KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







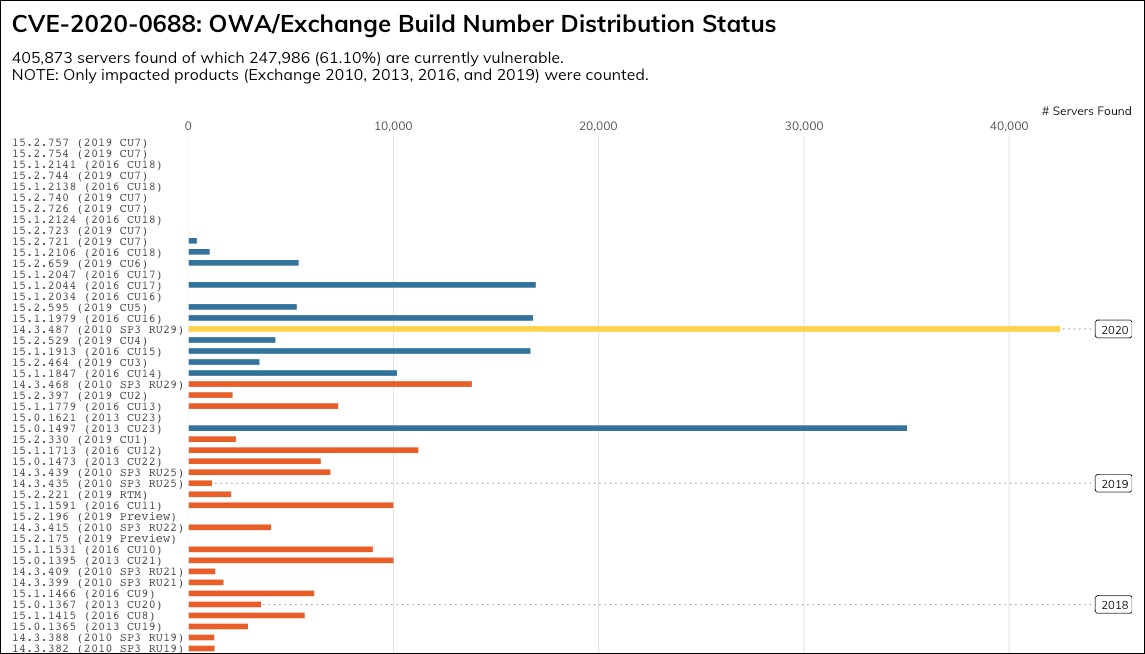
More than 247,000 Microsoft Exchange servers are yet to be patched against the CVE-2020-0688 post-auth remote code execution (RCE) vulnerability impacting all Exchange Server versions under support.
The CVE-2020-0688 RCE flaw exists in the Exchange Control Panel (ECP) component — enabled in default configurations — and it enables potential attackers to remotely take over vulnerable Exchange servers using any valid email credentials.
Microsoft addressed the security issue as part of the February 2020 Patch Tuesday and tagged it with an ‘Exploitation More Likely’ exploitability index assessment, suggesting that the vulnerability is an attractive target for attackers.
Cyber-security firm Rapid7, added an MS Exchange RCE module to the Metasploit penetration testing framework it develops on March 4, after several proof-of-concept exploits surfaced on GitHub.
One week later, both CISA and the NSA urged organizations to patch their servers against the CVE-2020-0688 flaw as soon as possible given that multiple APT groups were already actively exploiting it in the wild.
In an update to a previous report on the number of exposed Exchange servers vulnerable to attacks attempting to exploit the CVE-2020-0688 vulnerability, Rapid7 once again made use of its Project Sonar internet-wide survey tool for another headcount.
And the numbers are almost as grim as they were before, with 61.10% (247,986 out of a total of 405,873) of vulnerable servers (i.e., Exchange 2010, 2013, 2016, and 2019) still being left unpatched and exposed to ongoing attacks.
The company’s researchers found that 87% of almost 138,000 Exchange 2016 servers and 77% of around 25,000 Exchange 2019 servers were left exposed to CVE-2020-0688 exploits, and that roughly 54,000 Exchange 2010 servers “have not been updated in six years.”
Rapid7 also discovered 16,577 Exchange 2007 servers reachable over the Internet, an unsupported Exchange version that did not receive security updates to protect against CVE-2020-0688 attacks.
Also Read: Free 8 Steps Checklist for Companies to Prevent Data Breach
“There are two important efforts that Exchange Administrators and infosec teams need to undertake: verifying deployment of the update and checking for signs of compromise,” Rapid7 Labs senior manager Tom Sellers explains.
Compromised accounts used in attacks against Exchange servers can easily be discovered by checking Windows Event and IIS logs for parts of encoded payloads including the “Invalid viewstate” text or the __VIEWSTATE and __VIEWSTATEGENERATOR strings for requests to a path under /ecp (usually /ecp/default.aspx).
As Microsoft said that there are no mitigation measures for the CVE-2020-0688 vulnerability, the only choice left is to patch servers before attackers find them and fully compromise the entire network they’re on — unless admins have the time and are willing to reset all accounts’ passwords to render previously stolen credentials worthless.
Direct download links to security updates you need to install to patch vulnerable Microsoft Exchange Server versions and the related KB articles are listed in the table below:
| Product | Article | Download |
| Microsoft Exchange Server 2010 Service Pack 3 Update Rollup 30 | 4536989 | Security Update |
| Microsoft Exchange Server 2013 Cumulative Update 23 | 4536988 | Security Update |
| Microsoft Exchange Server 2016 Cumulative Update 14 | 4536987 | Security Update |
| Microsoft Exchange Server 2016 Cumulative Update 15 | 4536987 | Security Update |
| Microsoft Exchange Server 2019 Cumulative Update 3 | 4536987 | Security Update |
| Microsoft Exchange Server 2019 Cumulative Update 4 | 4536987 | Security Update |
Also Read: The Impact of GDPR and PDPA in Singapore