KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





Image: Cado Security
In a recent attack, cybercrime group TeamTNT relied on a legitimate tool to avoid deploying malicious code on compromised cloud infrastructure and still have a good grip on it.
They used an opensource tool specifically created to monitor and control cloud environments with Docker and Kubernetes installations, thus reducing their footprint on the breached server.
Analyzing the attack, researchers at Intezer discovered that TeamTNT installed Weave Scope open-source tool to gain full control of the victim’s cloud infrastructure.
According to them, this may be the first time a legitimate third-party tool is abused to play the part of a backdoor in a cloud environment, also indicating the evolution of this particular group.
Weave Scope integrates seamlessly with Docker, Kubernetes, and the Distributed Cloud Operating System (DC/OS), and AWS Elastic Compute Cloud (ECS). It provides a complete map of processes, containers, and hosts on the server and control over installed applications.
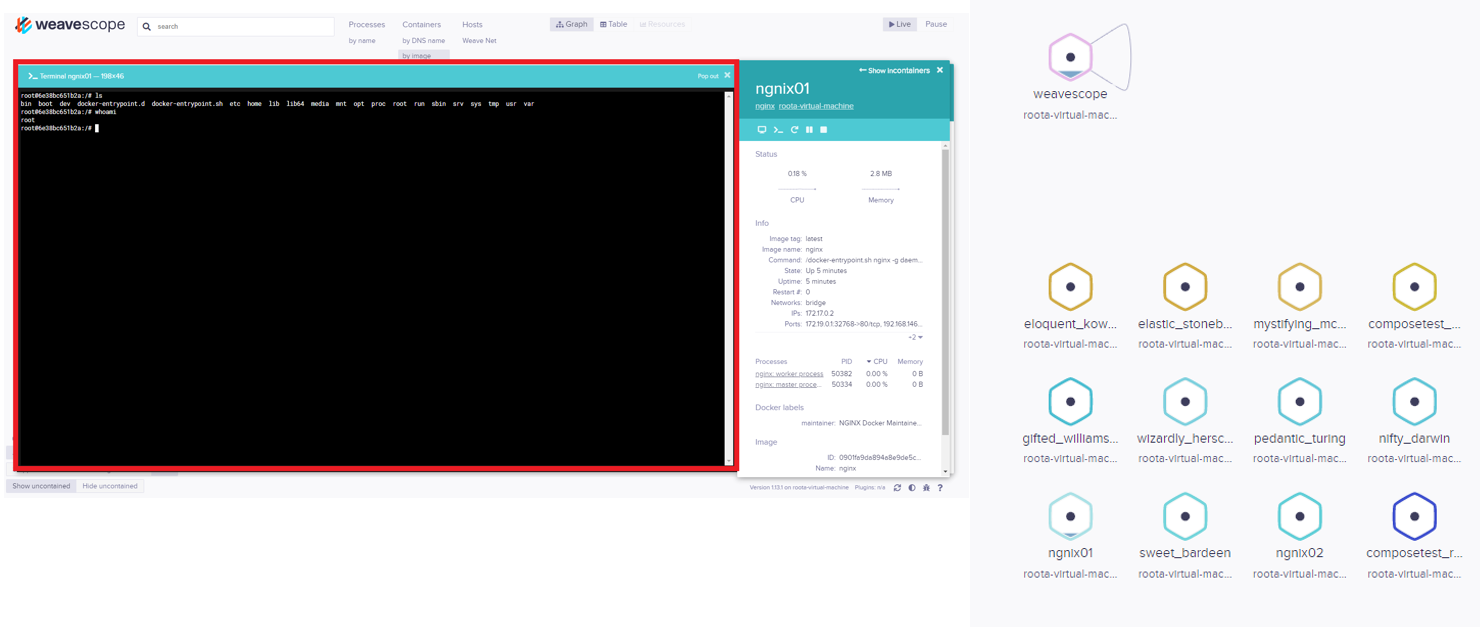
“The attackers install this tool in order to map the cloud environment of their victim and execute system commands without deploying malicious code on the server,” Intezer notes in a report today.
Also read: Personal Data Websites: 3 Things That You Must Be Informed
Describing the attack flow from the incident, the researchers say that TeamTNT’s way in was an exposed Docker API. This allowed them to create a clean Ubuntu container configured to mount on the victim server, thus gaining access to files on the host.
Then they set up a local user named ‘hilde’ with elevated privileges and use it to connect to the server via SSH. Installing Weave Scope is the next step in the attack, which requires just three commands to download, set permission over the Scope app, and launch.
With the utility on the server, TeamTNT could connect to the Weave Scope dashboard via HTTP on port 4040 (default for the Scope app endpoint) and take control.
The researchers say this scenario, although rare, could have been prevented if the Docker API ports were closed or restricted access policies were in place.
Another misconfiguration is allowing connections to the Weave Scope dashboard from outside the network. The documentation for the tool is clear about not making port 4040 accessible over the internet.
TeamTNT emerged on security researchers’ radar in early May as a cryptomining group, when MalwareHunterTeam tweeted about it and Trend Micro revealed that the attackers scanned the internet for open Docker daemon ports.
Last month, U.K.-based company Cado Security published a report with evidence that TeamTNT’s cryptomining worm could also steal AWS credentials and configuration files from Docker and Kubernetes instances.
Also read: Computer Misuse Act Singapore: The Truth And Its Offenses