KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







In what is being referred to as ‘BlueLeaks,’ a group called Distributed Denial of Secrets (DDoSecrets) has released a 269 GB data dump containing 24 years worth of records from over 200 police departments.
What can be observed “among the hundreds of thousands of documents” comprising FBI reports and bulletins are also full International Bank Account Numbers (IBANs), phone numbers, and email addresses.
DDoSecrets is similar to WikiLeaks, but with a commitment to make secrets public that even WikiLeaks chose to withhold.
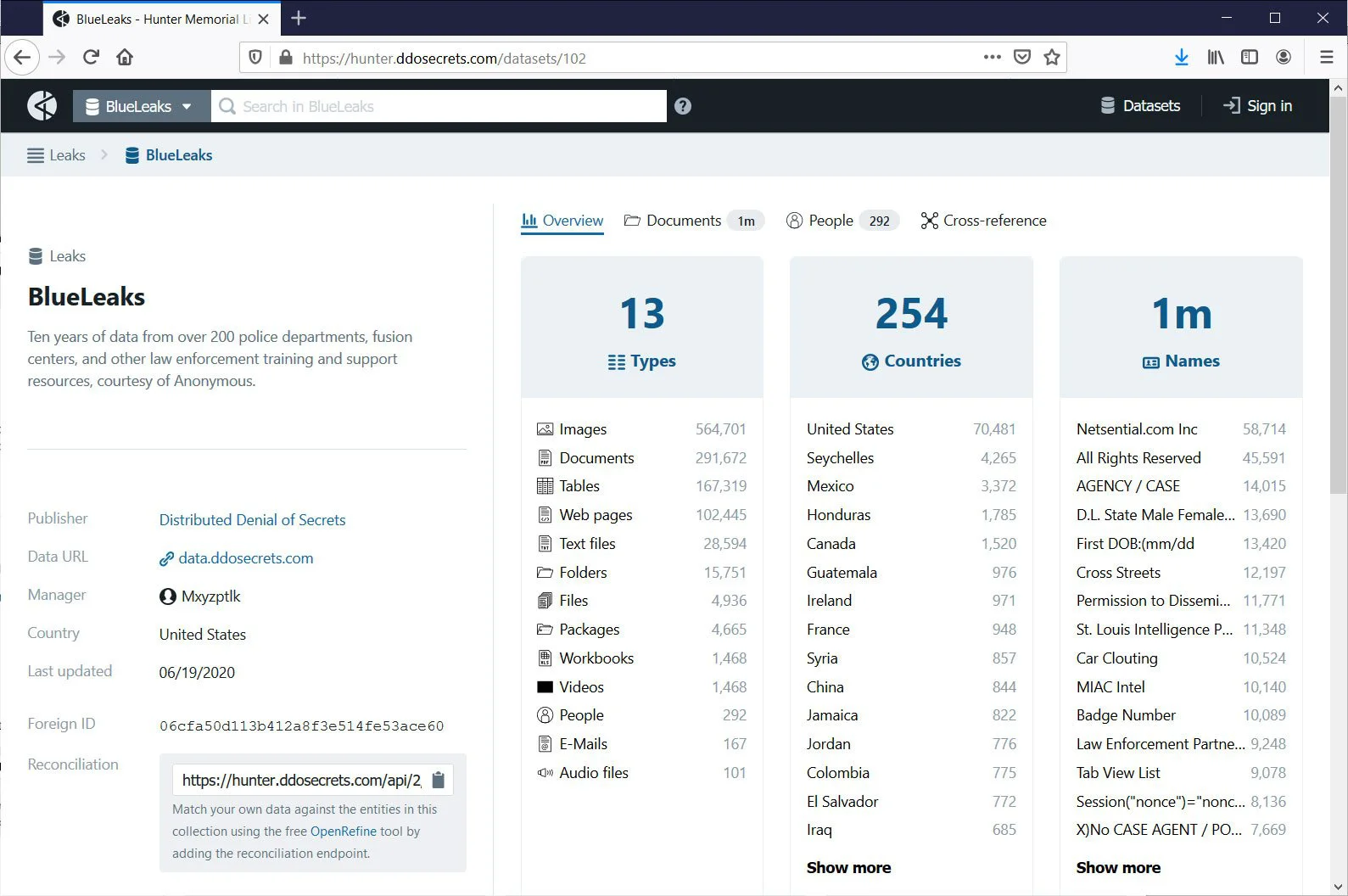
At the time of this writing, the link posted by DDoSecrets is still accessible and exposes records ranging from images, documents, data tables, web pages, emails, and text files.
