KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The second-ever UEFI rootkit used in the wild was found by security researchers during investigations surrounding attacks from 2019 against two non-governmental organizations (NGOs).
UEFI (Unified Extensible Firmware Interface) firmware allows for highly persistent malware given that it’s installed within SPI flash storage soldered to a computer’s motherboard making it impossible to get rid of via OS re-installation or hard drive replacement.
The UEFI bootkit, dubbed MosaicRegressor by Kaspersky researchers Mark Lechtik and Igor Kuznetsov who discovered it, is a modular and multi-stage malware framework used by Chinese-speaking hackers in data theft and espionage operations.
Only one other instance of a UEFI bootkit being used in the wild is known, namely LoJax, a rootkit discovered by ESET in 2018.
LoJax was injected by the Russian-speaking APT28 hacker group within the legit LoJack anti-theft software in the form of patched UEFI modules.
The malicious UEFI firmware images were modified by the attackers by injecting multiple malicious modules that can be used to deploy malware on targeted devices.
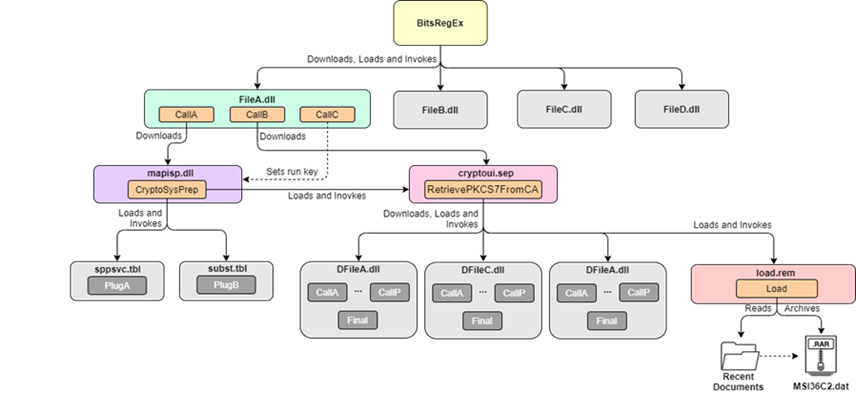
MosaicRegressor features several downloaders and, at times, multiple intermediary loaders whose end goals are to download and execute malicious payloads on targets’ machines.
“The fact that the framework consists of multiple modules assists the attackers to conceal the wider framework from analysis, and deploy components to target machines only on demand,” Kaspersky explains.
“Indeed, we were able to obtain only a handful of payload components during our investigation.”
While Kaspersky only obtained a limited number of the malware framework’s components, at least one of them used by the BitsRegEx bootkit variant was used for stealing, archiving, and exfiltrating to contents of the Recent Documents folder.
This UEFI rootkit is a custom version of Hacking Team’s VectorEDK bootkit, leaked in 2015, which likely allowed the MosaicRegressor developers to spend a lot less time creating it and to greatly narrow their risk of exposure.
Also Read: What Is A Governance Framework? The Importance And How It Works
Several MosaicRegressor components were found on the computers of several dozen organizations including NGOs and diplomatic entities from Africa, Asia, and Europe between 2017 and 2019.
“Based on the affiliation of the discovered victims, we could determine that all had some connection to the DPRK, be it non-profit activity related to the country or actual presence within it,” the reports reads.
“This common theme can be reinforced through one of the infection vectors used to deliver the malware to some of the victims, which were SFX archives pretending to be documents discussing various subjects related to North Korea.”
“Unfortunately, we were not able to determine the exact infection vector that allowed the attackers to overwrite the original UEFI firmware. Our detection logs show that the firmware itself was found to be malicious, but no suspicious events preceded it.”
One possibility outlined by Kaspersky is via physical access to the compromised machines and using a dedicated update tool to inject malicious code while booting the targeted device from a USB flash drive.
Another option would be that the bootkit was deployed remotely by first compromising the BIOS update authentication process after exploiting BIOS vulnerabilities.
Kaspersky’s full report (technical details included) on the multi-stage and modular MosaicRegressor UEFI bootkit can be found here (PDF).
Also Read: Data Protection Framework: Practical Guidance for Businesses