KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Over the past two weeks, Sam’s Club has started sending automated password reset emails and security notifications to customers who were hacked in credential stuffing attacks.
Sam’s Club, owned by Walmart, is an American chain of membership-only retail warehouse clubs operating since 1983. The brand is frequently listed alongside Costco and BJ’s Wholesale Club.
BleepingComputer had been closely monitoring these notifications over this period and has heard from Sam’s Club.
In emails sent out to Sam’s Club members, and seen by BleepingComputer, the company is alerting members that an unauthorized party may have gained access to their accounts.
This activity, detected by Sam’s Club in September, did not stem from a data breach. According to the company, it was likely a result of the attackers already knowing the user’s credentials—for example, via credential stuffing, data breaches, or phishing.
Also Read: How Bank Disclosure Of Customer Information Work For Security
Credential stuffing attacks involve the attackers trying previously leaked username-password combinations against another website in an automated fashion, in an attempt to find accounts that share the same credentials.
That is one reason security professionals strongly advise against using the same username-password combination across different websites. Should one such website be compromised, the attackers would now be able to re-use the leaked credentials on others as well.
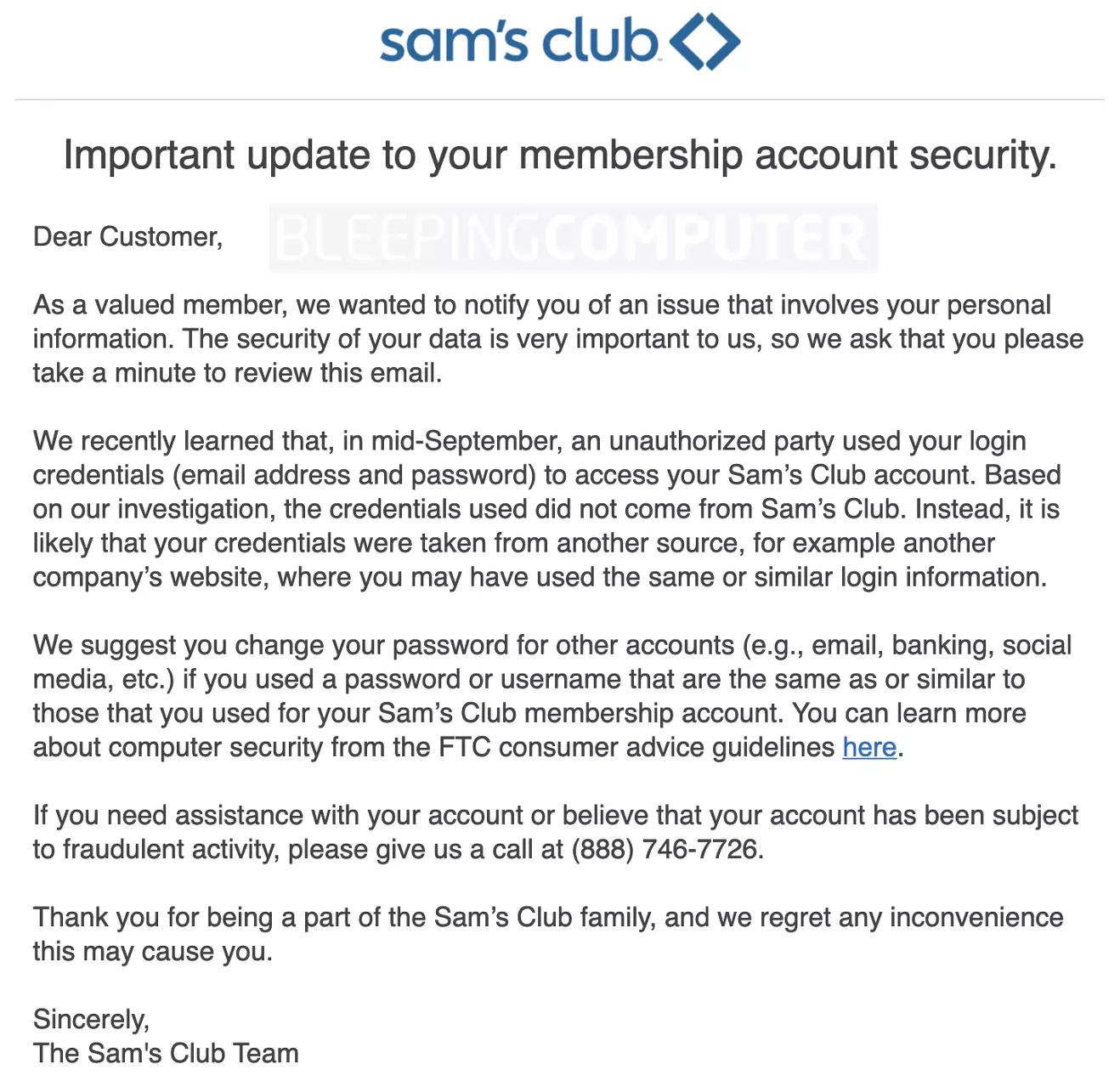
“We recently learned that, in mid-September, an unauthorized party used your login credentials (email address and password) to access your Sam’s Club account. Based on our investigation, the credentials used did not come from Sam’s Club,” read the security notification.
“Instead, it is likely that your credentials were taken from another source, for example, another company’s website, where you may have used the same or similar login information,” the email continued.
