KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Proof-of-Concept (PoC) exploits for the Apache web server zero-day surfaced on the internet revealing that the vulnerability is far more critical than originally disclosed.
These exploits show that the scope of the vulnerability transcends path traversal, allowing attackers remote code execution (RCE) abilities.
Apache remains one of the most popular web servers of choice with over a 25% market share.
Also Read: What Is PDPA And What Are The 5 Things You Should Know About
The path traversal vulnerability in Apache’s HTTP server, first reported by BleepingComputer, has actively been exploited in the wild before the Apache project was notified of the flaw in September, or had a chance to patch it.
But yesterday’s disclosure of the Apache webserver path traversal flaw, tracked as CVE-2021-41773, was followed by PoC exploits swiftly surfacing on the internet.
But, while PoC exploits were being developed and tinkered with, another discovery came to light.
Attackers can abuse Apache servers running version 2.4.49 not only to read arbitrary files but also to execute arbitrary code on the servers.
Security researcher Hacker Fantastic noted that the flaw soon turns into a Remote Code Execution (RCE) vulnerability on a Linux system if the server is configured to support CGI via mod_cgi.
Also Read: The Competency Framework: A Guide for Managers and Staff
Should an attacker be able to upload a file via a path traversal exploit, and set execute permissions on the file, they have now granted themselves the ability to execute commands with the same privileges as the Apache process.
CERT’s vulnerability analyst Will Dormann and security researcher Tim Brown have also reported success with code execution on Windows machines.
While playing with the simple PoC on his Windows server, Dormann realized that accessing an EXE via the path traversal exploit in turn launched the binary on his server, as opposed to simply dumping the contents of the EXE.
“I was not doing anything clever other than just reproducing essentially the public PoC on Windows when I saw calc.exe spawn,” says Dormann, who additionally confirmed this behavior to BleepingComputer.
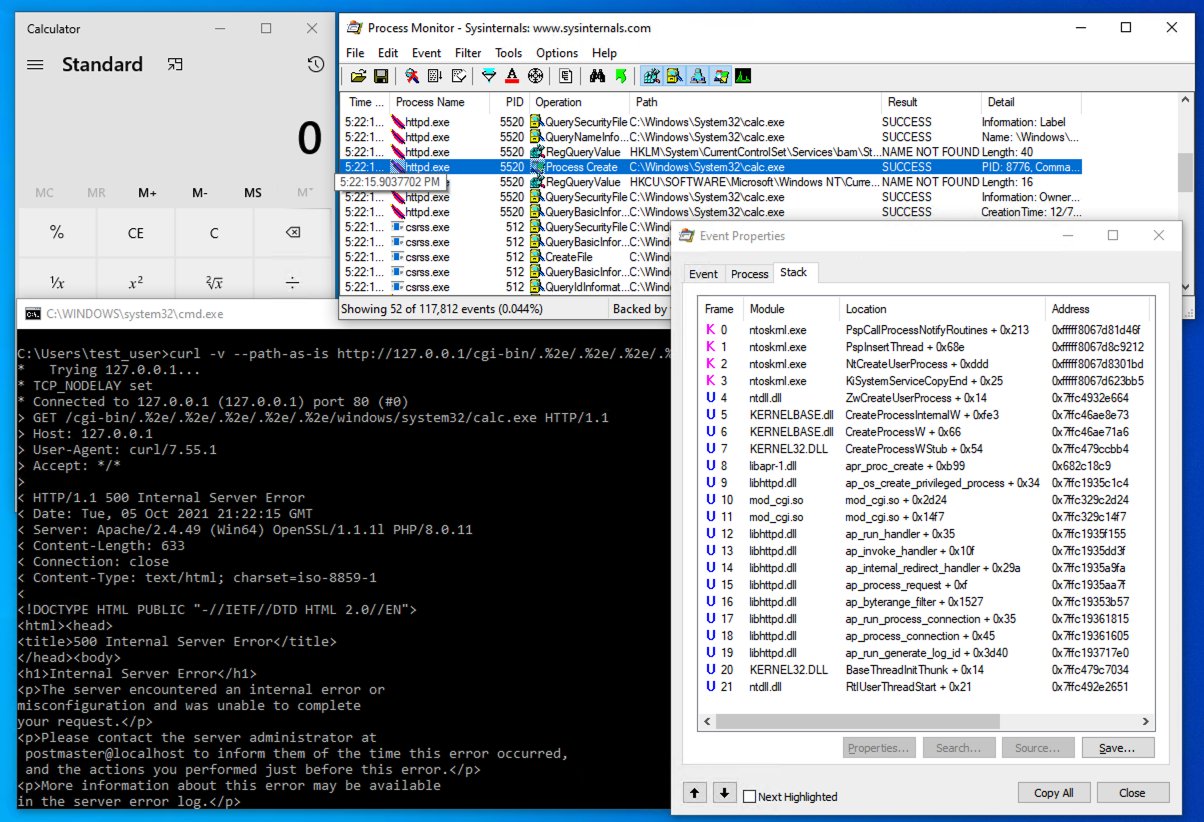
“Was CVE-2021-41773 mis-scoped when it was published?” surmised Dormann, pointing to the note in Apache’s original advisory that exploitation of the flaw would, at most, leak the source code of scripts—rather than running the scripts.
Although Shodan queries run by BleepingComputer show over 112,000 Apache servers are running the vulnerable 2.4.49 version, not all servers may be at risk.
The success of the path traversal exploits depends on a variety of factors, including if “mod-cgi” is enabled on the server, and the default “Require all denied” option is missing from the configuration.
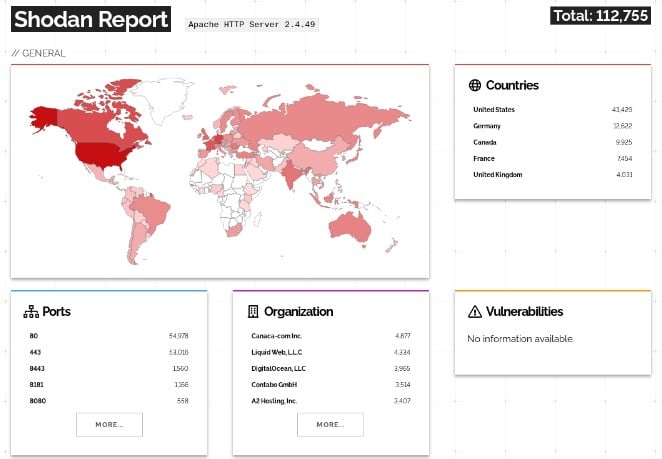
But, should all of the items in the aforementioned criteria apply, there is high potential for the vulnerability to evolve into arbitrary code execution:
“Again, Apache needs to be the vulnerable 2.4.49 version, and mod-cgi is enabled, and it needs to be missing the default Require all denied. But if both of those are true, then CVE-2021-41773 is as RCE as it gets,” explains Dormann.
Server administrators should ensure their Apache HTTP server instances are running patched versions 2.4.50 and above.
Threat intel analyst Florian Roth has provided Sigma rules to help detect an active exploit for the zero-day.