KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Apple has patched today three iOS zero-day vulnerabilities actively exploited in the wild and affecting iPhone, iPad, and iPod devices.
“Apple is aware of reports that an exploit for this issue exists in the wild,” the company said in a security advisory issued today when describing the three flaws.
The list of affected devices includes iPhone 6s and later, iPod touch 7th generation, iPad Air 2 and later, and iPad mini 4 and later.
The zero-days were addressed by Apple earlier today, with the release of iOS 14.2, the mobile OS’ latest stable version.
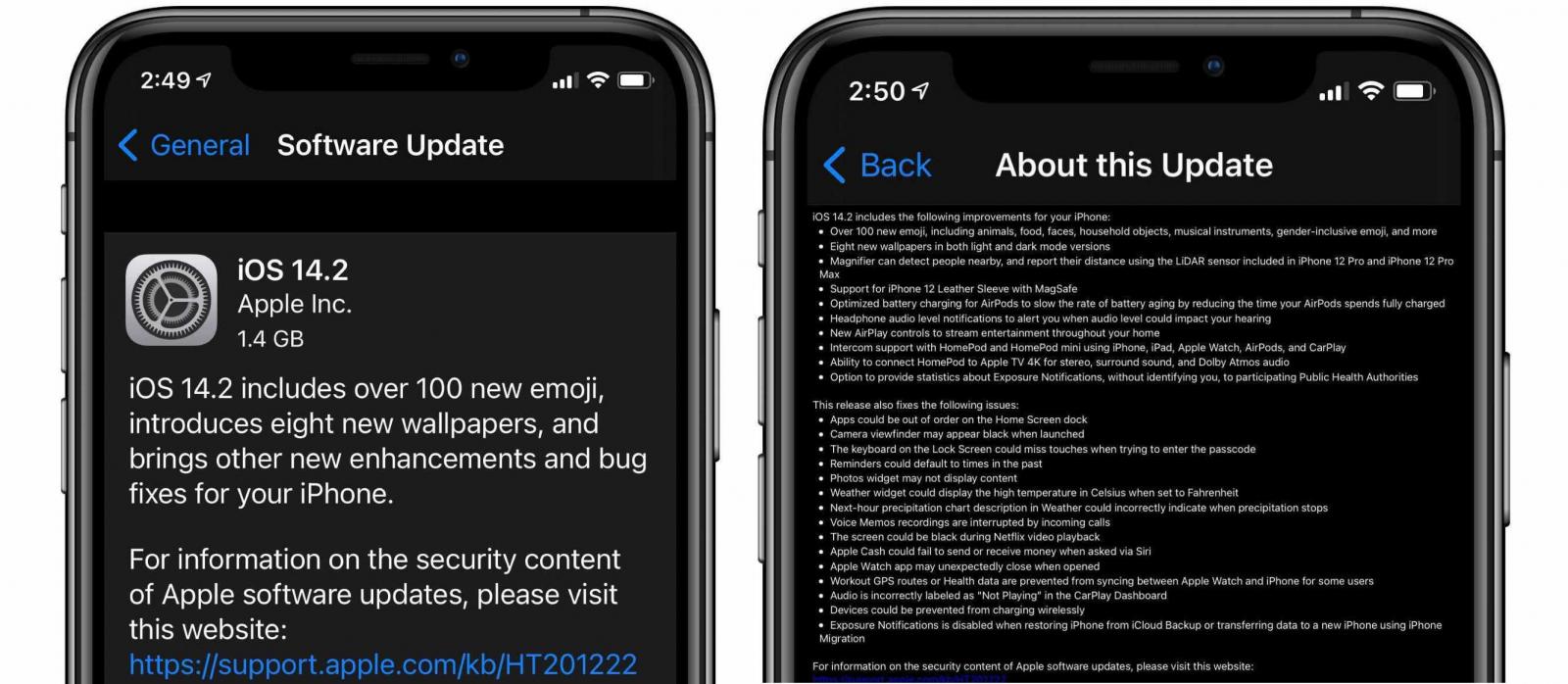
One of the vulnerabilities is a remote code execution (RCE) bug tracked as CVE-2020-27930 and triggered by a memory corruption issue when processing a maliciously crafted font by the FontParser library.
Also Read: By Attending This Event You Agree To Be Photographed
The second iOS zero-day is a kernel memory leak tracked as CVE-2020-27950 and caused by a memory initialization issue that allows malicious applications to gain access to kernel memory.
The third actively exploited bug is a kernel privilege escalation flaw (CVE-2020-27932) caused by a type confusion issue that makes it possible for malicious applications to execute arbitrary code with kernel privileges.
Project Zero, Google’s 0day bug-hunting team, were the ones who discovered and reported the security issues to Apple’s Security team.
“Targeted exploitation in the wild similar to the other recently reported 0days,” said Shane Huntley, Director and Google’s Threat Analysis Group. “Not related to any election targeting.”
Four other zero-days disclosed or patched during the last two weeks were also discovered by Google’s Project Zero researchers.
Google patched two actively exploited Chrome zero-day flaws (CVE-2020-15999 in the FreeType text-rendering library and CVE-2020-16009 in the WebAssembly and JavaScript engine).
A third one (CVE-2020-16010) caused by a heap buffer overflow in the Android UI was addressed in Chrome for Android 86.0.4240.185, released on Monday.
The Project Zero researchers also disclosed an elevation of privileges (EoP) zero-day in the Windows kernel exploited in the wild, affecting all versions between Windows 7 and Windows 10.
Also Read: What Legislation Exists in Singapore Regarding Data Protection and Security?
A patch for the Windows zero-day should be provided by Microsoft on November 10 during this month’s Patch Tuesday.