KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Multiple members of QQAAZZ, a multinational cybercriminal group, were charged today in the US, Portugal, Spain, and the UK for providing money-laundering services to several high-profile malware operations including Dridex, Trickbot, and GozNym.
Law enforcement estimations say that QQAAZZ laundered, or at least attempted to launder, tens of millions stolen from cybercrime victims starting with 2016.
“QQAAZZ advertised its services as a ‘global, complicit bank drops service’ on Russian-speaking online cybercriminal forums where cybercriminals gather to offer or seek specialized skills or services needed to engage in a variety of cybercriminal activities,” the Department of Justice said today.
“The criminal gangs behind some of the world’s most harmful malware families (e.g.: Dridex, Trickbot, GozNym, etc.) are among those cybercriminal groups that benefited from the services provided by QQAAZZ.”
Also Read: 5 Self Assessment Tools To Find The Right Professional Fit
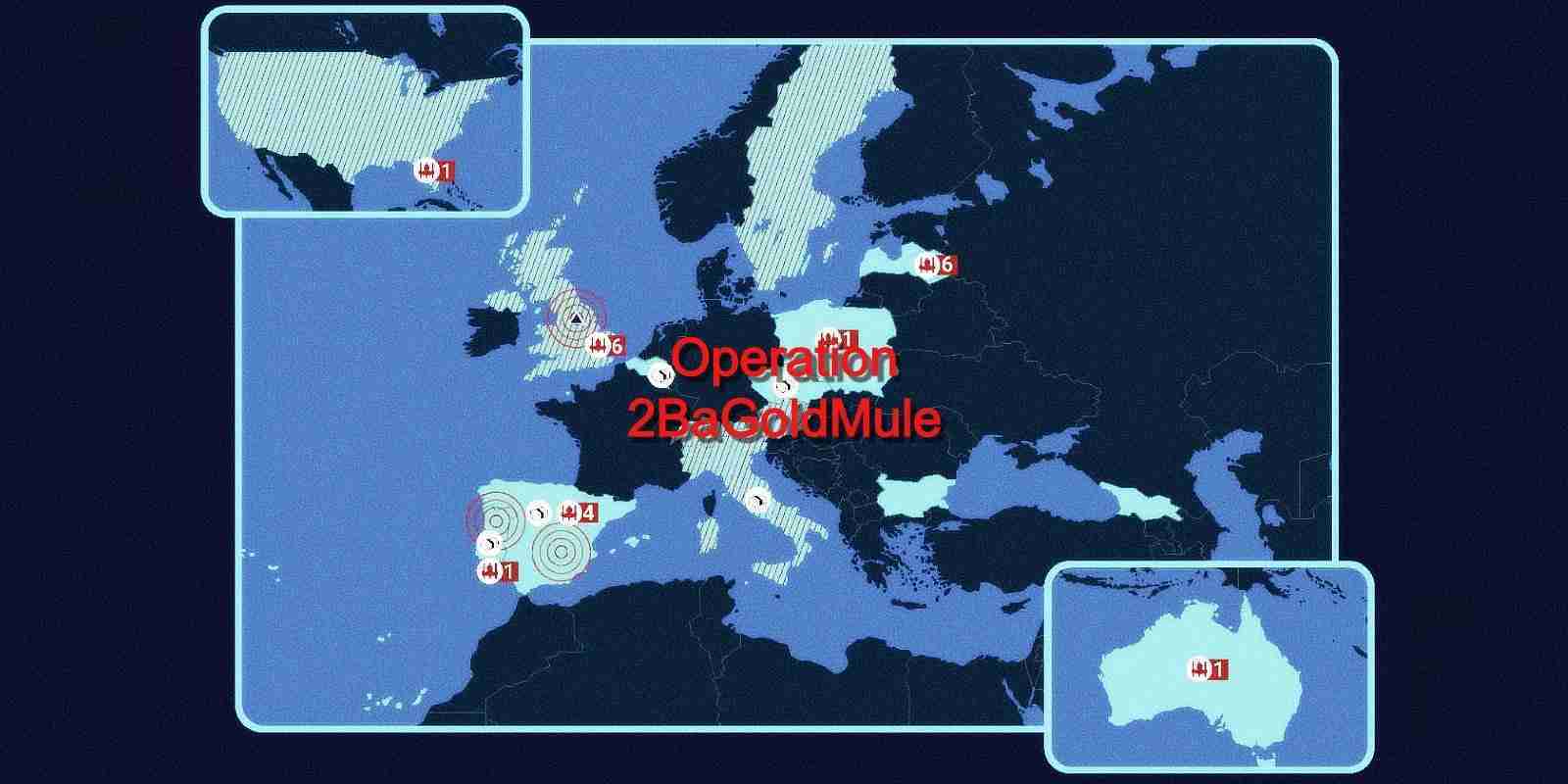
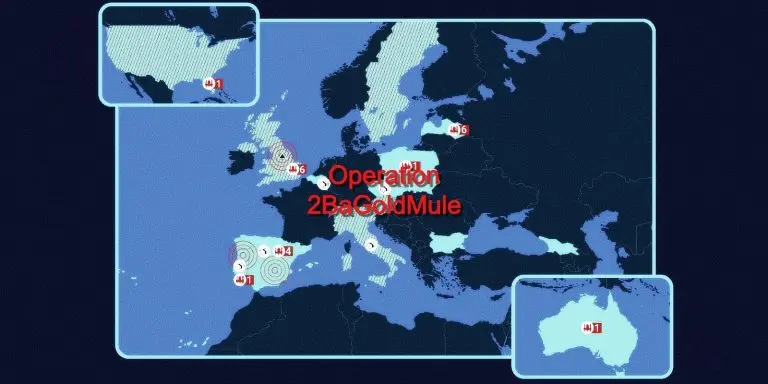
20 QQAAZZ members were arrested in a series of more than 40 house searches in Latvia, Bulgaria, the United Kingdom, Spain, and Italy.
