KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!






Threat researchers investigating phishing attacks encountered a less common technique in spear-phishing aimed at a senior executive at a top American company.
The code behind the phishing page made sure that the threat actor got the right credentials for the company Active Directory and performed redirects to hide the attempt.
Also read: 10 Government Data Leaks In Singapore: Prevent Cybersecurity
Testing logins in real-time is an unusual technique that allows the attacker to adapt their response based on the received feedback.
The attack started with an email delivered on a Friday, at the end of business hours, with a subject and attachment referring to an internal financial report. A short message informs of a payment remittance report being available.
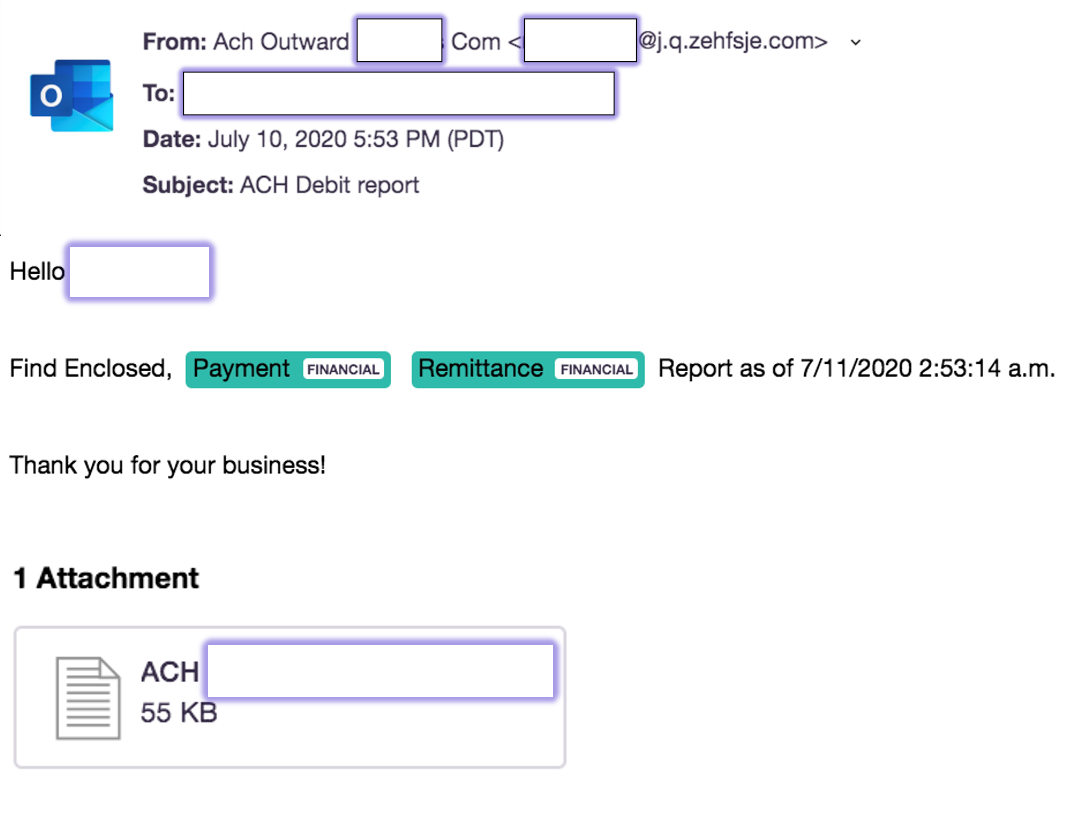
Opening the attachment launches a web page that looks like the legitimate Office 365 login page. This method is convenient for bypassing typical URL protection from Secure Email Gateway solutions.
A clue to the targeted nature of the attack is the fact that a recent rebranding effort from the company resulted in different email addresses used for communication and Active Directory (AD) authentication.
It appears that the threat actor was aware of this detail. They sent the phishing email to the correct address and filled the right AD username in the fake Office 365 login field on the landing page.
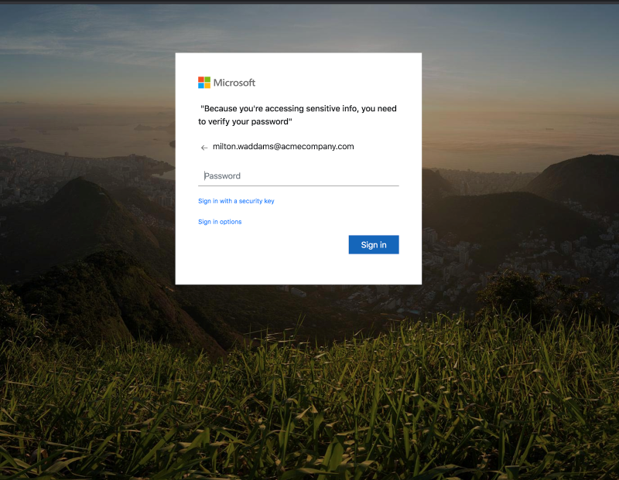
Researchers at Armorblox, a company protecting against targeted email attacks, analyzed the phishing attempt and noticed that the hackers verified the credentials immediately after getting them using Office 365 APIs.
