KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





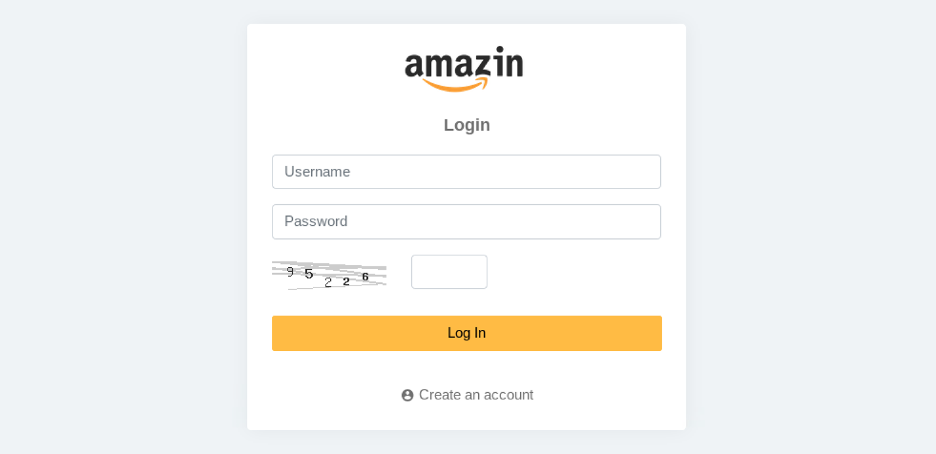
The most notable characteristic of the darknet marketplace Amazin is that the administrator is committing outright copyright infringement by unlawfully using Amazon’s intellectual property in their branding. In addition to cloning Amazon’s official logo and replacing the “o” with an “i,” (Amazon -> Amazin), the administrator of Amazin Market has also poached other branding characteristics from Amazon’s official website.
For example, the marketplace admin has laid the cloned spin-off logo on top of the exact same quintessential charcoal color that Amazon features on its website. The admin has also situated a white shopping cart in the top-right hand corner of the market, much like Amazon’s actual interface.
Amazin Market has a relatively intuitive user interface and customer support system, that continues to mirror Amazon’s both visually and navigationally. The market also heralds a robust vendor rating and review system. Referred to as a supplier rating, it measures the performance of darknet vendors on Amazin Market on an ongoing basis, as well as provides buyers on Amazin Market with the opportunity to make better purchasing decisions.

While Amazin market may look like Amazon from a visual perspective, the merchandise one can find being sold there is a major departure from the kitchenware and back-to-school supplies you’ll find on Amazon. Instead, Amazin market carries exclusively illicit supplies, such as hacked accounts and e-gift card codes.
Amazin Market appears to principally feature financial-related goods and services. Vendors on Amazin Market are currently advertising for sale hacked Amazon, JPMorgan and PayPal accounts, as well as compromised iTunes, Amazon, Google Play and GameStop e-gift card codes, sometimes 70-80% off face value.
In addition to hijacked accounts and e-gift card codes, vendors on Amazin Market are also advertising for sale money laundering services using PayPal, Payoneer and Western Union.
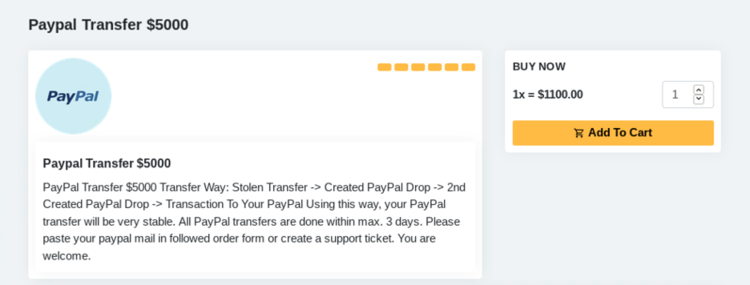

Of significance, DarkOwl discovered that one vendor is responsible for trafficking all of the stolen payment card information through Amazin Market. Known as ‘HQDumps,’ the vendor is selling ‘dumps,’ hacker-slang for stolen payment card information that can be used to conduct in-store card fraud.
After reviewing and analyzing all of HQDumps’s listings, DarkOwl was able to determine that HQDumps is currently selling financial details that belong to victims that reside around the world, particularly in the United States, Europe, Australia and Asia.
Also read: Understanding The Data Intermediary In Data Protection
Key things to know about Amazin Market
7 vendors currently operate on Amazin Market. The names of those vendors include, amazin, JPMorgan, RedBull, Babo, Patron, Joker and HQDumps. After reviewing all of HQDumps’s vendor reviews on Amazin Market, DarkOwl uncovered that HQDumps used to be a vendor on the Silk Road. It remains unknown what version of the Silk Road HQDumps was affiliated with, whether the original or post-Ulbricht versions.
DarkOwl also found that HQDumps used to be a member of the “MasterGroupOfSpam,” a Telegram Channel inhabited by 9,700+ cybercriminals involved in various criminal activities, primarily hacking and card fraud. It is important to note that HQDumps has not operated on Telegram (HQ DUMPS @ HQDUMPS) since late May.
Differentiating itself from other darknet markets, such as Infinity Market, Amazin Market does not reveal the precise number of stolen goods that each and every vendor is advertising. This feature may have been implemented in an effort to better protect Amazin Market’s vendors, as law enforcement agencies have been known to prioritize vendors by the sheer volume of illicit goods that they are individually offering.
Contrary to other darknet markets, Amazin Market only supports Bitcoin as a means of payment. At this time, DarkOwl has not observed any darknet forum chatter or related scrutiny related to this payment limitation.
Amazin Market, like so many other markets on the darknet, has an escrow system. Escrow systems serve as third party vehicles that hold funds until both sides of the transaction have been completed. It’s an important feature as it acts as a way to protect both buyer and vendors from getting scammed.
DarkOwl analysts noticed that Amazin Market is listed on Tor66, a darknet search engine on the Tor Network that advertises many known scam services. Interestingly, Amazin Market is also listed as a ‘scam market’ on Dark Web Magazine’s dark web scam list. These findings support why the admin has had a difficult time gaining traction amidst the criminal underground, even with a darknet marketing incentive of $30 USD (as pictured below).


DarkOwl discovered a darknet market known as MoneyPlus with the same source code, vendor community and user-interface as Amazin Market. DarkOwl uncovered that the administrator of MoneyPlus (additional and possible alias Amazin) can be reached via email at [email protected]. At this time, DarkOwl does not have definitive evidence whether Amazin Market and MoneyPlus Market are affiliated, and whether both markets are run by the same administrator.
Additional research efforts revealed that Amazin Market has a dual presence on the deep web (hxxps://amazin.to and hxxps://amazin.biz). After running a WHOIS and IP Geo lookup around both domains, the first domain was found to be registered on March 28, 2014. The domain was also found to be protected by Cloudflare and linked to the IP address of 104.31.81.229, a server located in Manila, Philippines. The second domain was found to be registered on December 17, 2012. In contrast, the domain was not found to be protected by Cloudflare, and is linked to the IP address of 192.64.119.87, a server located in Los Angeles, CA.
As such, the actual location of the marketplace’s servers, as well as the identity of the marketplace’s administrator, remain unclear.
Also read: How Being Data Protection Trained Can Help With Job Retention