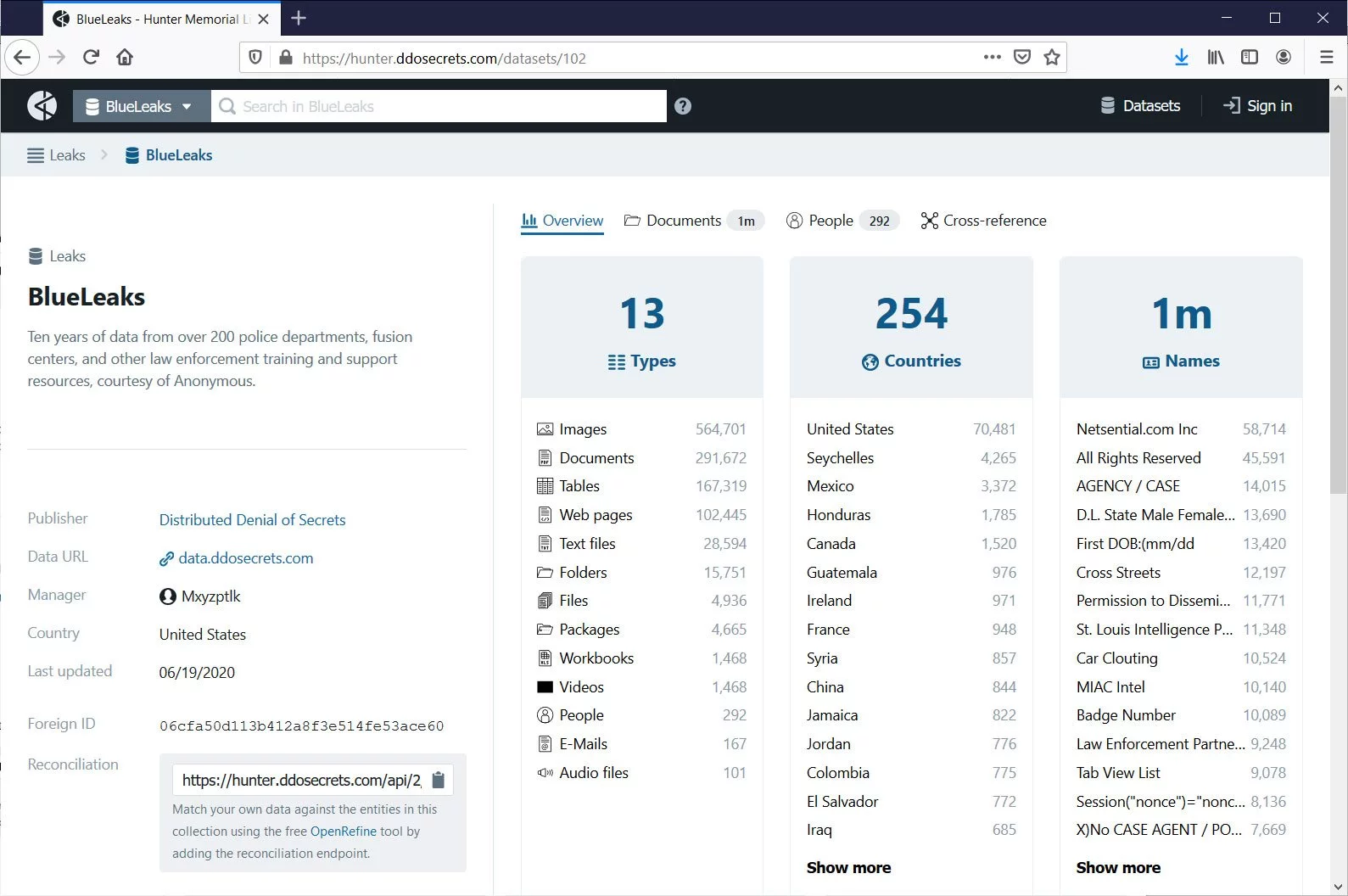
Some of the organizations and departments whose data was exposed by this leak include:
Some of the agencies in #BlueLeaks include:
Alabama Fusion Center
Austin Regional Intelligence Center
Boston Regional Intelligence Center
Colorado Information Analysis Center
California Narcotic Officers' Association
Delaware Information and Analysis Center
FBI Houston Citizens Academy Alumni Association
FBI National Academy Association Arkansas/Missouri Chapter
FBI National Academy Association Michigan Chapter
FBI National Academy Association of Texas
Fort Worth Intelligence Exchange
Minnesota Fusion Center Intelligence Communications Enterprise For Information Sharing and Exchange
Illinois Crime Reporting and Information - Metro East
Iowa Law Enforcement Academy
Iowa Fusion Center
Faith-Based Information Sharing and Analysis Organization
Missouri Information Analysis Center
Northern California Regional Intelligence Center
Nevada Cyber Exchange
New Hampshire Information and Analysis Center
Northern Nevada Regional Intelligence Center
North Texas Fusion Center
Nevada Threat Analysis Center
Orange County Intelligence Assessment Center
South Carolina Information and Intelligence Center
San Diego Crime and Intelligence Analysis Association
South Dakota Fusion Center
Southeast Florida Fusion Center
Southeastern Michigan Association Chiefs of Police
Infragard (San Francisco Bay Area)
Texas Narcotic Officers Association
Utah Statewide Information and Analysis Center
Virginia Law Enforcement National Security Network
Wisconsin Statewide Intelligence CenterThe BlueLeaks data dump was published on Juneteenth (June 19th), indicating the likely motive behind the leak, perhaps retaliation given the recent events and protests.
Brian Krebs reported on the leak and was able to obtain an analysis from the National Fusion Center Association (NFCA) on June 20th, certifying the authenticity of the leaked records.
The findings by NFCA indicate that the dates and timestamps within the leaked documents cover periods from as early as 24 years ago, going back to August 1996.
“Additionally, the data dump contains emails and associated attachments,” stated the findings, as reported by KrebsOnSecurity.
