Distributed denial-of-service (DDoS) attacks started strong this year, setting new records and taking the extortion trend that started last August to the next level.
Internet security services company Akamai has already dealt with the largest known ransom DDoS (RDDoS) attack, which was also more complex than previously seen incidents of the same type.
Akamai says that in February they dealt with “three of the six biggest volumetric DDoS attacks” the company has ever recorded.
Two of these were the largest known ransom DDoS attacks and the most recent of them peaked at 800Gbps; it targeted a gambling company in Europe and was also the most complex Akamai saw since extortion DDoS started.
“Since the start of the [ransom DDoS] campaign, show-of-force attacks have grown from 200+ Gbps in August to 500+ Gbps by mid-September, then ballooned to 800+ Gbps by February 2021” – Akamai
According to Akamai, the perpetrators used a new DDoS attack vector: a networking protocol known as the Datagram Congestion Control Protocol (DCCP) or protocol 33.
Leveraging DCCP for DDoS leads to a volumetric attack and can bypass the defenses set up for the TCP and UDP traffic flows that are more commonly seen during these incidents.
Also Read: Practitioner Certificate In Personal Data Protection: Everything You Need To Know
Anti-DDoS company Radware saw the new wave of extortions hit at the end of 2020 and in the first week of January. They said that organizations threatened with DDoS attacks in August and September of 2020 received new ransom letters asking for 10 bitcoins to stop the strike.
Radware says that the organizations that received the new letters had not been disclosed to the media last year. Indications that the same actor was behind the new threats are present in the ransom note sent to the targets.
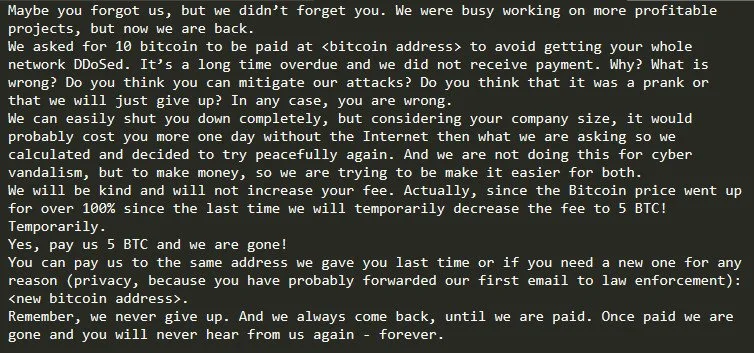
The actor started to prove they were not making empty threats just hours after sending the letters. Victims experienced more than nine hours of relentless DDoS attacks that exceeded 200Gbps and peaked at 237Gbps.
Akamai confirmed that their customers went through similar episodes, the company noting that the “2021 DDoS campaigns have become more targeted and much more persistent.”
At two organizations, Akamai saw multiple campaigns extending over several days and targeting a range of IP addresses, indicating that the attackers did their homework.
“The attackers were relentlessly looking for weaknesses in defenses to exploit, as well as trying different attack vector combinations. In one attack, the threat actors targeted nearly a dozen IPs and rotated through multiple DDoS attack vectors trying to increase the likelihood of disrupting the back-end environments” – Akamai
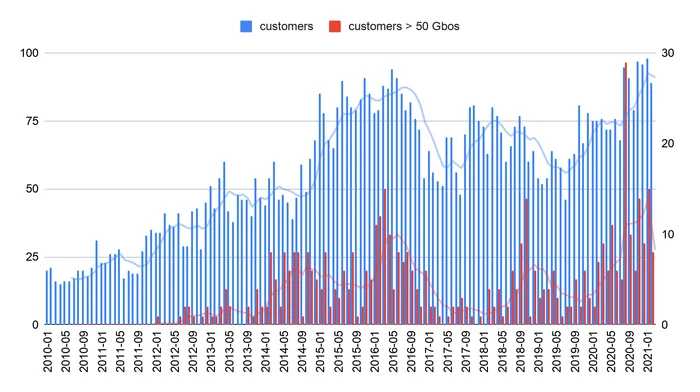
Another tendency observed this year is an increase of DDoS attacks above 50Gbps. While it may seem like much, this amount of junk data can take many services offline.
In less than three months, Akamai recorded more attacks of this magnitude than it did in the entire 2019, and their number is expected to rise significantly this year.
Also Read: The DNC Singapore: Looking At 2 Sides Better