The researchers confirmed this by testing mock credentials on the phishing page. The attempt appeared in the logs for the Azure Active Directory.
“Our threat researchers verified the real-time nature of the site by updating the script with a test login and a dummy password and saw a failed login attempt from Provo, Utah in the Azure Active Directory Sign-In portal. As expected, the IP address (162.241.120.106) that attempted the sign-in is the same endpoint the phishing script sends the credentials” – Armorblox
The attackers also made sure to scatter their traces as much as possible to make tracking them more difficult. As such, their infrastructure used serviced from all over the world,
They used the Amazon Simple Email Service to send out the phishing message, registered the domain for the phishing page at Alibaba with a domain registrar in Singapore, and hosted the website at a datacenter in Provo, Utah, operated by a provider in India (UnifiedLayer).
Using Amazon SES to deliver the email kept spam alarms silent since the service supports DKIM/SPF, increasing the reputation of the message.
In their blog post today, ArmorBlox says that checking the validity of the logins for Active Directory authentication allows the attacker to adapt their next step; and if successful, they can compromise the account before any remediation action, establishing a foothold that could makes cleaning operations more difficult.
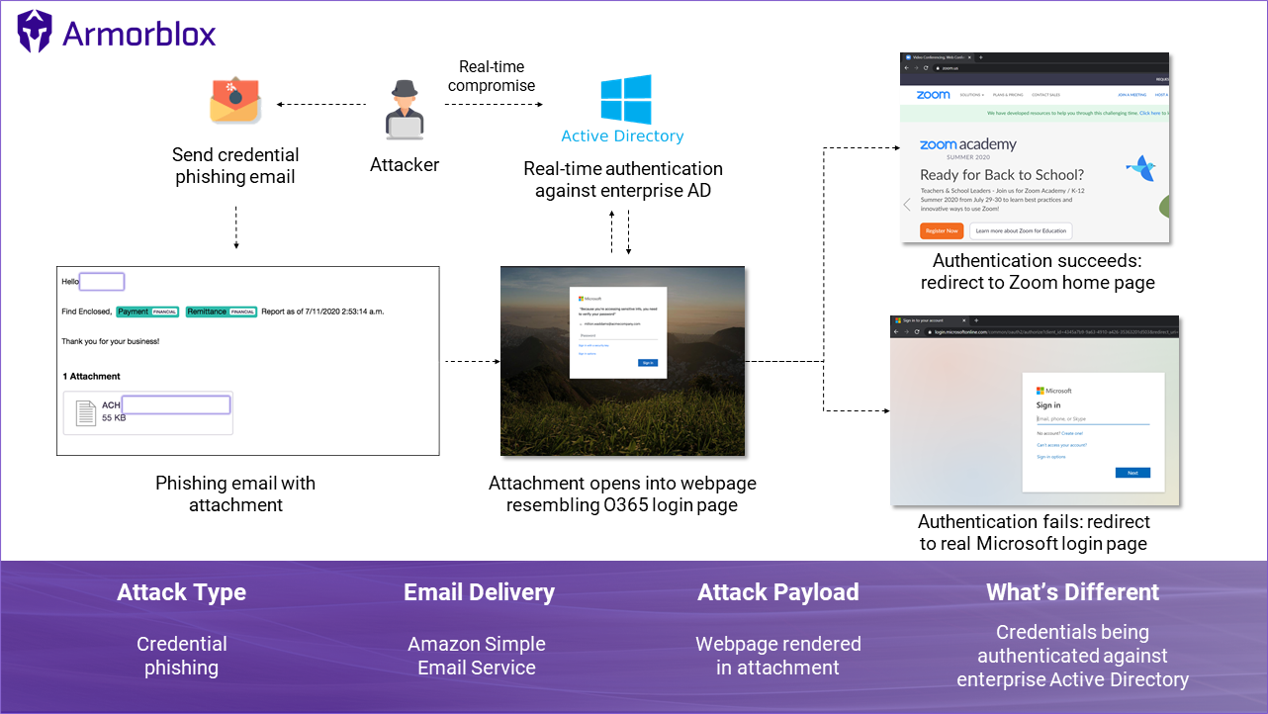
They summarized the complete chain of attack in the following picture:
Also read: How To Anonymised The Data: What Are The Importance Of This?