KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







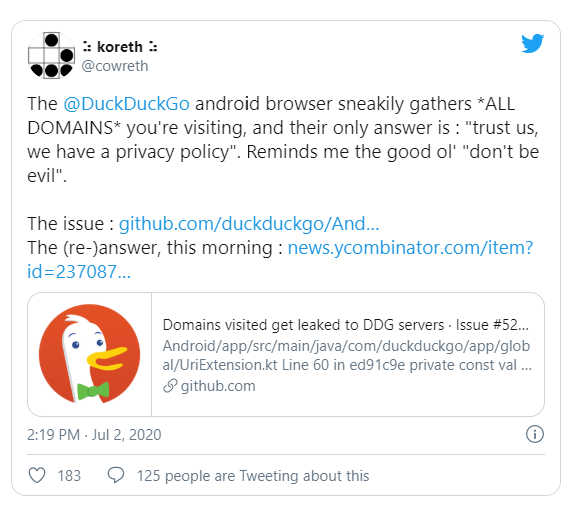
DuckDuckGo, the flag bearers of privacy in the search engine space, has been caught gathering site visits via their Android app.
An ethical hacker, who goes by the username of @cowereth has revisited the issue that was reported a year back on Github as a bug. It was brushed under the carpet then due to various overlapping reasons.
DuckDuckGo stores the favicons(a small website icon that shows in the address bar or bookmark tabs) of the websites on a different internal server hosted at a subdomain icons.duckduckgo.com.
In general, when you visit a website the hostnames of the visited website calls its own server or checks with the local browser cache(whichever is latest) to fetch the favicon.
However, in the Duckduckgo Android browser, instead of calling up for the favicon from the visited website server or the browser’s cache(local client, for a predetermined time), it calls their server as mentioned earlier to request the favicon of the website.
In easier words, it transfers the user’s browsing data to one of its servers without the user’s consent.
DuckDuckGo has brushed this a regular thing, citing error reports based on favicon display being a complex exercise for their android browser app.
The purpose of the request you observed is to retrieve a website’s favicon so that it can be displayed in certain places within the app or on the results page. We use an internal favicon service because it can be complicated to locate a favicon for a website. They can be stored in a variety of locations and in a variety of formats. The service understands these edge cases and simplifies retrieval within our apps and our search engine. At DuckDuckGo, we do not collect or share personal information. That’s our privacy policy in a nutshell. For more detailed information on that, you can checkout our privacy policy at https://DuckDuckGo.com/privacy. The favicon service, as with all our services, adheres to this privacy policy in that the requests are anonymous and do not collect or share any personal information.
Furthermore, they have also stated the usage policy addressing the uncertainty over Favicons, in their privacy policy section.
Different service is used because the favicon is saved in different formats and sizes.
Furthermore, DDG reiterates on the promises to not collect any user information.
Also read: Free PDPA Singapore Checklist 2020
While DDG is correct on the different ways of favicon being referenced in HTML, it is not a convincing reason for storing user’s data(of favicons and hostnames of websites visited) on a different service instead of the user’s end(the host).
The DuckDuckGo Android browser app could use the retrieved used data to tailor user profiles based on individuals, find out the IP address from which a particular website is visited.
Other major browsers stores the favicons and other related stuff on their storage itself, relying less on the website’s server.
That has been the norm since Internet explorer, the browser which introduced favicons. W3 also states it for favicons, which sets the web standards for the Internet.
After the criticism started pouring in, the CEO of DDG, Gabriel Weinberg posted on Hacker News, acknowledging the issue, while reassuring the users on not using the favicons for anything other than displaying them on their Android browser.
After that, he replied to comments on the thread, reassuring the company’s commitment to user privacy.
DuckDuckGo has committed an update to fix the issue soon.
Also read: The FREE Guide To The 9 Obligations Of PDPA