KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






Hackers have set up an auction site on the dark web to sell 250,000 databases stolen from tens of thousands of breached MySQL servers.
The entire collection is seven terabytes in size and is part of a database ransom business that registered a sharp rise since October.
Back in May, BleepingComputer reported about an attacker that was stealing SQL databases from online shops and threatening victims that their data would become public if they did not pay 0.06 BTC.
Although the hacker’s website on the clear web listed only 31 databases, the number of abuse reports for the wallet left in the ransom note was above 200, indicating a much larger operation.
Researchers at Guardicore monitored the scheme through the year and noticed a sharp rise in activity since October 3.
The attacker has moved from the clear web to the dark web, creating an auction site that lists 250,000 databases from 83,000 breached servers that were exposed on the public web.
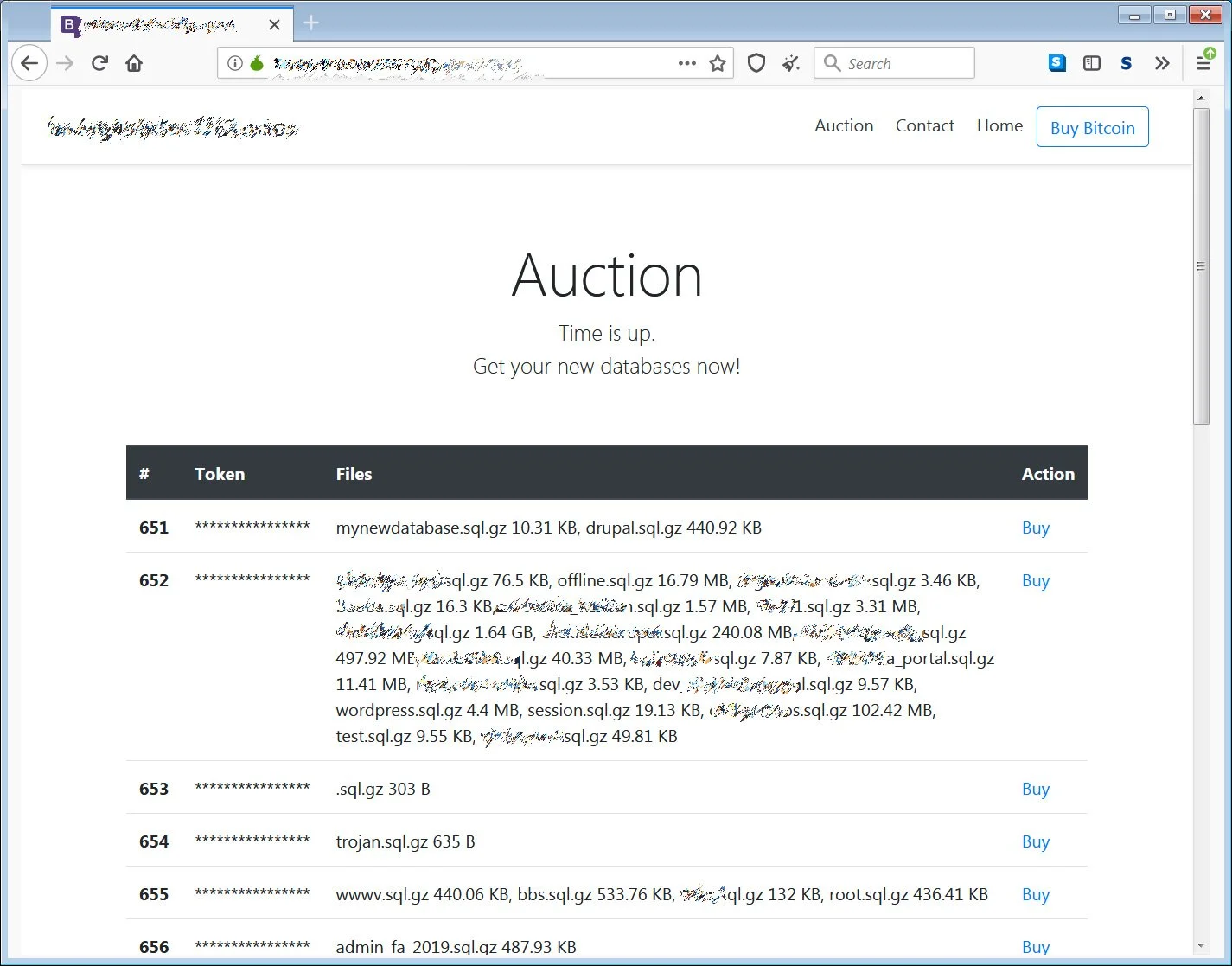
The MySQL databases sold on the auction site range from 20 bytes to gigabytes in size, and are offered for the same amount – 0.03 bitcoins or $545 at current prices.