When asked for more information, Sam’s Club spokesperson Meggan Kring told BleepingComputer:
“Protecting our members’ privacy is something we take very seriously, and we are continually monitoring for suspicious activity. As part of this effort, we recently found that unauthorized parties had logged into certain member accounts.”
“This was not a breach of our systems, but rather a case of these parties obtaining user names and passwords from phishing campaigns, planting malware or breaches at other companies. We have reset passwords for these accounts and are taking additional measures to protect the accounts from fraudulent activity.”
“We are reaching out directly to those members who were affected,” Kring told BleepingComputer.
Also Read: How To Check Data Breach And How Can We Prevent It
Previously, Sam’s Club members had received security notifications alerting them of an automatic password reset due to suspicions of unauthorized account access.
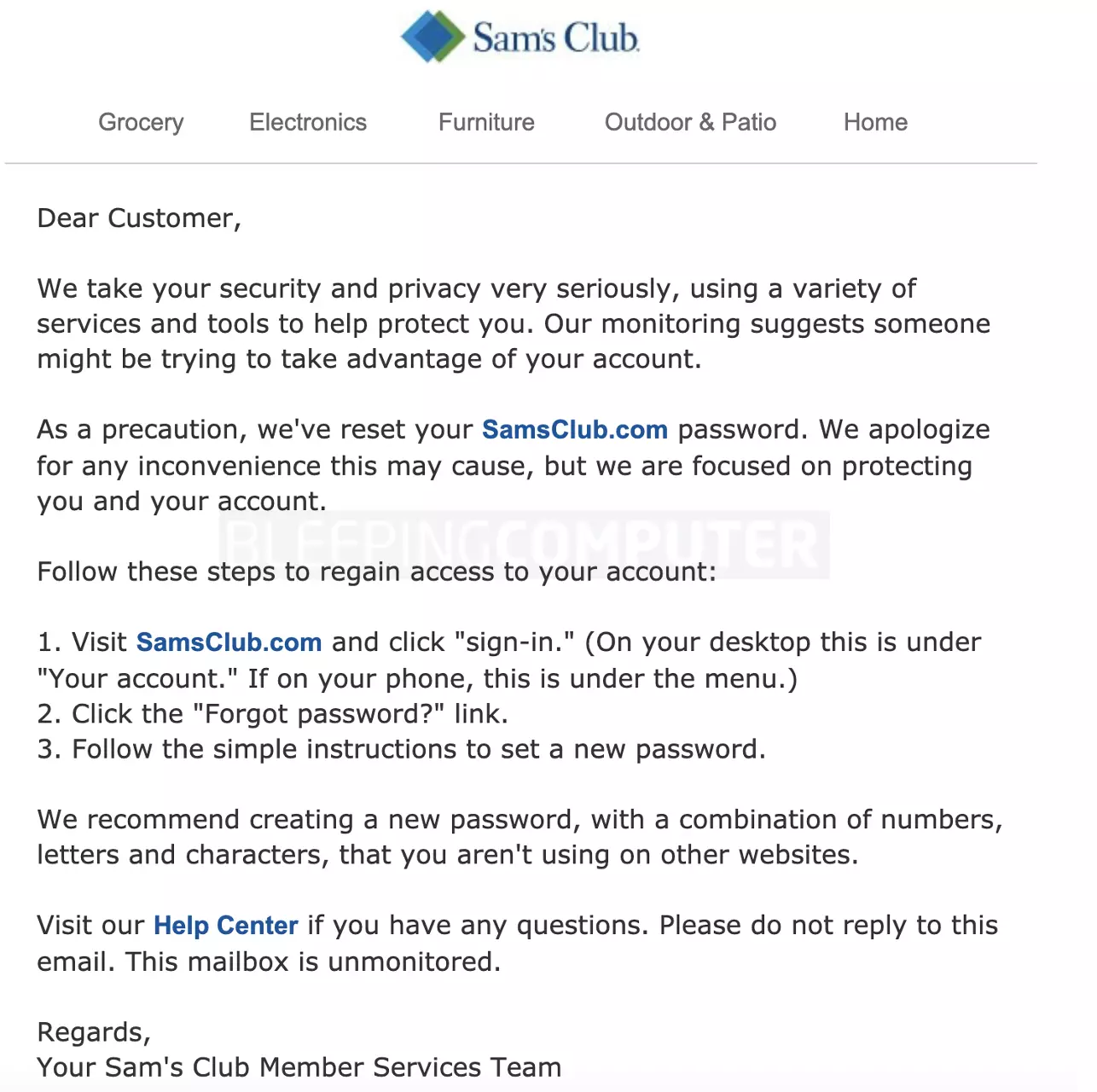
A copy of such an email obtained by BleepingComputer was sent September 24, 2020, to customers and read:
“Our monitoring suggests someone might be trying to take advantage of your account. As a precaution, we’ve reset your SamsClub.com password. We apologize for any inconvenience this may cause, but we are focused on protecting you and your account.”
More companies should follow Sam’s Club’s lead in proactively monitoring customer accounts and resetting passwords. This proactive protection of customers is especially important with cyberattacks on the rise and attackers deploying credential stuffing attacks that deprive people of COVID-19 relief payments.
However, it is not clear how it became possible to gain unauthorized access to Sam’s Club member accounts. Assuming the credential stuffing technique was leveraged as an attack vector, were there no automated rate limiters or security controls in place?
Cybersecurity challenges continue to grow as the attackers constantly evolve their tactics, and defenders continue to catch up in stepping up their game.