KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Reporting Date: 18 June 2020
Assessment Period: 1 to 16 June 2020
Subject: Hacker groups are planning a large-scale phishing campaign targeted at more than 5M individuals and businesses (small, medium, and large enterprises) across six countries and multiple continents
Method: The hacking campaign involved using phishing emails under the guise of local authorities in charge of dispensing government-funded Covid-19 support initiatives. These phishing emails are designed to drive recipients to fake websites where they will be deceived into divulging personal and financial information.
CYFIRMA Researchers have been tracking the Lazarus Group, a known hacker group sponsored by North Korea, for many years. Investigations into the Group’s activities have revealed detailed plans indicating an upcoming global phishing campaign.
Also read: Free PDPA Singapore Checklist 2020
There is a common thread across six targeted nations in multiple continents – the governments of these countries have announced significant fiscal support to individuals and businesses in their effort to stabilize their pandemic-ravaged economies. The following are some of the government-funded programs:
> Singapore, a small nation-state in Southeast Asia, has announced almost SGD 100B financial aid in various forms to stem unemployment and keep businesses afloat;
> Japan has announced stimulus funds of about 234 trillion yen;
> Korea government has allocated a total of US$200B of emergency relief funds for industries including carmakers, telecoms, airlines, shipbuilders, and small merchants. The relief funds include cash handouts to families with certain provinces extending the support to tax-paying foreigners;
> Indian government has announced Rs 20 lakh crore (US$307B) of credit, finance and collateral-free loans to micro, small and medium enterprises, as well as welfare packages for citizens;
> America has set aside trillions of dollars to design Economic Impact Payment or Stimulus Payments as well as Paycheck Protection Program to prop up its economy; and
> As part of the UK government COVID-19 recovery strategy, a number of support programs have been made available, such as Coronavirus Job Retention Scheme, and Self-Employment Income Support Scheme. The Government’s package has also been complemented by further contributions from the Bank of England.
The Lazarus Group’s upcoming phishing campaign is designed to impersonate government agencies, departments, and trade associations who are tasked to oversee the disbursement of the fiscal aid.
The hackers plan to capitalize on these announcements to lure vulnerable individuals and companies into falling for the phishing attacks.
Given the potential victims are likely to be in need of financial assistance, this campaign carries a significant impact on political and social stability.
CYFIRMA Researchers first picked up the lead on June 1, 2020, and have been analyzing the planned campaign, decoding the threats, and gathering evidence. Evidence points to hackers planning to launch attacks in six countries across multiple continents over a two-day period. Further research uncovered seven different email templates impersonating government departments and business associations.
As of time of reporting (18 Jun), we have not seen the phishing or impersonated sites defined in the email templates. But our research shows the hackers were planning to set that up in the next 24 hours.
We also observed that hackers are planning to spoof or create fake email IDs impersonating various authorities. These are some of the emails discussed in their phishing campaign plan:
Campaign Launch Dates:
According to the hackers plans as observed by CYFIRMA Research, the phishing campaigns are scheduled to launch in the following countries across multiple continents on the stated dates.
| Country Name | Campaign Launch Date | Target |
| USA | 20 June 2020 | Individuals |
| UK | 20 June 2020 | Businesses |
| Japan | 20 June 2020 | Individuals |
| India | 21 June 2020 | Individuals |
| Singapore | 21 June 2020 | Businesses |
| South Korea | 21 June 2020 | Individuals |
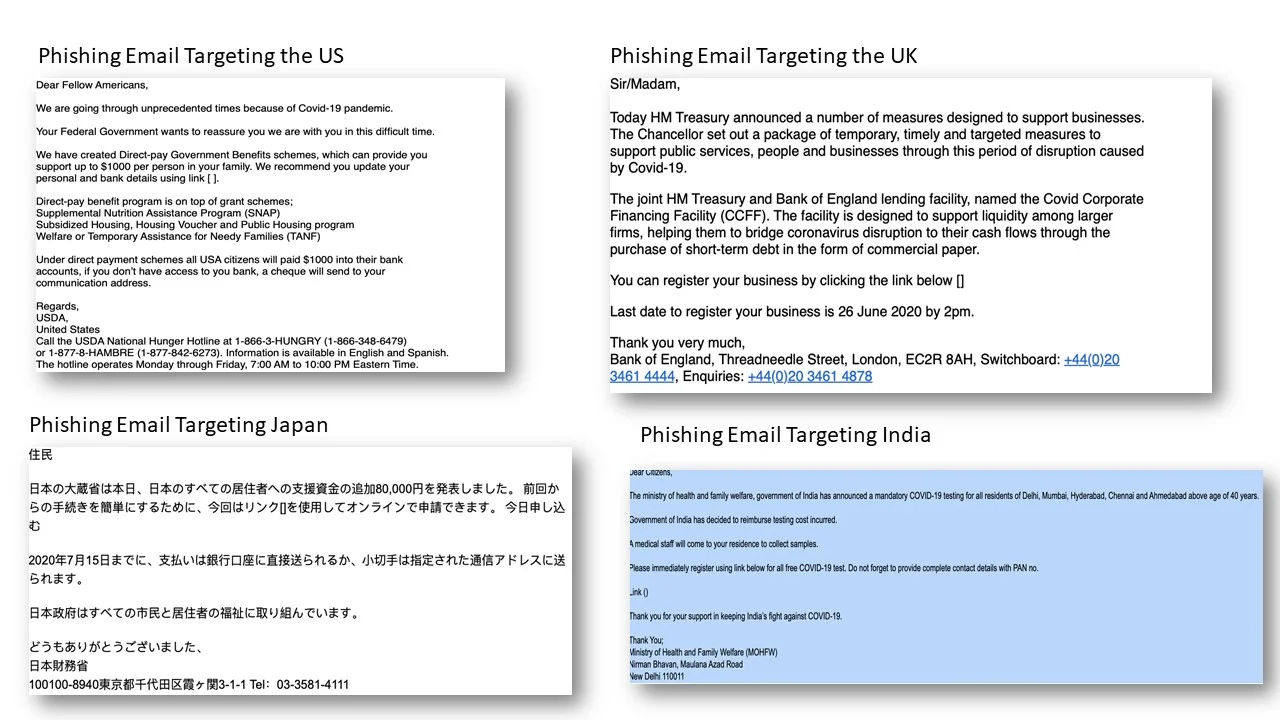
USA: Hackers claimed to have 1.4M curated email IDs. The Plan is to send the email below via a spoofed USDA email account luring them with fake Direct Payment of USD 1000 and inciting them to provide personal detail. Pls see email evidence below.
