KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has confirmed that they no longer allow Microsoft Defender to be disabled via the Windows 10 Registry to support the Tamper Protection security feature.
When Windows 10 1903 was released, it introduced a new security feature called Tamper Protection that prevents Windows Security and Microsoft Defender settings from being changed outside of the Windows interface.This includes command-line tools, Registry changes, or group policies.
Windows users have historically been able to disable Microsoft Defender using the ‘Turn off Microsoft Defender Antivirus’ group policy.
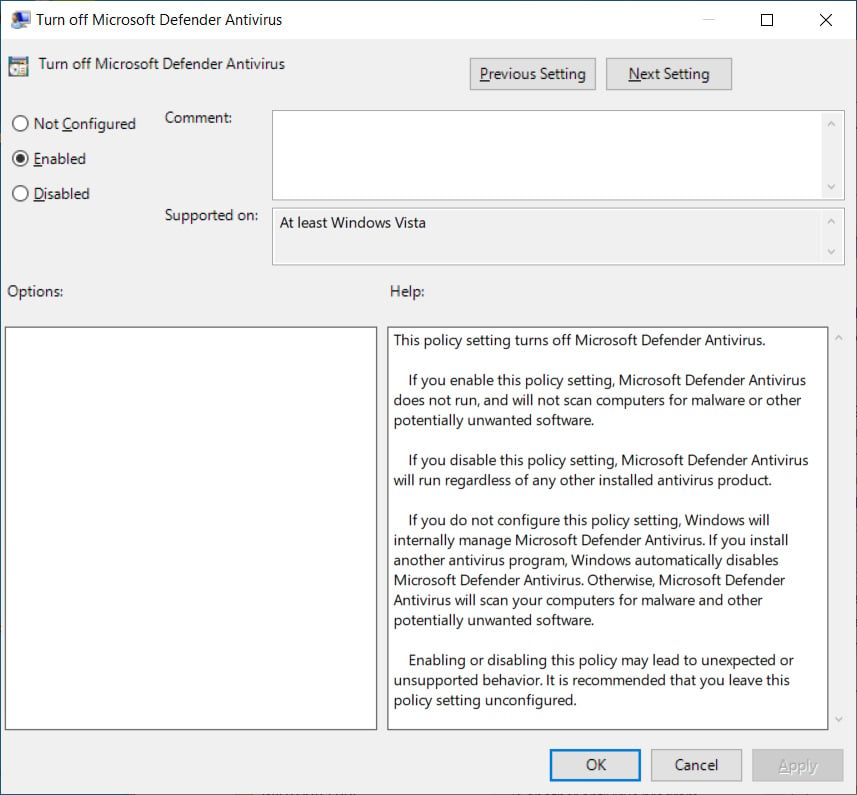
Once enabled, a ‘DisableAntiSpyware’ Registry value is created and set to 1 under the HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender key.
Earlier this month, we reported that Microsoft Defender would no longer honor this Registry value as it is no longer needed, and Tamper Protection protects it anyway.
“This is a legacy setting that is no longer necessary as Microsoft Defender antivirus automatically turns itself off when it detects another antivirus program.”
“Note that this setting is protected by tamper protection. Tamper protection is available in all Home and Pro editions of Windows 10 version 1903 and higher and is enabled by default,” Microsoft added to the support documentation for DisableAntiSpyware.
Microsoft’s statements were not the whole story as extensive testing by BleepingComputer showed that even with Tamper Protection enabled, the DisableAntiSpyware Registry value still worked briefly.
When enabled, if a malware rebooted the computer, Microsoft Defender would be disabled for that particular session. On the next reboot, Tamper Protection would kick in and enable Windows Defender again.
