KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Threat actors are actively exploiting Oracle WebLogic servers unpatched against CVE-2020-14882 to deploy Cobalt Strike beacons which allow for persistent remote access to compromised devices.
Cobalt Strike is a legitimate penetration testing tool also used by threat actors in post-exploitation tasks and to deploy so-called beacons that enable them to gain persistent remote access.
This later allows them to access the compromised servers to harvest data and to deploy second stage malware payloads.
The CVE-2020-14882 remote code execution (RCE) flaw was patched by Oracle during last month’s Critical Patch Update and it was used by attackers to scan for exposed WebLogic servers one week later.
Since then, a related no-auth RCE vulnerability tracked as CVE-2020-14750, also allowing for unauthenticated to take over unpatched instances, was addressed by an out-of-band security update issued last weekend.
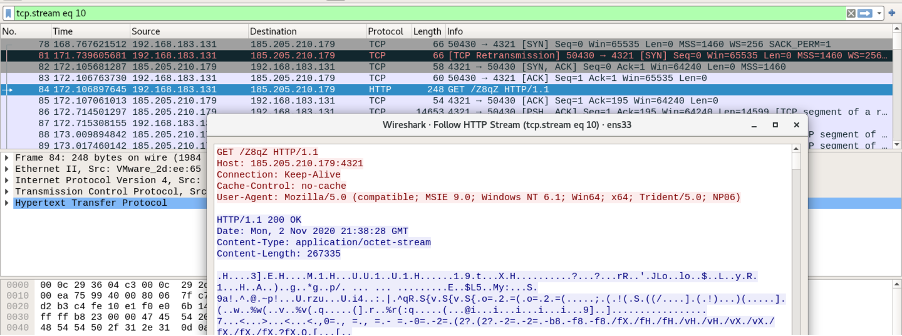
This latest series of attacks targeting vulnerable WebLogic instances started over the weekend as SANS ISC Handler Renato Marinho revealed in an advisory.
Also Read: Going Beyond DPO Meaning: Ever Heard Of Outsourced DPO?
Attackers are using a chain of base64-encoded Powershell scripts to download and install Cobalt Strike payloads on unpatched Oracle WebLogic servers.
“Interestingly, 66 percent of all ransomware attacks this quarter involved red-teaming framework Cobalt Strike, suggesting that ransomware actors are increasingly relying on the tool as they abandon commodity trojans,” the Cisco Talos Incident Response (CTIR) team revealed in a September quarterly report.
Given that both CVE-2020-14882 and CVE-2020-14750 can easily be exploited by unauthenticated attackers to take over vulnerable WebLogic servers, Oracle advises companies to immediately apply the security updates to block attacks.
“Due to the severity of this vulnerability, Oracle strongly recommends that customers apply the updates provided by this Security Alert as soon as possible after they have applied the October 2020 Critical Patch Update,” the company said in an advisory issued over the weekend.
Eric Maurice, Director of Security Assurance at Oracle, also shared a link to WebLogic Server hardening instructions in a blog post announcing the out-of-band security update on Sunday.
Also Read: Limiting Location Data Exposure: 8 Best Practices
The Cybersecurity and Infrastructure Security Agency (CISA) also urged administrators to apply the security update as soon as possible to address the two critical vulnerabilities.
Cybersecurity firm Spyse which operates an IT infrastructure search engine discovered over 3,300 exposed Oracle WebLogic servers potentially vulnerable to CVE-2020-14882 exploits.