KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A malicious Firefox add-on named “Safepal Wallet” scammed users by emptying out their wallets and lived on the Mozilla add-ons store for seven months.
Safepal is a cryptocurrency wallet application capable of securely holding more than 10,000 types of assets, including Bitcoin, Ethereum, and Litecoin.
Although the malicious browser add-on has been taken down, BleepingComputer has seen the phishing website set up by the threat actors is still up.
“Today I browsed [through] the add-on list of Mozilla Firefox, I was searching for Safepal wallet extension to use my cryptocurrency wallet also in the web browser,” explains a Mozilla add-ons user who goes by the name, Cali
Little did Cali know what was coming for them. A few hours after installing and logging in to the add-on with their real Safepal credentials, the user saw their wallet balance drop to $0.
“I was deep in shock… I saw my last transactions and saw that [$4,000 of my funds] were transferred to another wallet. I could not believe it [was an] add-on that is deployed in the add-on list of Mozilla Firefox,” continues the user in Mozilla’s support forum.
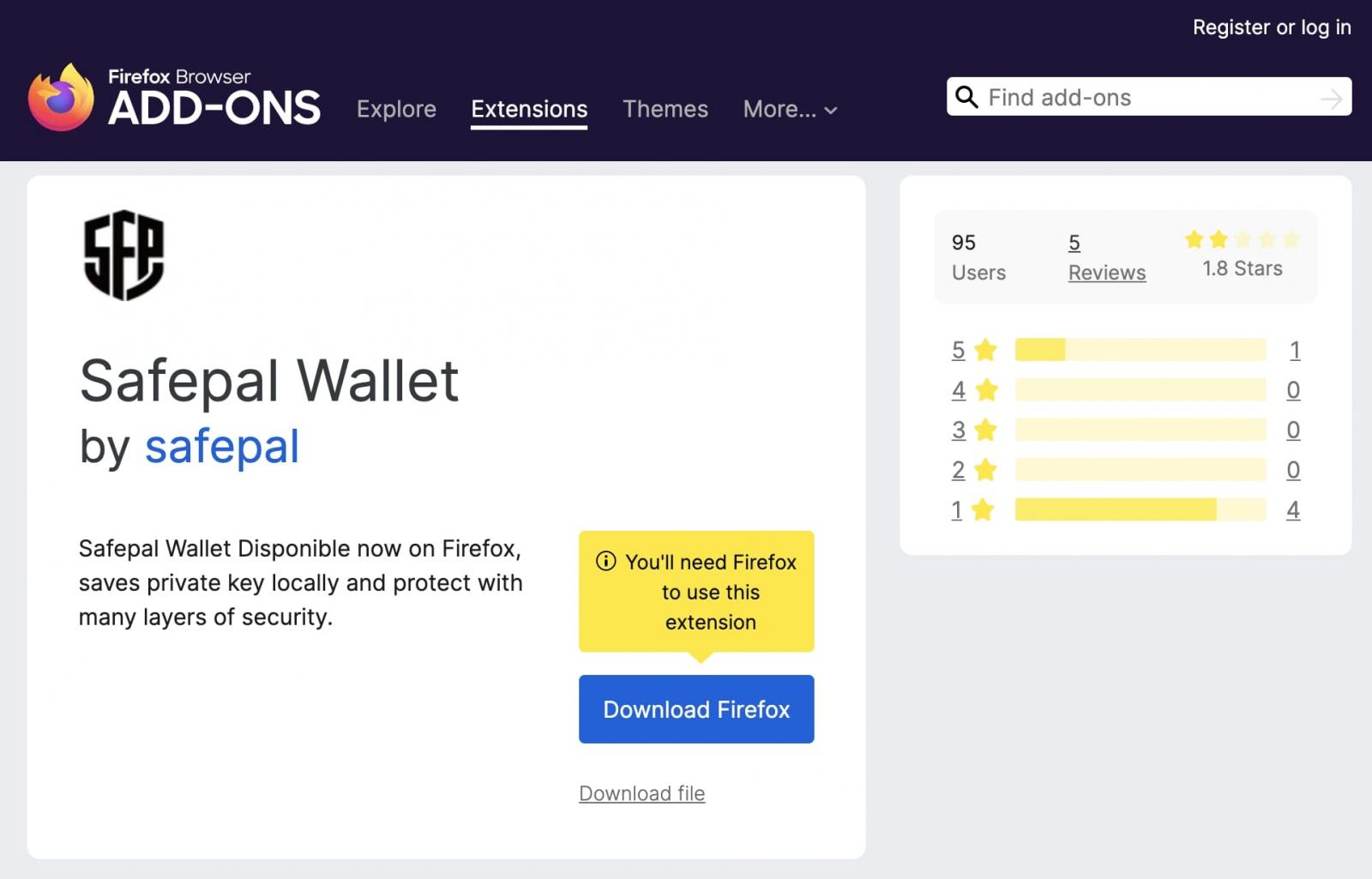
The add-on page for ‘Safepal Wallet’, seen by BleepingComputer, stated the add-on was up since at least February 16th, 2021.
Also Read:
On the same page, the 235 KB add-on touts itself to be a Safepal application that securely “saves private key locally,” along with convincing product images and marketing materials.