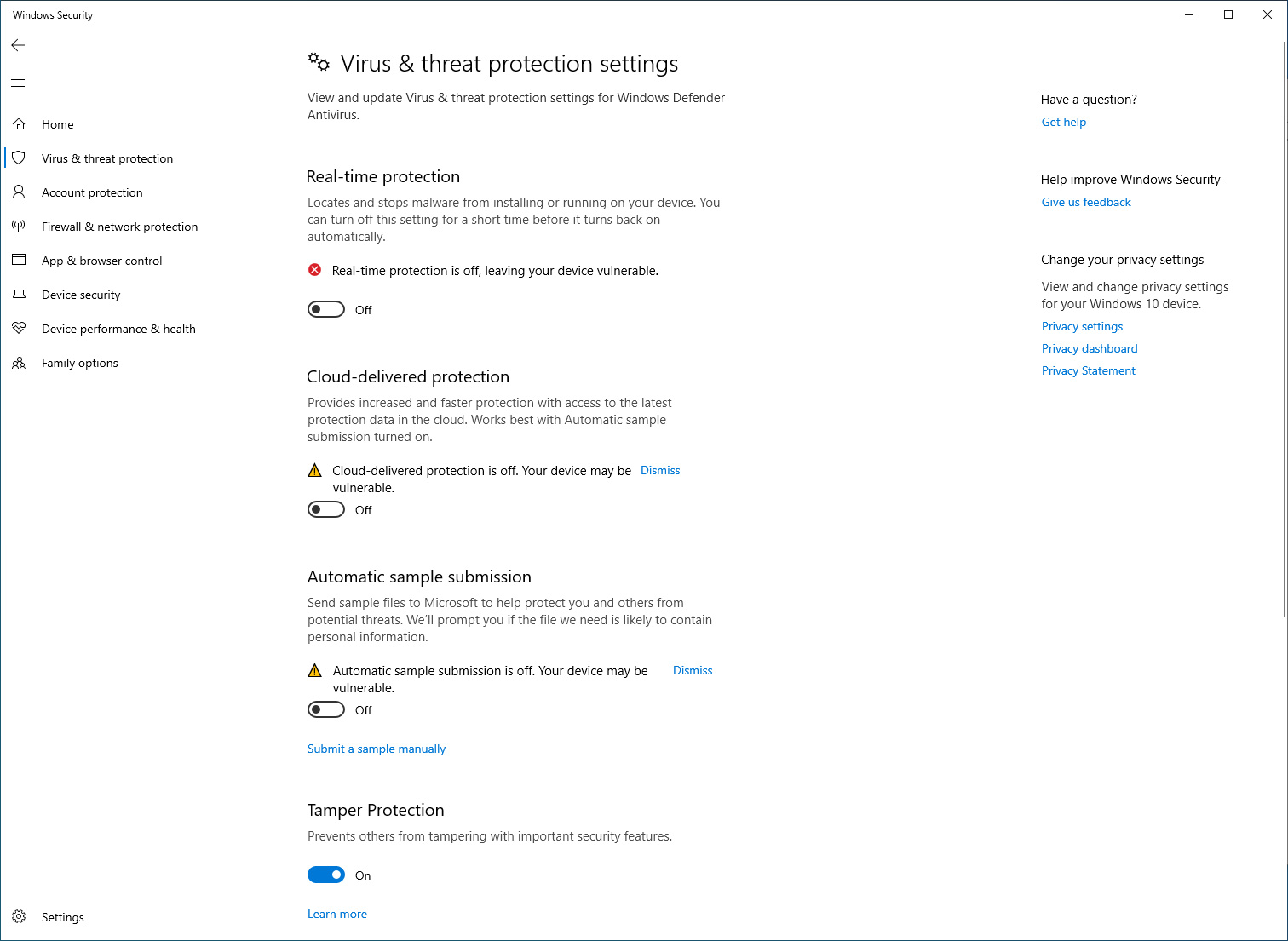
This brief lapse of protection, though, is all that malware needs to infiltrate a Windows computer.
We have reported on numerous infections, including TrickBot, Novter, Clop Ransomware, Ragnarok Ransomware, and AVCrypt Ransomware who have specifically targeted Microsoft Defender by disabling it using the ‘DisableAntiSpyware’ Registry value.
Due to this, BleepingComputer believes that Microsoft removed this policy not only as it is not needed, but also to prevent attackers from exploiting this brief hole in Tamper Protection.
Also read: How Bank Disclosure Of Customer Information Work For Security
In an update to the Windows 10 Message Center, Microsoft has confirmed our suspicions that the DisableAntiSpyware policy is now ignored to support Tamper Protection.
Supporting tamper protection through the deprecation of DisableAntiSpyware
Microsoft Defender Antivirus tamper protection is turned on by default for all consumer Windows 10 devices. This feature protects devices from cyber attacks that try to disable built-security solutions, such as antivirus protection, in an attempt to gain access to your data, to install malware, or to otherwise exploit your data, identity, and devices. As Microsoft Defender antivirus automatically turns itself off when it detects another antivirus program, we are removing a legacy registry setting called DisableAntiSpyware. Intended to be used by OEMs and IT admins to disable Microsoft Defender Antivirus for the purpose of deploying another antivirus product during deployment, DisableAntiSpyware is not applicable to consumer devices and will be removed beginning with Microsoft Defender Antimalware platform versions 4.18.2007.8 and higher (see KB4052623 for details). This update will be rolled out to devices running Windows Enterprise E3 and E5 at a future date.
With the DisableAntiSpyware policy removed, malware can no longer exploit the weakness in TamperProtection, and Microsoft Defender will only be disabled when done so via the Windows settings or when another antivirus software is installed.
Also read: 7 Simple Tips On How To Create A Good Business Card Data