KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A security researcher discovered that malicious apps for Fitbit devices can be uploaded to the legitimate Fitbit domain and users can install them from private links.
With some social engineering, hackers could take advantage of this and trick users into adding apps to obtain the wealth of personal information typically collected from Fitbit device sensors or the phone.
Fitbit develops fitness activity tracking wearables (smartwatches, bands) providing the user with metrics like number of steps walked or steps climbed, heart rate, sleep quality, along with activity history. Various mobile apps (health, games, music, utilities) from Fitbit and its developer community are published in the official Fitbit Gallery.
Also Read: By Attending This Event You Agree To Be Photographed
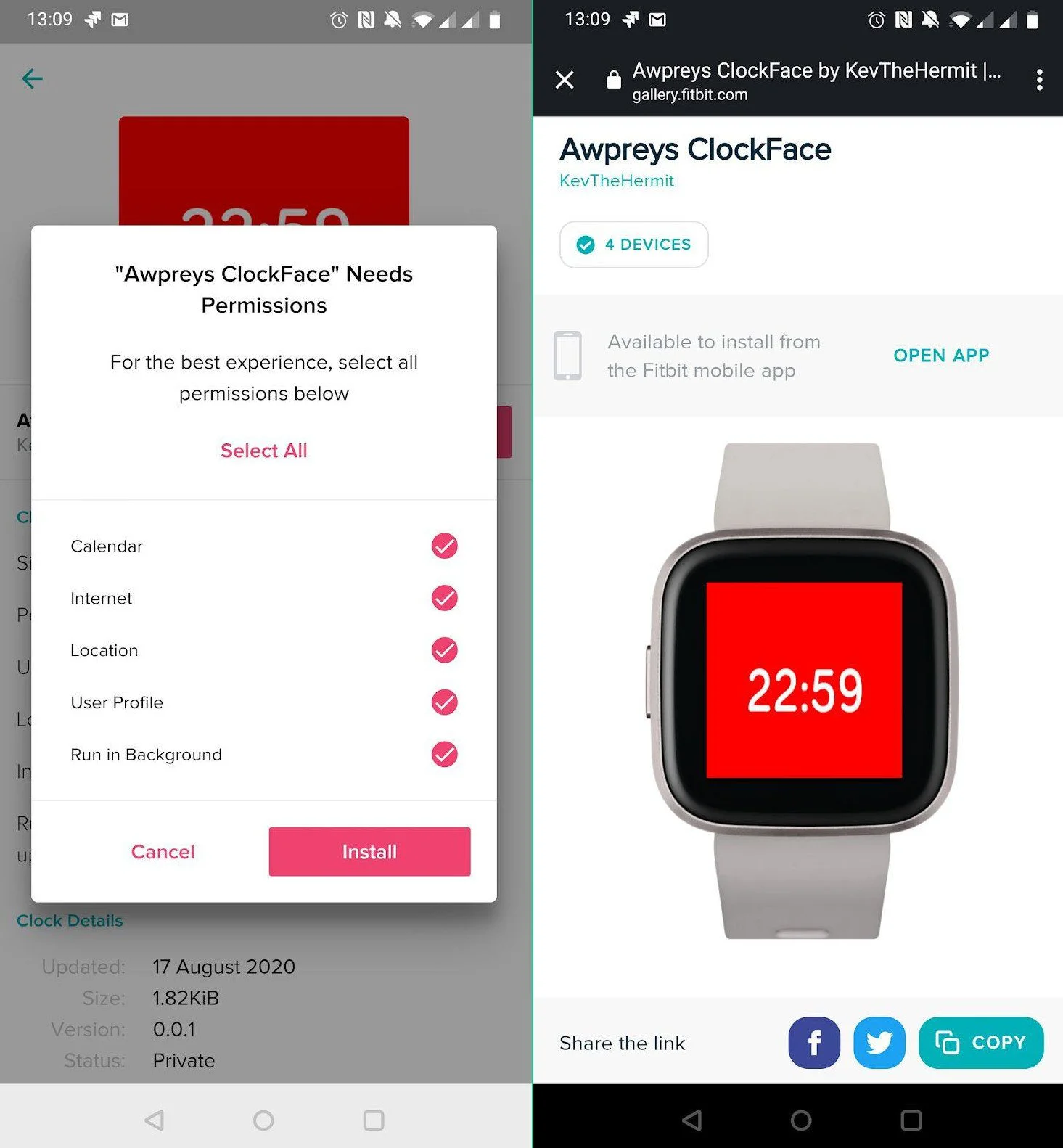
Kevin Breen, threat research director at Immersive Labs, was able to upload to the Fitbit Gallery a malicious app he created specifically to test if it would bypass the app store’s defenses.
Driven by the curiosity to see if this would be a feasible attack method against enterprise environments, Breen included in the app code that could steal device details, personal body data, and would allow a connection to company connections for ill-intended actions.
He figured that being delivered from the legitimate Fitbit domain the app would bypass protections for unauthorized or suspicious installations, reasoning that proved to be right.
“Essentially, it could send device type and location, user information such as gender, age, height, heart rate and weight as well as accessing calendar info. Whilst this doesn’t include PII profile data the calendar invites could expose additional information such as names and locations,” the researcher notes in a report today.