This was the result of an international law enforcement operation involving 16 countries coordinated by the Europol and dubbed Operation 2BaGoldMule
An extensive bitcoin mining operation associated with QQAAZZ was also seized in Bulgaria as part of this operation.
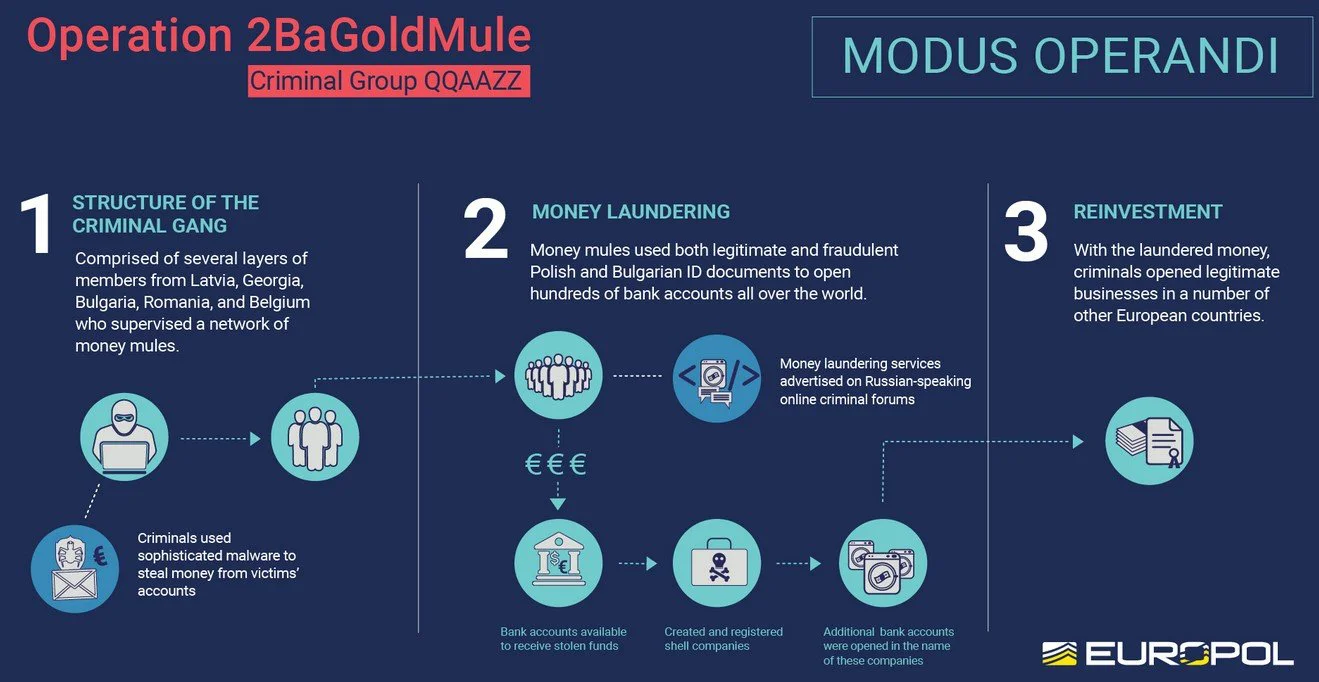
According to indictments unsealed today [1, 2], the criminal gang offered its “cash-out services” in the form of a “global, complicit bank drops service) to high-profile Russian cybercrime gangs on Russian-speaking cybercriminals forums (e.g., Verified and Mazafaka).
They communicated with their “clients” via instant messaging, instructing them to send the stolen funds to bank accounts under QQAAZZ’s control and opened with the help of money mules using fake and legitimate Polish and Bulgarian ID documents.
QQAAZZ’s members also incorporated dozens of shell companies, used to open other bank accounts which were later used to receive and launder funds stolen by cybercriminals using malware.
In total, “hundreds of corporate and personal bank accounts at financial institutions throughout the world” were used during the money laundering operation.
Also Read: Best Privacy Certification: 3 Simple Steps On How To Achieve
Some of the money was also “converted to cryptocurrency using ‘tumbling’ services designed to hide the original source of the funds.”
QQAAZZ returned a part of the laundered funds to their cybercrime clients, after taking fees of up to 50% for themselves out of the total balance of stolen funds received.
While dozens of victims who had their money stolen and laundered by QQAAZZ were identified in the US, the total number and their identity is unknown given the scale of the money laundering operation and the multitude of cybercrime gangs it served.
“Cybercriminals are constantly exploring new possibilities to abuse technology and financial frameworks to victimise millions of users in a moment from anywhere in the world,” Edvardas Šileris, Head of Europol’s European Cybercrime Centre, said.
“Today’s operation shows how through a proper law enforcement international coordination we can turn the table on these criminals and bring them to justice.”