KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







The threat actor behind the Joker Android malware has once again succeeded to successfully slip spyware infected apps onto the Play Store, Google’s official Android app store.
Android applications infected with Joker malware, a spyware and premium dialer tool also known as Bread and tracked since 2017, were originally designed to perform SMS fraud.
More recently, Joker’s creators have moved to new tactics after Google introduced new Play Store policies which restrict the use of SEND_SMS permissions and increase Google Play Protect’s coverage.
Updated versions of this Android trojan now are used for a type of mobile billing fraud known as toll fraud. Through this new tactic, the Joker’s operators use malicious apps to trick their victims into subscribing to or buying various types of content via their mobile phone bill.
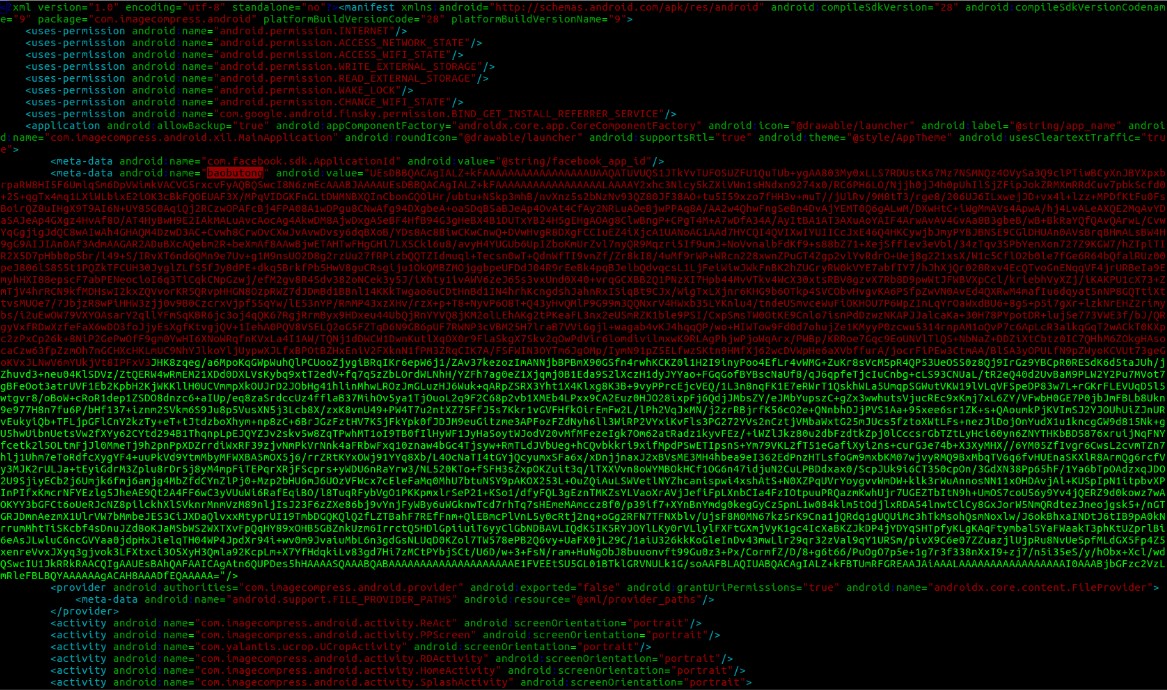
A new variant of Joker successfully slipped into the Play Store and infected Android users after hiding the malicious payload as a dex file hidden in the form o Base64 encoded strings within seemingly benign apps’ AndroidManifest files (used to provide Android build tools, the Android OS, and the Google Play Store with essential info about the apps).
This allows the malware to successfully avoid detection while being analyzed during the submission process and to eliminate the need to connect to a command-and-control (C2) server to download the malicious components onto the compromised devices.
In all, Check Point researchers who spotted the new Joker variant reported 11 apps to Google, applications that were removed from the official Android marketplace by April 30, 2020.