Also Read: A Look at the Risk Assessment Form Singapore Government Requires
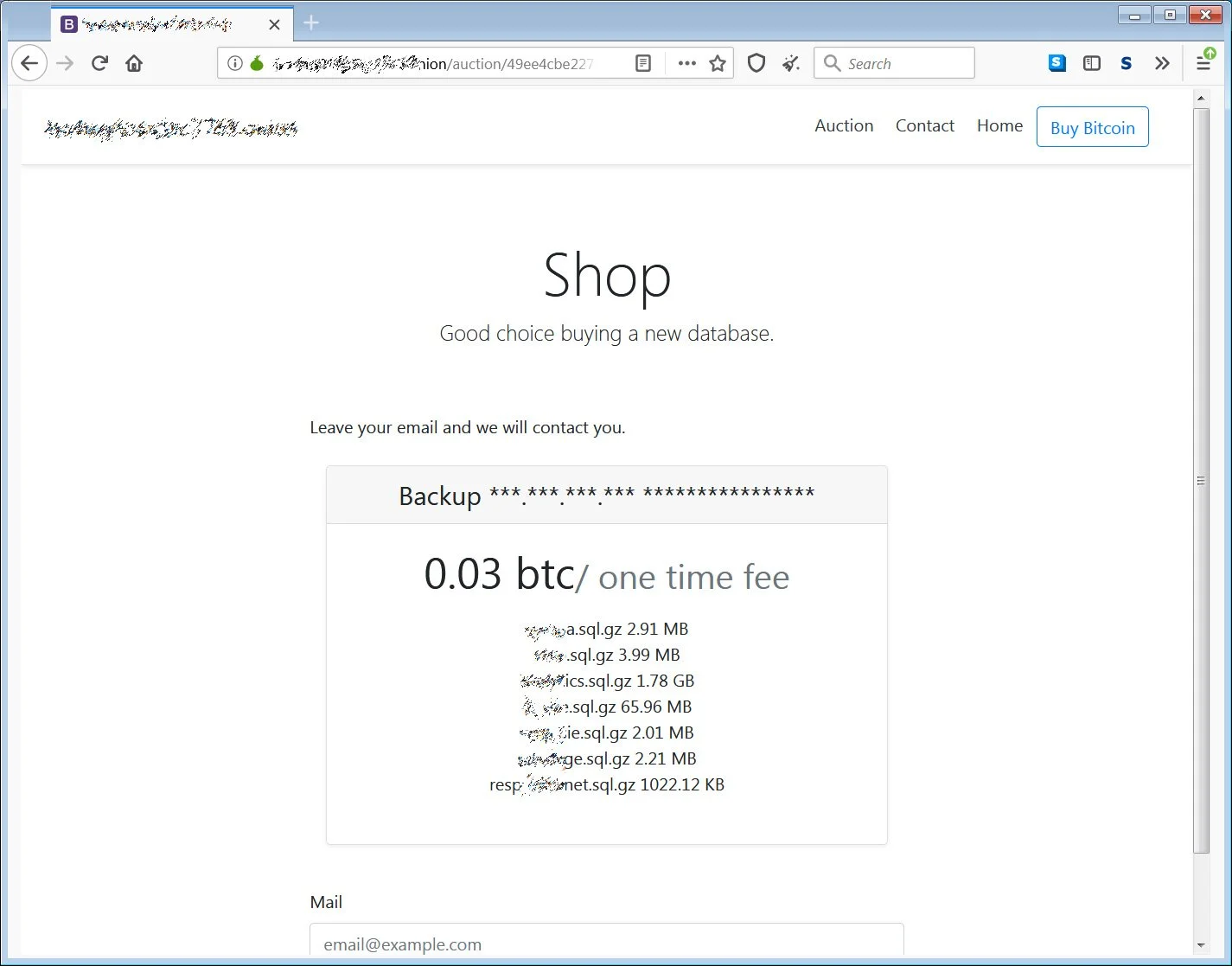
Based on the names and sizes of the auctioned databases, BleepingComputer believes these are automated attacks. This is because the actor is not only selling large databases, but also test and default databases that contain only 20 bytes of data.
In a report published today, Guardicore confirms that the data results from non-targeted, automated attacks that use brute force to gain access to the data.
When the threat actor hacks into a MySQL server, they will execute various commands that archive and copy the databases to the attacker’s infrastructure, delete them from the victim server, and then create a ransom note.
