KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Singapore’s largest online grocery store Lazada Redmart has suffered a data breach after 1.1 million user accounts were put up for sale on a hacker forum.
The database dump containing sensitive customer is priced at $1,500.
Lazada is a billion-dollar arm of Alibaba with over 8,000 employees globally.
Hackers selling the illicit data dumps told BleepingComputer they had obtained Lazada’s MongoDB-based data set with data from over 1.1 million RedMart accounts.
The leaked dump contains RedMart customer accounts’ email addresses, SHA-1 hashed passwords, first and last name, phone numbers, mailing addresses, billing addresses, partial credit card numbers, and expiration dates.
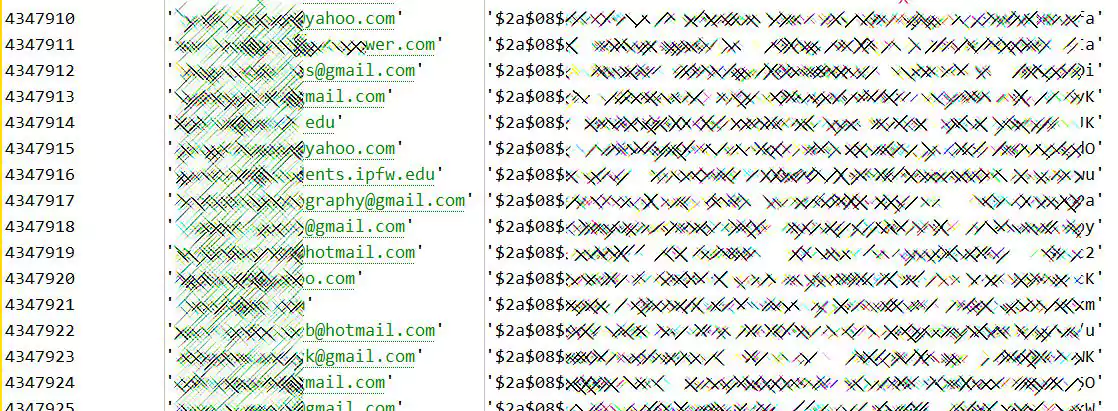
According to the hackers, however, the data set isn’t standardized, and that “some rows have more information than others.”
Also Read: How Singapore Cybersecurity Materplan 2020 Is Formidable
For example, certain customers had the first 6 and last 4 digits of their credit card number included with their data.
On October 29th, Lazada sent out an email notification to impacted customers stating they had discovered the breach during “proactive monitoring” of their systems.
In Lazada’s data breach notification, the company claims that the data exposed in the breach is 18 months old.
“The customer data hosted on this database is more than 18 months out of date as it was last updated in March 2019,” Lazada stated.
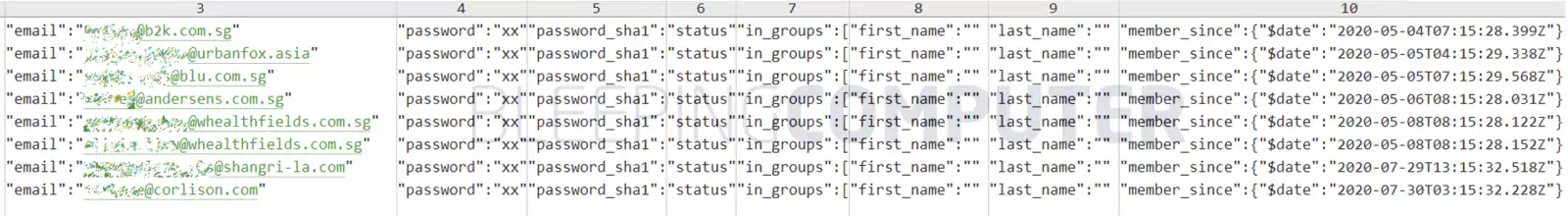
However, the data breach broker told BleepingComputer in a conversation that the stolen database contains user records with registration dates in May and July 2020, as shown below.
The data breach email further reassured customers that their passwords are “protected by encryption.”
While the passwords in the stolen database are indeed SHA-1 hashed, it is possible to dehash them to recover the original password.
As a safety precaution, RedMart has reset the passwords on all accounts and will prompt you to change it the next time you login.
It is also suggested that you change your password on any other sites utilizing the same one as used on RedMart.
RedMart users should also be on the lookout for targeted phishing emails that utilize the information in the stolen database.
“Lazada does not request customers to verify your personal information,” the breach notification stated.
The exact date of the breach remains unknown.
When BleepingComputer asked the data breach broker how RedMart was compromised, they declined to share that information.
Also Read: The PDPA Data Breach August 2020: A Recap of 8 Alarming Cases
According to RedMart, on discovering the breach, the company took steps to promptly block access to the database.
“We have taken immediate action to block unauthorised access to the database. This data was used on the previous RedMart app and website, which are no longer in use. Lazada customer data in Southeast Asia is not affected by this incident,” reads the email notification.
The company also stated they were reviewing and hardening their security controls in addition to collaborating with the law enforcement authorities on this incident.
“We want to be transparent about this incident with all of our customers and reassure you that we are taking it seriously,” concluded the notification.
But what stands out is the discrepancy between their claim of the leaked data being 18 months old and the database screenshot above showing July 2020 registration dates.