1,000,000 |
| Walla! Sports | 1.8.3.1 | 100,000 |
| XRecorder | 1.4.0.3 | 100,000,000 |
| Hamal | 2.2.2.1 | 1,000,000 |
| IndiaMART | 12.7.4 | 10,000,000 |
| Edge | 45.09.4.5083 | 10,000,000 |
| Grindr | 6.32.0 | 10,000,000 |
| Yango Pro (Taximeter) | 9.56 | 5,000,000 |
| PowerDirector | 7.5.0 | 50,000,000 |
| OkCupid | 47.0.0 | 10,000,000 |
| Teams | 40.10.1.274 | 1,000,000 |
| Bumble | 5.195.1 | 10,000,000 |
As the Google Play Core Library can not be auto-updated by Google, developers must manually download a new version and update their apps with it. Their apps will continue to be vulnerable and potentially exploited by threat actors to steal data and passwords or perform malicious activity until they do.
Also Read: How to Send Mass Email Without Showing Addresses: 2 Great Workarounds
Unfortunately, even after Check Point notified each of the developers about their apps’ vulnerability, the researchers said only Viber and Booking released fixed versions.
Update 12/3/20: Moovit had released an updated version today that fixed the vulnerability and was removed from the list above.