KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







University Hospital New Jersey in Newark, New Jersey, paid a $670,000 ransomware demand this month to prevent the publishing of 240 GB of stolen data, including patient info.
The attack on the hospital occurred in early September by a ransomware operation known as SunCrypt, who infiltrates a network, steals unencrypted files, and then encrypts all of the data.
After the SunCrypt operators publicly posted an archive of 48,000 documents belonging to UHNJ, a representative of the hospital contacted the threat actors via their dark web payment portal to negotiate the stopping of any further publishing of patient data.
In a conversation seen by BleepingComputer between the hospital and the ransomware operators, we get a glimpse into the strangely cordial negotiation of a criminal ransom demand.
After a sample of the hospital’s private stolen data was published on SunCrypt’s data leak site, the hospital contacted the threat actors via their Tor payment site, where they were told that the ransom was $1.7 million. The attackers told them that this ransom, though, “is negotiable due to COVID-19 situation.”
As UHNJ only had two servers encrypted, they were more concerned about the releasing of patient’s data and were willing to pay a ransom to prevent it from being released any further.
“We want to prevent any further leakage of our data and that is why we are here talking with you,” UHNJ told the ransomware operator.
It is not entirely clear what information was contained in the stolen files, but the ransomware operators claimed to have “ID scans, DOB, SSN, illness type.”
After a series of back-and-forth negotiations, they agreed to a ransom of $672,744, or 61.90 bitcoins, and the hospital sent a payment to the given bitcoin address.
The bitcoin blockchain shows that 61.9 bitcoins were sent to the ransomware operation’s bitcoin address on September 19th.
After negotiations were completed, the ransomware operator told UHNJ, “You did a great job too. Our management owes us.”
As part of the negotiations, the ransomware operators agreed to provide a decryptor, all stolen data, a security report, and an agreement not to disclose any stolen data or attack UHNJ again.
According to the security report received by UHNJ, their network was compromised after an employee fell for a phishing scam and provided their network credentials.
Also Read: 4 Easy Guides To Data Breach Assessment
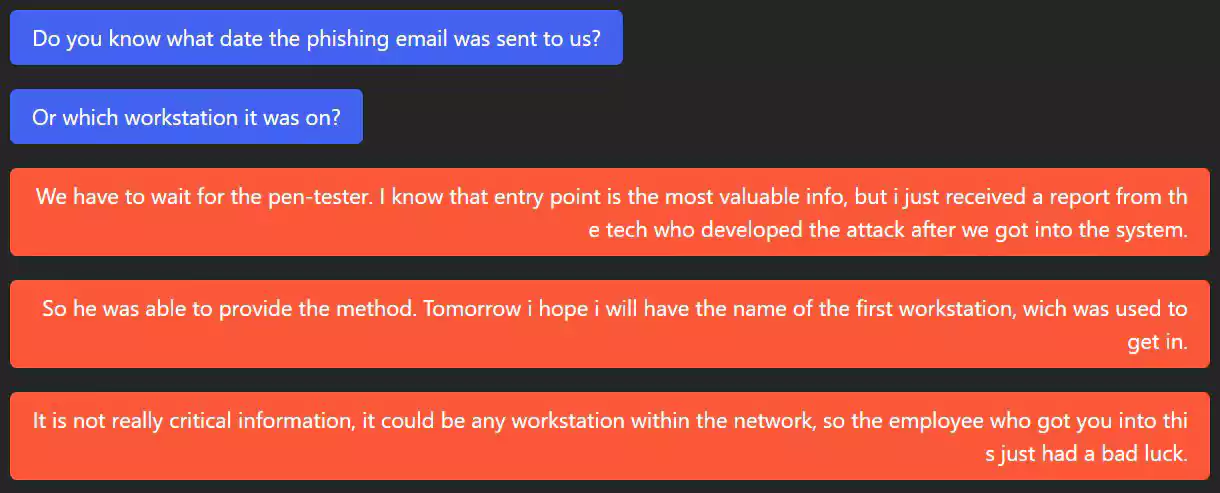
The ransomware operators then used these stolen network credentials to log in to UHNJ’s Citrix server and gain access to the network.
BleepingComputer has contacted UHNJ via phone and email for comment before publishing this article but did not receive a response.
In March, as the Coronavirus pandemic was surging worldwide, BleepingComputer contacted different ransomware operations to see if they would attack healthcare and medical organizations.
The CLOP, DoppelPaymer, Maze, and Nefilim ransomware operators stated that they would not target hospitals and decrypt for free any encrypted by mistake.
Netwalker ransomware was the only one who responded that any organization, including an encrypted hospital, would have to pay.
Data breach journalist ‘Dissent Doe’ of Databreaches.net recently reported that they contacted SunCrypt after noticing UHNJ’s data was removed from the ransomware data leak site.
In a conversation, the SunCrypt ransomware operators told Dissent Doe that they would no longer target healthcare organizations.
“We don’t play with people’s lives. And no further attacks will be carried against medical organizations even in this soft way,” SunCrypt told databreaches.net.
Unfortunately, this comes too late for UHNJ.
Also Read: Privacy Policy Template Important Tips For Your Business