KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Grindr has fixed a security flaw that could have allowed attackers to easily hijack any Grindr account if they knew the user’s email address.
Grindr is a social networking platform for gay, bi, trans, and queer people active since its launch in 2009, with roughly 4.5 million daily active users from countries all over the world.
French security researcher Wassime Bouimadaghene who discovered the vulnerability asked for Troy Hunt’s help to get reach out to Grindr after he unsuccessfully tried to report it through multiple channels.
Once Hunt asked for a Grindr security contact on Twitter, within about 90 minutes, the company quickly addressed the flaw blocking future account takeover attempts using the same attack technique.
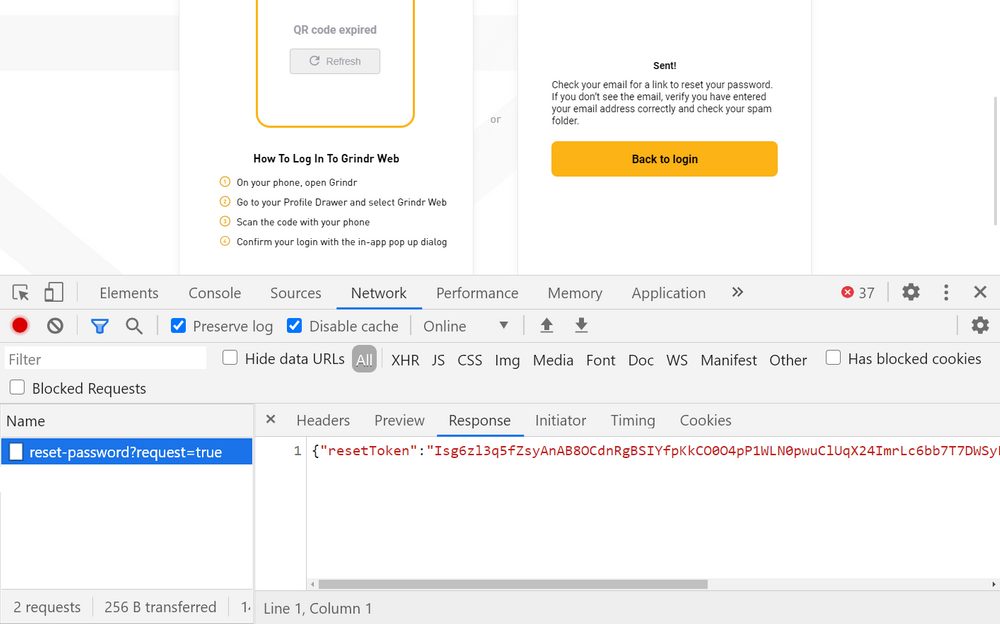
As Hunt was able to confirm, the reset token generated when resetting an account’s password could be obtained using the web browser’s dev tools as it was leaked in the page response content.
This made it possible to manually generate the unique link users’ would otherwise only receive via e-mail.
To find the template for that, one would only have to register a Grindr account and start the password reset process to get the reset email.
Using this technique, an attacker could reset the password and take over any Grindr account for which they knew the email.
Also Read: How Being Data Protection Trained Can Help With Job Retention
“This is one of the most basic account takeover techniques I’ve seen,” Hunt said in a blog post describing the now fixed issue. “I cannot fathom why the reset token – which should be a secret key – is returned in the response body of an anonymously issued request.”
“The ease of exploit is unbelievably low and the impact is obviously significant, so clearly this is something to be taken seriously,” he added.
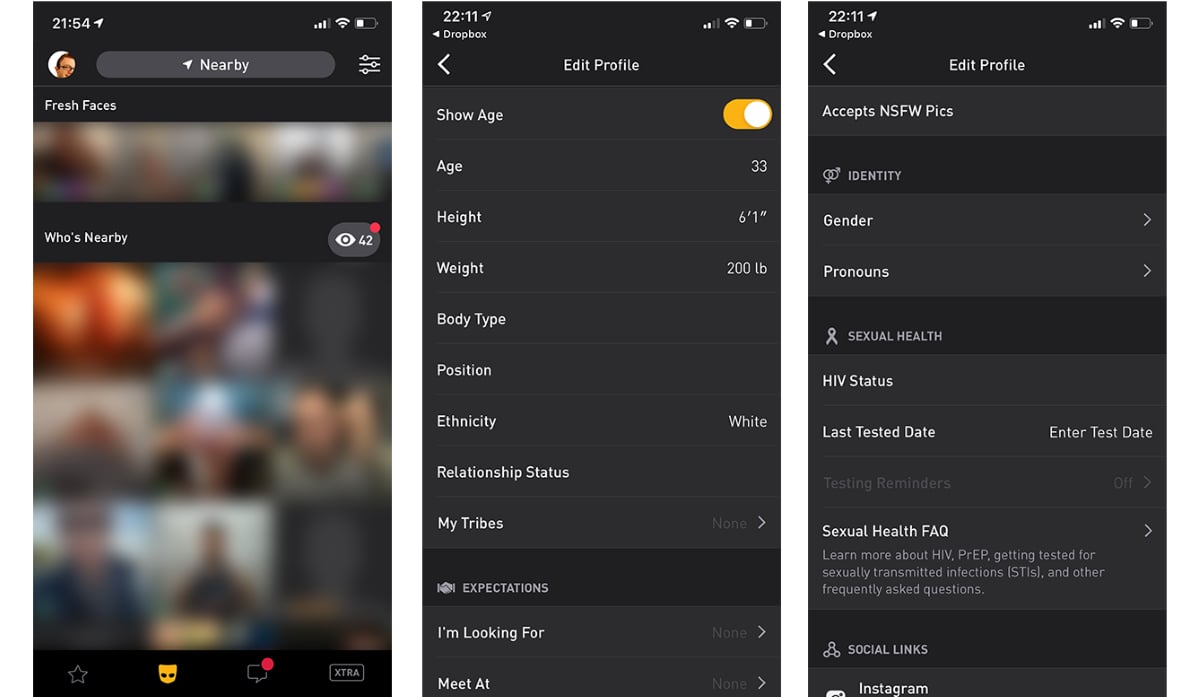
Once an attacker would take control of a Grindr user’s account using this flaw, he would have access to all the data stored within that account including but not limited to messages, HIV infection status, and personal photos, through the Grindr mobile and web app.
After fixing the security issue, Grindr told TechCrunch that they are working on making it easier for researchers to report such issues and that a new bug bounty program is in the works.
“We are grateful for the researcher who identified a vulnerability. The reported issue has been fixed. Thankfully, we believe we addressed the issue before it was exploited by any malicious parties,” Grindr said in a statement.
“As part of our commitment to improving the safety and security of our service, we are partnering with a leading security firm to simplify and improve the ability for security researchers to report issues such as these.
“In addition, we will soon announce a new bug bounty program to provide additional incentives for researchers to assist us in keeping our service secure going forward.”
BleepingComputer has also reached out to Grindr for comment but had not heard back at the time of this publication.
Three years ago, Norwegian independent research organization SINTEF discovered that Grindr shared users’ personal information (including HIV status, GPS location, email address, and more) with third parties (Apptimize and Localytics) via the iOS and Android apps.
The company’s head of security later said that Grindr has stopped sharing the sensitive info and that it all happened because of a simple misunderstanding of what was actually being shared with third-party vendors.
Also Read: Going Beyond DPO Meaning: Ever Heard Of Outsourced DPO?