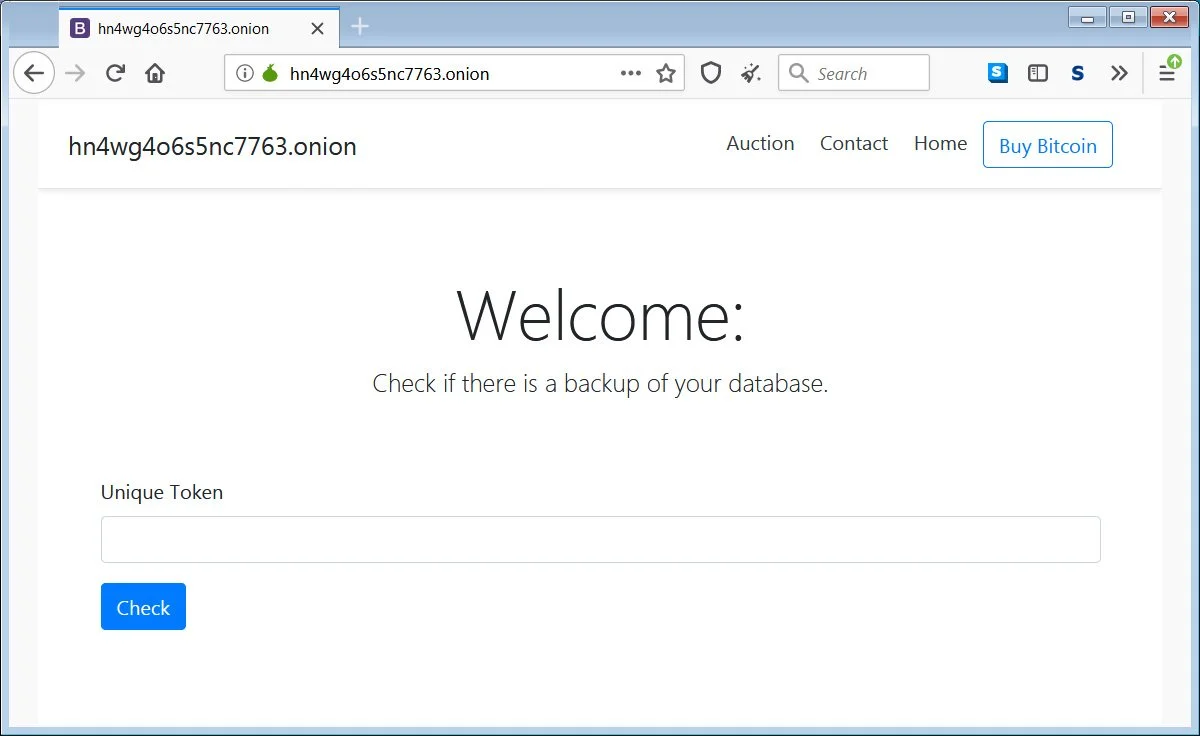
The ransom note is created in a new database table titled ‘warning’ containing a single record.
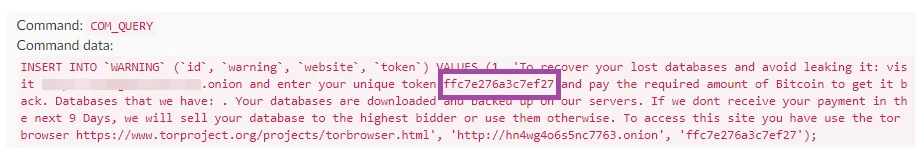
This record has instructions for the victim, directing them to the Tor site to pay the ransom and providing a unique token to access the personal page.
According to Guardicore’s findings, the actor establishes persistence by creating a backdoor user (mysqlbackups’@’%’). This allows them to compromise the server again at a later time.
The researchers distinguish between two stages of this double extortion campaign, that show an evolution of the operation.
In the first one, the ransom note from the attacker had a bitcoin wallet where victims could send money to get their databases. Guardicore telemetry captured 63 attacks of this type, from four different IP addresses.
The auction site is part of the second stage of the campaign and follows the trend set up by cybercriminal gangs in the file-encrypting ransomware business, like REvil, Netwalker, MountLocker and the likes of them.
Also Read: How to Send Mass Email Without Showing Addresses: 2 Great Workarounds
Talking to BleepingComputer, Guardicore researcher Ophir Harpaz says that there’s a good chance that the evolution of the operation may not be the work of the initial actor.
Apart from the leak site, another clue is that Guardicore monitoring systems recorded different sets of IP addresses for the two phases.
At the moment, there are about five million MySQL servers in the world that are reachable over the public internet. Automated attacks such as these are constantly discovering new targets in an attempt to breach them.
Since these are driven by testing common credentials, admins should make it a priority to use strong, unique passwords for databases with important data.
Admins should also avoid exposing the databases, if possible, or at least enable access to them over a secure, non public connection, and complement these defenses with good visibility of the network.