KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new ransomware vaccine program has been created that terminates processes that try to delete volume shadow copies using Microsoft’s vssadmin.exe program,
Every day, Windows will create backups of your system and data files and store them in Shadow Volume Copy snapshots.
These snapshots can then be used to recover files if they are mistakenly changed or deleted.
As ransomware infections do not want victims to use this feature to recover files for free, one of the first things they do when executed is to delete all Shadow Volume copies on the computer.
One method of deleting Shadow Volumes is to use the following vssadmin.exe command:
vssadmin delete shadows /all /quietAlso Read: 6 Simple Tips on Cyber Safety at Home
This weekend, security researcher Florian Roth released the ‘Raccine’ ransomware vaccine that will monitor for the deletion of shadow volume copies using the vssadmin.exe command.
“We see ransomware delete all shadow copies using vssadmin pretty often. What if we could just intercept that request and kill the invoking process? Let’s try to create a simple vaccine,” Raccine’s GitHub page explains.
Raccine works by registering the raccine.exe executable as a debugger for vssadmin.exe using the Image File Execution Options Windows registry key.
Once raccine.exe is registered as a debugger, every time vssadmin.exe is executed, it will also launch Raccine, which will check to see if vssadmin is trying to delete shadow copies.
If it detects a process is using ‘vssadmin delete,’ it will automatically terminate the process, which is usually done before ransomware begins encrypting files on a computer.
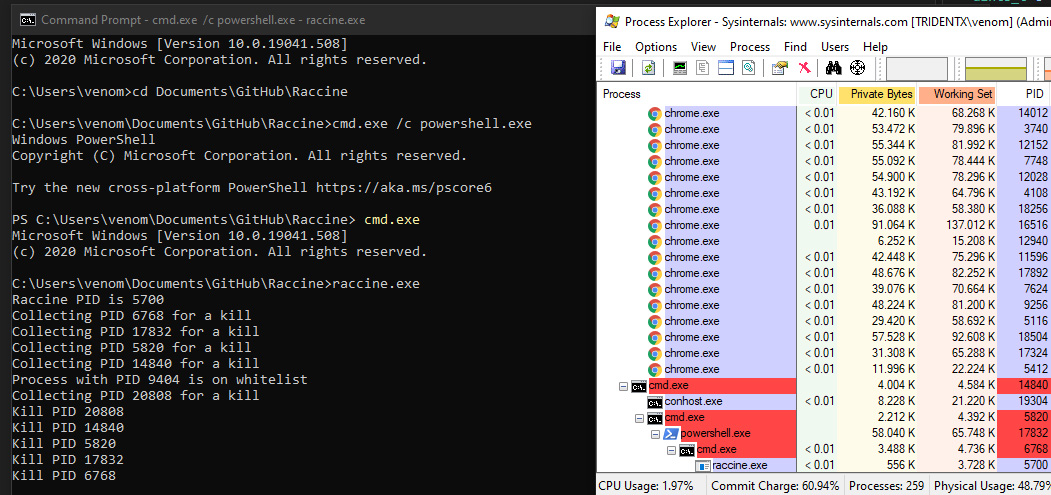
While this method will prevent encryption by a large amount of ransomware, some modern ransomware families delete shadow volumes using other commands, as listed below.
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$_.Delete();}
WMIC.exe shadowcopy delete /nointeractiveFor these ransomware variants, Raccine will not currently block the ransomware as they do not use vssadmin.exe. Support for these commands may be added in the future.
It should also be noted that Raccine may terminate legitimate software that uses vssadmin.exe as part of their backup routines.
Roth plans on adding the ability to allow certain programs to bypass Raccine in the future so that they are not mistakenly terminated.
To install Raccine, you can follow these steps:
Raccine is now registered as a debugger for the vssadmin.exe command monitors for attempts to delete shadow volume copies.
If you find that Raccine is terminating legitimate programs that you use, you can uninstall it by running the raccine-reg-patch-uninstall.reg registry file and deleting C:\windows\raccine.exe.
Once you uninstall Raccine, it will no longer terminate processes that attempt to delete shadow volume copies using vssadmin.exe.
Also Read: How To Delete Security Camera Footage: 5 Different Ways