He says that all the data comes from the Fitbit watch or the paired phone and includes GPS location, heart rate, accelerometer data, body presence, as well as user details like age, height, gender, average heart rate.
Furthermore, his app for Android could also connect to the calendar and read events if synchronization is active. On iOS, the permission to access the calendar was not active by default.
Also Read: A Look at the Risk Assessment Form Singapore Government Requires
Since it can run in the background, all the data can be delivered to a server when an internet connection is available.
The researcher says that the Fitbit software development kit (SDK) exposes a web API, accessible from the application for allowing (oAuth) a connection to it.
Not all users would go this far in configuring their app but those that complete this step will find loads of private and sensitive data being available: name, date of birth, all activity history, list of friends, sleep times.
“As the fetch API allows the use of HTTP to internal IP ranges, I also managed to turn the malicious watch face into a primitive network scanner that could scan and access internal network sites and services” – Kevin Breen
Achieving this required only setting up a server to scan IP addresses and code that allowed the app to connect and execute code. This would essentially convert the Fitbit device into a gadget that could map the enterprise network and interact with devices available (routers, firewalls).
Breen’s malicious app is still present in the Fitbit gallery, accessible via a private link. The researcher notes that it does not have a call-back domain configured, to prevent it from leaking data if installed by accident.
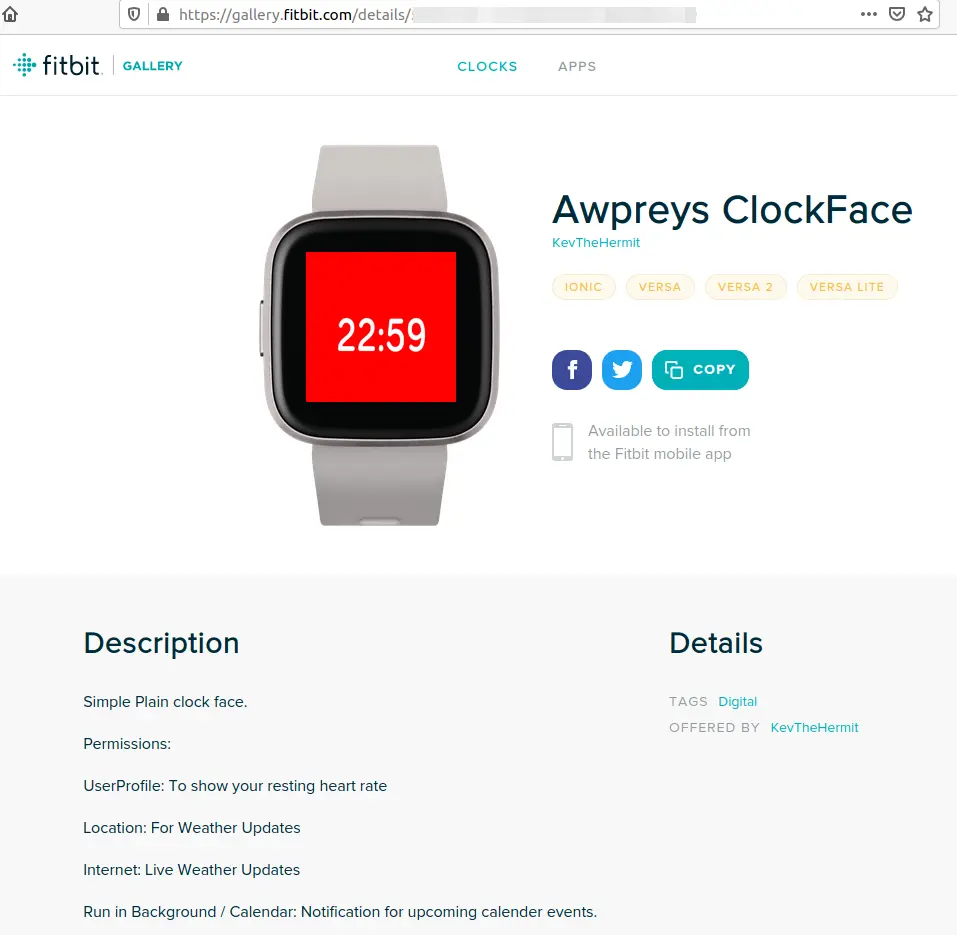
However, it is possible to configure a server address manually from the app’s settings page. Even if not publicly exposed, attackers could still find it and leverage it in phishing attacks or use it as a model to create other malicious apps for Fitbit.
Breen reported the issues to Fitbit and received a prompt response from the company informing that a set of mitigations would follow.
Fitbit said that unlike the private apps in its gallery that have not been officially submitted, those that are publicly available go through a manual check to ensure they have no malicious behavior.
“This is standard stuff but to my mind did not address the issue of malicious apps still being available from the Fitbit domain prior to being officially submitted. This, in my opinion, presented a social engineering vector,” said Breen.
His research has prompted some changes for the better, though. Users will get a warning when installing an app from a private link; if it is already installed, it will be identified in the list of Fitbit apps present on the phone as not being in the public Fitbit Gallery.
These changes should already be active. Fitbit also told Breen that a future update will adjust permissions during the authorization flow so that they are opt-out by default and the user can select them as needed.