To publish an add-on on Mozilla’s website, developers are required to follow a submission process that states submitted add-ons are “subject to review by Mozilla at any time.” But, it isn’t clear to what extent are submissions reviewed with regards to their safety.
Within five days of Cali’s public report of the incident this month, a Mozilla spokesperson responded that they were investigating. The page has since been removed by Mozilla.
Also Read: New Licensing Requirements For Cyber-Security Service Providers in 2022
Although Safepal has official smartphone apps available on both Apple AppStore and Google Play, we are not aware of there being authentic ‘Safepal’ browser extensions.
Thankfully, on Mozilla add-ons store, some users had posted one-star reviews warning others not to download ‘Safepal Wallet’:
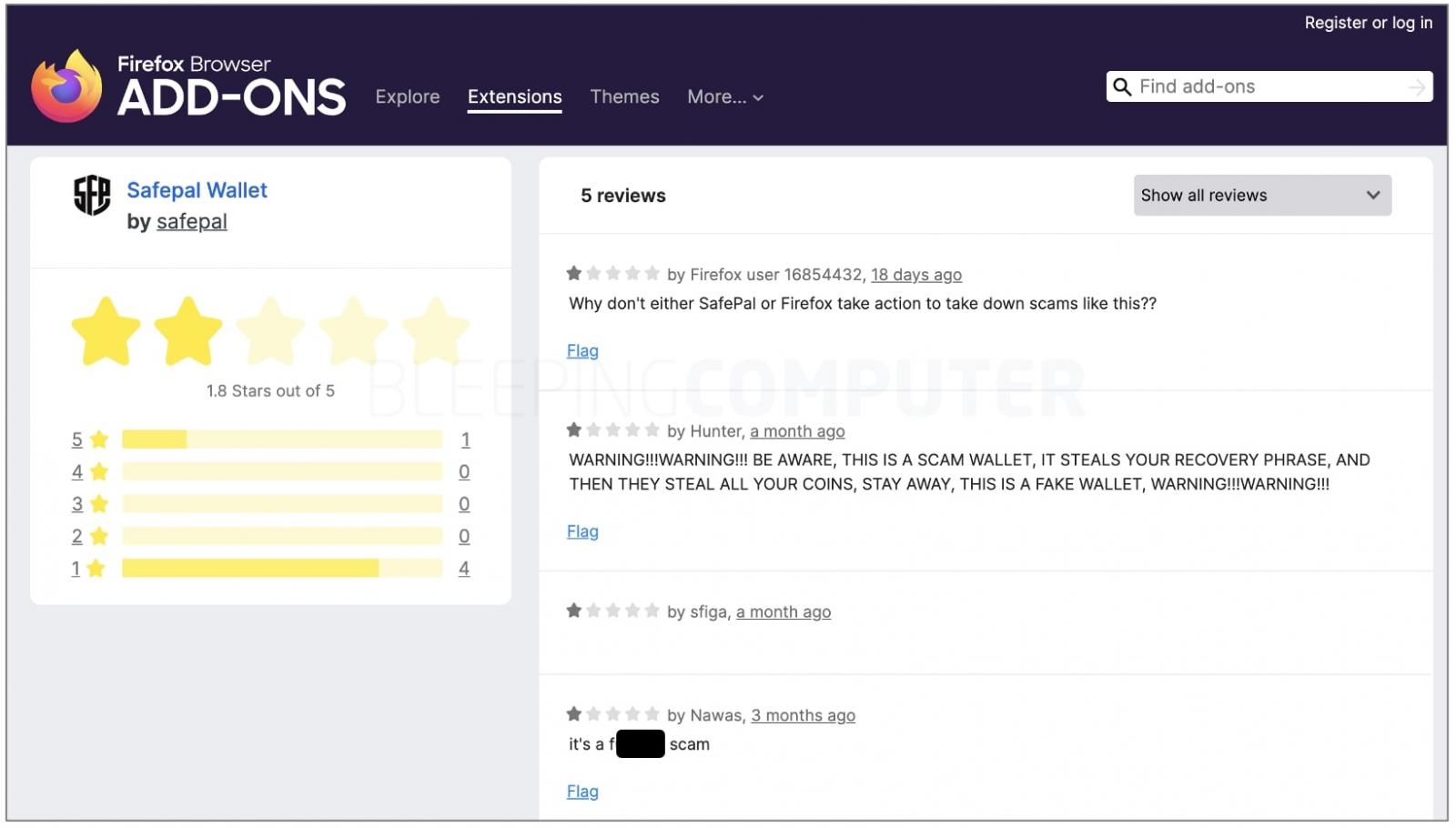
But, for Cali, it seems a little too late in the game, and the chances of them getting their funds back are bleak.
“I already talked with the police they can do nothing for me. They told me that there is no way they can trace the hacker. The only solution is left for me is maybe some of you can help me out by figuring out who the hacker was and how I can get my funds back,” states the user.
BleepingComputer reached out to Mozilla to learn more about the issue:
“Extension security is important to Mozilla, and our ecosystem continually responds to changing threats,” a Mozilla spokesperson told BleepingComputer.
“Our recent focus has been on limiting the damage malicious extensions can do, helping users discover Recommended Extensions that we vet and monitor, helping users understand the risks that come with installing extensions, and making it easier for users to report potentially malicious extensions to us.”
“When we become aware of add-ons that pose a risk to security and privacy according to our Add-on Policies, we take steps to prevent them from running in Firefox. In this instance, shortly after we became aware of potential abuse by this extension, we took action to block and remove it from the Firefox Add-on store.”
Also Read: A Closer Look: The Personal Information Protection Law in China
“Users should be especially cautious about installing software that might have access to private information or financial resources.”
While investigating the malicious Firefox add-on, BleepingComputer came across the phishing domain used by the add-on. This webpage, shown below, was also listed as the “support site” link on the fake add-on’s home page:https://safeuslife.com/tool/
WHOIS records indicate the phishing site was registered in January this year via Namecheap. At the time of writing, the webpage is still live and instructs the victim to key in their “12-word Backup Phrase in the correct order to pair your SafePal Wallet.”
