KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Researchers have released exploits for the Windows Zerologon CVE-2020-1472 vulnerability that allow an attacker to take control of a Windows domain. Install patches now!
As part of the August 2020 Patch Tuesday security updates, Microsoft fixed a critical 10/10 rated security vulnerability known as ‘CVE-2020-1472 | Netlogon Elevation of Privilege Vulnerability’.
After successfully exploiting this vulnerability, attackers are able to elevate their privileges to a domain administrator and take over a domain.
Since then, cybersecurity firm Secura, who discovered this vulnerability, has released a detailed writeup of the vulnerability and named Zerologon.
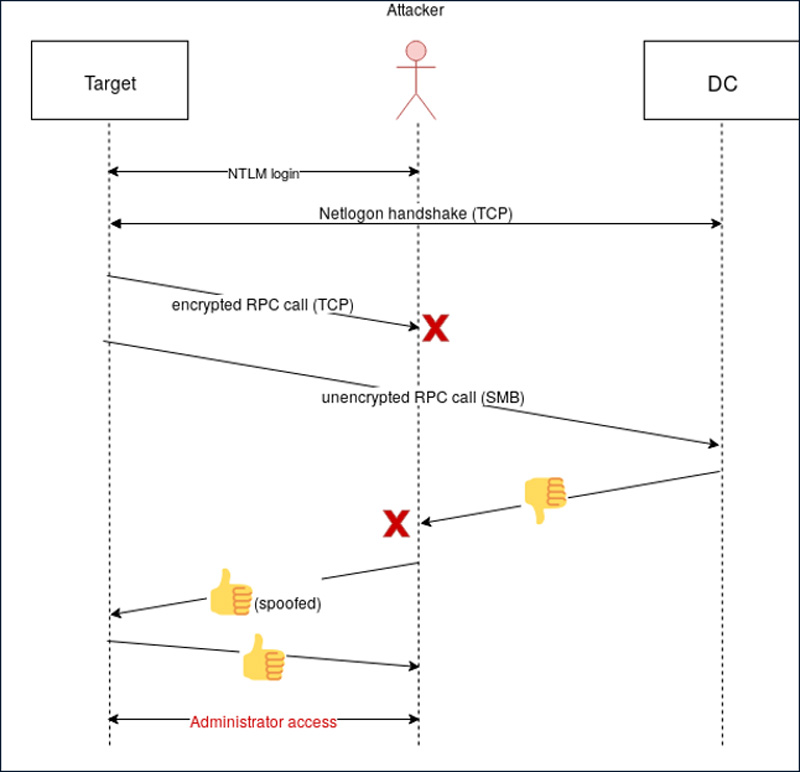
When a user logs into a Windows device on a domain, it uses the the Netlogon Remote Protocol (MS-NRPC) over RPC to communicate with the domain controller and authenticate the user.
If a user logs in with the correct credentials, the domain controller tells the device to allow authentication with the appropriate permissions. Those with wrong credentials will obviously not be able to log in.
As the authentication attempts are sensitive, Windows sends the authentication requests over an encrypted, secure RPC connection
Secura researcher Tom Tervoort discovered that is is possible to force domain controllers to fall back to unencrypted RPC communication when performing authentication requests.
After falling back to non-secure RPC communication, Tervoort could abuse a flaw in the Netlogon AES-CFB8 cryptographic negotiation algorithm to try and spoof a successful login.
In Tervoort’s tests, it would take an average of 256 attempts to spoof a successful login successfully.
This manipulation would trick the device to log the user into the system as a domain administrator.
Also Read: Website Ownership Laws: Your Rights And What It Protects
Once an attacker gains domain administrator privileges on the network, they get full access to the domain controller, can change users’ passwords, and execute any command they wish.
What makes this vulnerability so scary is that an attacker does not even need legitimate credentials on the domain, but can spoof the responses to cause any login attempt to be successful.
“It would not be necessary to wait for some other user to attempt to log in. Instead, the attacker can login themselves, pretending to only support NTLM and providing some invalid password. The service they are logging in to will forward the NTLM handshake to the domain controller and the domain controller would reply with a negative response. This message could then be replaced by a spoofed reply (also containing a recalculated session key) indicating that the password was correct and, by the way, the user trying to log in happened to be a member of the domain admin group (meaning they also have administrative privileges on the target machine),” Tervoort explains in his report on Zerologon.
This vulnerability is especially concerning when it comes to human-operated ransomware attacks as it allows an adversary with a foothold on a single workstation to gain full control of a network over a Windows domain.
“This vulnerability can be particularly dangerous when an attacker has a foothold in an internal network because it allows for both elevation of privileges (to local admin) and lateral movement (gaining RCE on other machines on the network),” Tervoort warned.
Since the release of Secura’s writeup, numerous researchers have released proof-of-concept exploits that allow a user to gain domain administrator privileges on a vulnerable network.
Rich Warren of NCC Group released a PoC yesterday that allowed him to achieve domain admin in ten seconds.
Researchers have released additional exploits [1. 2] that perform similar attacks on domain controllers.
Also Read: Data Protection Authority GDPR: Everything You Need To Know
As fixing the Zerologon vulnerability can cause some devices to not properly authenticate, Microsoft is rolling out the fix in two stages.
The first stage was released on August 11th in the form of a security update that will prevent Windows Active Directory Domain controllers from using unsecured RPC communication.
This update will also log authentication requests from non-Windows devices that do not use secure RPC communication to allow administrators time to fix the devices or replace them with hardware that supports secure RPC.
On February 9th, 2021, as part of the Patch Tuesday updates, Microsoft will release a second update that will enter the enforcement phase that requires all devices on the network to use secure-RPC, unless specifically allowed by an administrator.
Due to this, it is strongly advised that Windows administrators deploy the first stage of the patch on their Active Directory Domain controller to protect their network.
Secura has released a tool that allows you to check if your domain controller is vulnerable to the Zerologon (CVE-2020-1472) vulnerability.