KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The Dharma Ransomware-as-a-Service (RaaS) operation makes it easy for a wannabe cyber-criminal to get into the ransomware business by offering a toolkit that does almost everything for them.
A RaaS operation is a cybercrime model where the developers are in charge of managing the ransomware development and ransom payment system. At the same time, affiliates are responsible for compromising victims and deploying the ransomware.
As part of this model, the developers earn between 30-40% of any ransom payments, and the affiliates make the rest.
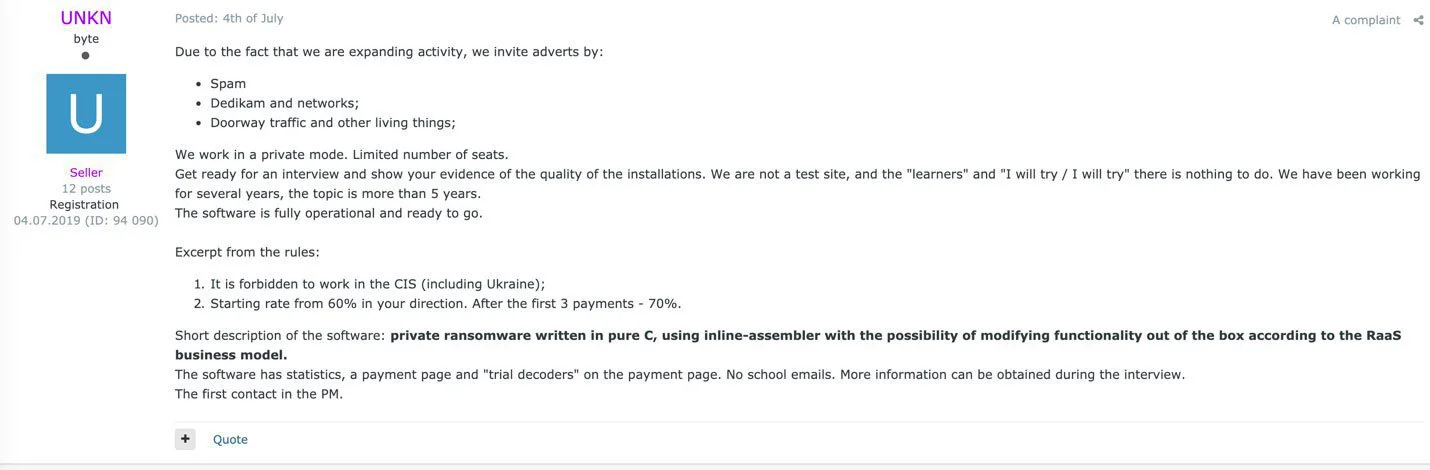
Most of today’s enterprise-targeting ransomware groups operate as a private RaaS model, where only the most talented hackers are invited to participate.
For example, the REvil RaaS requires all potential affiliates to be interviewed and show proof that they are experienced hackers.
One of the oldest ransomware families operating today is the Dharma ransomware.
Starting under the name CrySiS around March 2016, the master decryption keys were leaked in a post in the BleepingComputer forums in November 2016.
Soon after, a new variant of the ransomware was released that appended the .dharma extension to encrypted files. Since then, the family and its constant stream of new variants have been known as Dharma.
Unlike other large enterprise-targeting RaaS operations that demand a hundred thousand to million-dollar ransom demands, Dharma tends to be on the lower range with average demands at around $9,000.
Based on a new toolkit offered by the RaaS, its low price may reflect the low bar of entry required for affiliates.
New research from Sophos may explain why the ransom demands are so much lower for Dharma ransomware attacks than other operations; it caters to a less experienced affiliate.
Unlike many private RaaS operations that only work with experienced hackers, it has been discovered that the Dharma operators offer a ready-made toolkit that allows anyone wannabe hackers to compromise a network.
Known as ‘Toolbelt’, this toolkit is a PowerShell script that, when run, allows the attacker to download and execute a variety of tools from a mapped Remote Desktop shared ‘\\tsclient\e’ folder.