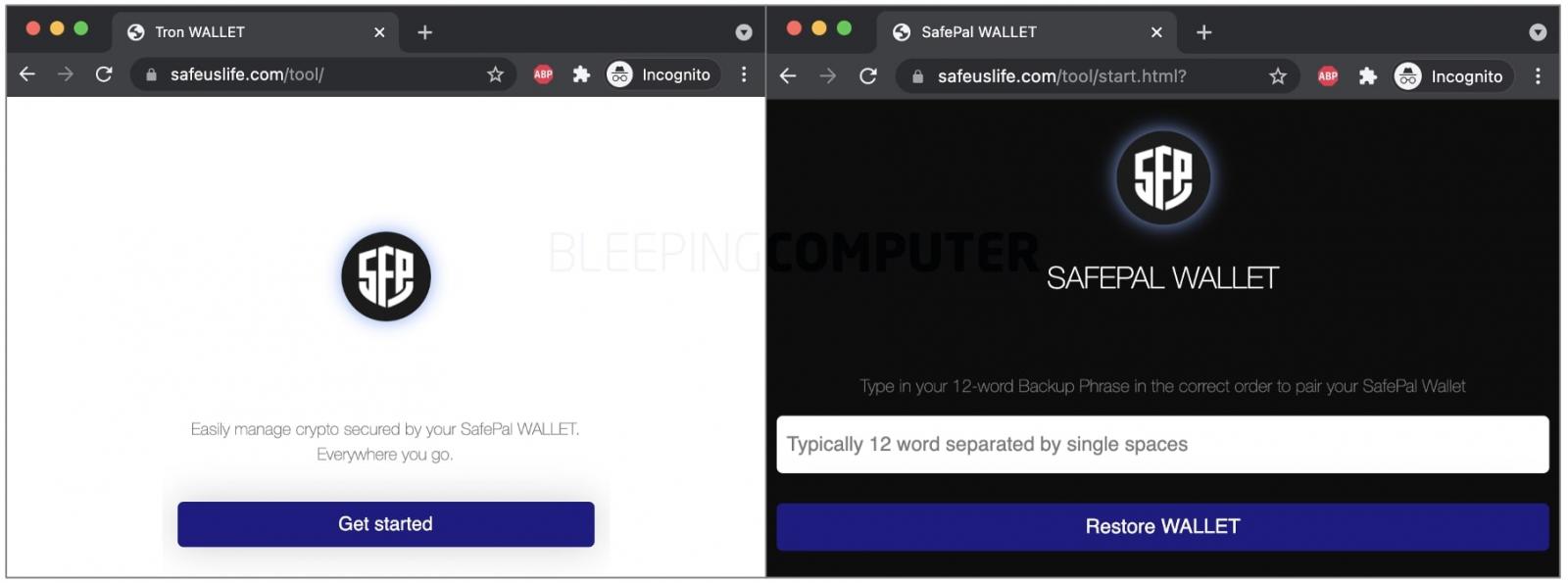
But once the recovery phrase is entered and the form is submitted, the page simply refreshes without any noticeable response. The recovery phrase is silently sent to the attacker.
Cryptocurrency wallets, like many online services, use a backup phrase consisting of twelve randomly generated words that can be used for recovering the user’s private key and wallet, should they forget their password. But, the recovery phrase is a crucial secret meant to be used under exceptional circumstances and only on the trusted app or website of the service provider.
A stolen recovery phrase can grant attackers control over your wallet along with the ability to access and transfer funds.
In recent times, cryptocurrency scams are growing, with threat actors are finding innovative and hard-to-detect ways to trick users. Just last week, someone hacked the official Bitcoin.org website and successfully scammed visitors for $17,000.
In previously seen attacks, open-source repositories, including npm, PyPI, and GitHub have been abused for spreading both cryptostealing and cryptomining malware.
With the increasing presence of threat actors on online platforms, users should be careful when providing their security phrases or transferring cryptocurrency online.
Mozilla additionally recommends the following steps for assessing the safety of any browser extension:
BleepingComputer has reached out to both Mozilla and Safepal for further comment and we are awaiting their responses. We have also reported the phishing domain in question to Namecheap.
Update, Sep 28th, 00:16: Added statement received from Mozilla after publishing.