Check Point’s Manager of Mobile Research Aviran Hazum says that the new method of infection used by Joker includes the following three steps:
1. Build payload first: Joker builds its payload beforehand, inserting it into the Android Manifest File.
2. Skip payload loading: During evaluation time, Joker does not even try to load the malicious payload, which makes it a lot easier to bypass Google Play Store protections.
3. Malware spreads: After the evaluation period, after it’s been approved, the campaign starts to operate, malicious payload decided and loaded
“Joker adapted. We found it hiding in the ‘essential information’ file every Android application is required to have,” Hazum explains.
“Our latest findings indicate that Google Play Store protections are not enough. We were able to detect numerous cases of Joker uploads on a weekly basis to Google Play, all of which were downloaded by unsuspecting users.”
A list of malware sample hashes and Android package names for all the apps found to be infected with Joker payloads is available in the table embedded below.
| SHA256 hash | Package Name |
| db43287d1a5ed249c4376ff6eb4a5ae65c63ceade7100229555aebf4a13cebf7 | com.imagecompress.android |
| d54dd3ccfc4f0ed5fa6f3449f8ddc37a5eff2a176590e627f9be92933da32926 | com.contact.withme.texts |
| 5ada05f5c6bbabb5474338084565893afa624e0115f494e1c91f48111cbe99f3 | com.hmvoice.friendsms |
| 2a12084a4195239e67e783888003a6433631359498a6b08941d695c65c05ecc4 | com.relax.relaxation.androidsms |
| 96f269fa0d70fdb338f0f6cabf9748f6182b44eb1342c7dca2d4de85472bf789 | com.cheery.message.sendsms |
| 0d9a5dc012078ef41ae9112554cefbc4d88133f1e40a4c4d52decf41b54fc830 | com.cheery.message.sendsms |
| 2dba603773fee05232a9d21cbf6690c97172496f3bde2b456d687d920b160404 | com.peason.lovinglovemessage |
| 46a5fb5d44e126bc9758a57e9c80e013cac31b3b57d98eae66e898a264251f47 | com.file.recovefiles |
| f6c37577afa37d085fb68fe365e1076363821d241fe48be1a27ae5edd2a35c4d | com.LPlocker.lockapps |
| 044514ed2aeb7c0f90e7a9daf60c1562dc21114f29276136036d878ce8f652ca | com.remindme.alram |
| f90acfa650db3e859a2862033ea1536e2d7a9ff5020b18b19f2b5dfd8dd323b3 | com.training.memorygame |
Users who suspect that they might have been infected by one of these Joker-infested applications are advised to uninstall the infected apps from their Android device.
They should also check their mobile and credit-card bills to for new subscriptions and immediately unsubscribe (if possible).
Also read: 6 Simple Tips on Cyber Safety at Home
Google said in January 2020 that approximately 1,700 applications infected with Joker malware were removed from the Play Store by Google’s Play Protect since the company started tracking it during early 2017.
At least one set of such malicious Android apps were able to get into the Play Store as discovered by CSIS Security Group security researchers who found 24 apps with more than 472,000 downloads in total on the marketplace in September 2019.
“Sheer volume appears to be the preferred approach for Bread developers,” Android Security & Privacy Team’s Alec Guertin and Vadim Kotov said at the time.
“At different times, we have seen three or more active variants using different approaches or targeting different carriers. [..] At peak times of activity, we have seen up to 23 different apps from this family submitted to Play in one day.”
Joker’s creators are continually forced to switch tactics and to look for gaps in Play Store’s defenses as Google introduces new policies and Google Play Protect scales and adapts its defenses.
“They have at some point used just about every cloaking and obfuscation technique under the sun in an attempt to go undetected,” Guertin and Kotov said.
“Many of these samples appear to be designed specifically to attempt to slip into the Play Store undetected and are not seen elsewhere.”
Also read: Cost of GDPR Compliance for Singapore Companies