KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A malicious campaign known as ‘Eternal Silence’ is abusing Universal Plug and Play (UPnP) turns your router into a proxy server used to launch malicious attacks while hiding the location of the threat actors.
UPnP is a connectivity protocol optionally available in most modern routers that allows other devices on a network to create port forwarding rules on a router automatically. This allows remote devices to access a particular software feature or device as necessary, with little configuration required by a user.
However, it is yet another technology that trades convenience for security, especially when the UPnP implementation is potentially vulnerable to attacks allowing remote actors to add UPnP port-forwarding entries via a device’s exposed WAN connection.
Researchers from Akamai have spotted actors abusing this vulnerability to create proxies that hide their malicious operations, calling the attack UPnProxy.
Also Read: New Data Protection Laws Australia: How Implementation Works
Out of 3,500,000 UPnP routers found online, 277,000 are vulnerable to UPnProxy, and 45,113 of them have already been infected by hackers.
Akamai’s analysts speculate that the actors attempt to exploit EternalBlue (CVE-2017-0144) and EternalRed (CVE-2017-7494) on unpatched Windows and Linux systems, respectively.
Leveraging these flaws can lead to an array of potential problems, including resource-consuming cryptominer infections, devastating worm-like attacks that quickly spread to entire corporate networks, or initial access to corporate networks.
The new rulesets defined by the hackers contain the phrase ‘galleta silenciosa’, which is Spanish for ‘silent cookie’.
{"NewProtocol": "TCP", "NewInternalPort": "445", "NewInternalClient": "192.168.10.212",
"NewPortMappingDescription": "galleta silenciosa", "NewExternalPort": "47669"}The injections attempt to expose TCP ports 139 and 445 on devices connected to the targeted router, roughly 1,700,000 machines running SMB services.
Akamai is unsure about the success rate of this campaign, but observed a systematic approach to the scans, targeting devices that utilize static ports and paths for their UPnP daemons to inject port forwards.
Akamai’s analysts speculate that the actors attempt to exploit EternalBlue (CVE-2017-0144) and EternalRed (CVE-2017-7494) on unpatched Windows and Linux systems respectively.
Leveraging these flaws can lead to an array of potential problems, including resource-consuming cryptominer infections, devastating worm-like attacks that quickly spread to entire corporate networks, or initial access to corporate networks.
“Because there is a decent possibility that (vulnerable) machines unaffected by the first round of EternalBlue and EternalRed attacks were safe only because they weren’t exposed directly to the internet. They were in a relatively safe harbor living behind the NAT,” explains Akamai’s report
“The EternalSilence attacks remove this implied protection granted by the NAT from the equation entirely, possibly exposing a whole new set of victims to the same old exploits.”
‘Eternal Silence’ is a very cunning attack because it renders the practice of network segmentation ineffective and doesn’t give any indication of what is happening to the victim.
The best way to determine if your devices have been captured is by scanning all endpoints and auditing the NAT table entries.
Also Read: Shred It Singapore For Commercial Document Destruction
There are many ways to do this, but Akamai has conveniently provided this bash script (screenshot below), which can be run against a potentially vulnerable URL.
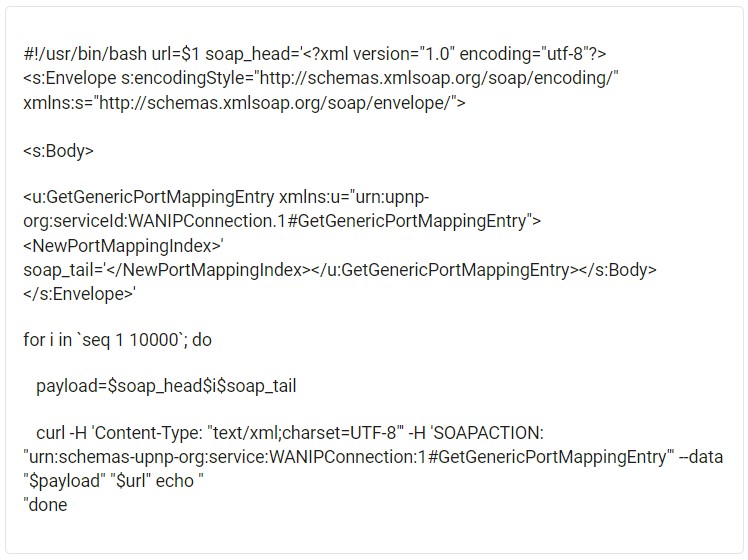
If you’ve located a device compromised with Eternal Silence, disabling UPnP won’t clear the existing NAT injections. Instead, users will need to reset or flash the device.
Also, applying the latest firmware update should be a priority as the device vendor may have addressed any UPnP implementation flaws via a security update.