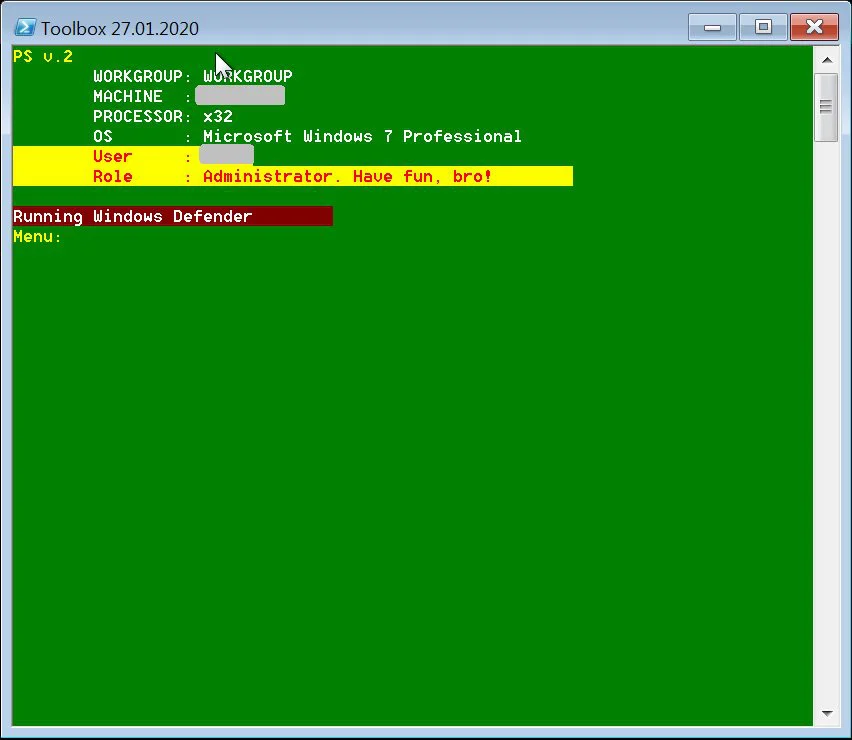
When using the toolkit, the affiliate would enter a number corresponding to one of 62 tasks that can be executed.
After entering the command, the toolkit would download the necessary executables from the Remote Desktop share and execute them.
Also read: 12 brief explanation about the benefits of data protection for business success
This toolkit allows the affiliate to spread laterally through a network with the help of tools like Mimikatz to harvest passwords, NirSoft Remote Desktop PassView to steal RDP passwords, Hash Suite Tools Free to dump hashes, and other tools to find computers to target and ultimately deploy the ransomware.
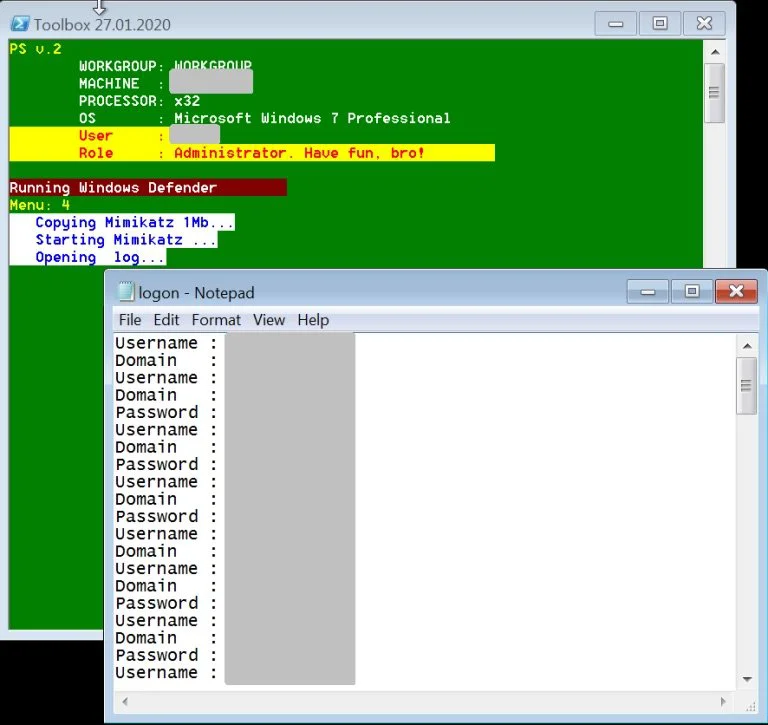
After obtaining the toolkit, BleepingComputer can confirm that it requires the affiliate’s Remote Desktop share to be properly set up and accessible for the commands to be executed properly.
This required remote share indicates that the toolkit is part of a larger package distributed by the RaaS.
For an inexperienced hacker, this toolkit contains all of the programs that the affiliate needs to steal passwords, spread to other machines on a network, and ultimately deploy the ransomware.
After analyzing the patterns of Dharma attacks, Sophos found that a group of affiliates commonly perform the following steps when using the toolkit:
“These cases were related to a single Dharma RaaS operator. We know there are multiple Dharma operators, but the multiple instances we found in this research using these scripts was tied to one specific RaaS with multiple sub-operators.”
“We don’t know if all of them use the same toolset, but we’ve seen the same pattern of attack across many, many Dharma attacks, so we believe they may all at least come from a single original source and are used widely,” Sophos researcher Sean Gallagher told BleepingComputer.
Sophos also believes that the RaaS provides documentation on using the toolkit to spread laterally through a network.
With a similar approach seen in numerous attacks, the documentation likely provides a set of steps that affiliates should use when deploying the ransomware.
By offering a toolkit and documentation on how to use it, Dharma can recruit more potential affiliates.
This larger pool of distributors allows them to cast a wide net to catch as many victims as possible, and what they lose in smaller ransoms, they make up in potentially more substantial volume of payments.
Also read: Top 25 Data Protection Statistics That You Must Be Informed