UK: Hackers claimed to have 180,000 business contacts. The plan is to send email below via a spoofed Bank of England email account and luring them to provide business details, pressing them to provide before 26 June 2020. Pls see email evidence below.
Japan: Hackers claimed to have 1.1M individual email IDs and planning to send phishing email from a spoofed Ministry of Finance, Japan email account offering additional payment of JPY 80,000 for all citizens and residents of Japan. Pls see email evidence below.
India: Hackers claimed to have 2M individual email IDs. The plan is to send emails free COVID-19 testing for all residence of Delhi, Mumbai, Hyderabad, Chennai and Ahmedabad inciting them to provide personal information. Pls see email evidence below.
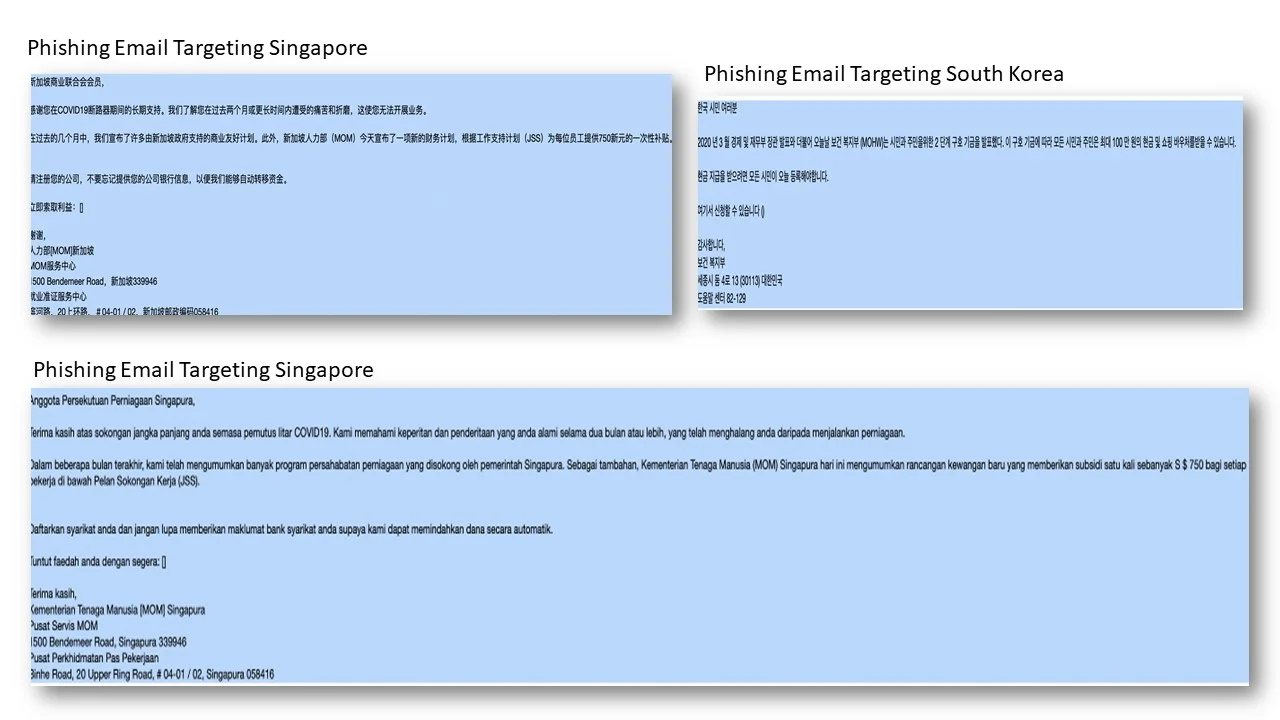
Singapore: Hackers claimed to have 8,000 business contact details and planning to send phishing email from a spoofed Ministry of Manpower email account offering additional payment of SGD 750 for all employees these companies have employed. Pls see email evidences below.
South Korea: Hackers claimed they have 700,000 individual email IDs and will send phishing email to all citizens announcing an additional 1M Won payment in cash and shopping vouchers. The fake email will be spoofed to impersonate the South Korean Government. Pls see email evidence below.
Also read: The FREE Guide To The 9 Obligations Of PDPA