“Our initial analysis revealed that some of these files contain highly sensitive information such as ACH routing numbers, international bank account numbers (IBANs), and other financial data as well as personally identifiable information (PII) and images of suspects listed in Requests for Information (RFIs) and other law enforcement and government agency reports.”
The NFCA told Krebs that the source of the leak is a data breach at Netsential, a software development firm based in Houston, TX.
Netsential’s website states
Netsential’s website states: “Our software is currently being used by Fortune 500 companies, financial institutions, small and medium sized businesses, associations, online publications, government agencies and schools throughout the United States.”
“Netsential Sites are Easy to Maintain – If you can cut and paste – you can maintain and update your website with Netsential’s browser-based software.”
It is unclear if the breach impacted the company’s other clients, and the company’s Director, Stephen Gartrell, did not provide any comment to KrebsOnSecurity.
Also read: 9 Policies For Security Procedures Examples
According to NFCA, the leaked data could be exploited by hacktivists, cybercriminals, and nation-states to target fusion centers and intelligence agencies.
The leaked information may not aid in exposing any potential police misconduct but may pose a danger to victims and endanger ongoing investigations as Stewart Baker, an attorney at Steptoe & Johnson LLP, noted.
“With this volume of material, there are bound to be compromises of sensitive operations and maybe even human sources or undercover police, so I fear it will put lives at risk,” said Baker.
Baker drew attention to the nature of the work of fusion centers in general, which involves intelligence gathering on threats and criminals, and not necessarily keeping data on police misconduct.
“Every organized crime operation in the country will likely have searched for their own names before law enforcement knows what’s in the files, so the damage could be done quickly. I’d also be surprised if the files produce much scandal or evidence of police misconduct. That’s not the kind of work the fusion centers do.”
A member of DDoS, Emma Best spoke up via a Twitter thread, to clarify some of the misconceptions about their group made by the Attorney General’s Office in Bahama:
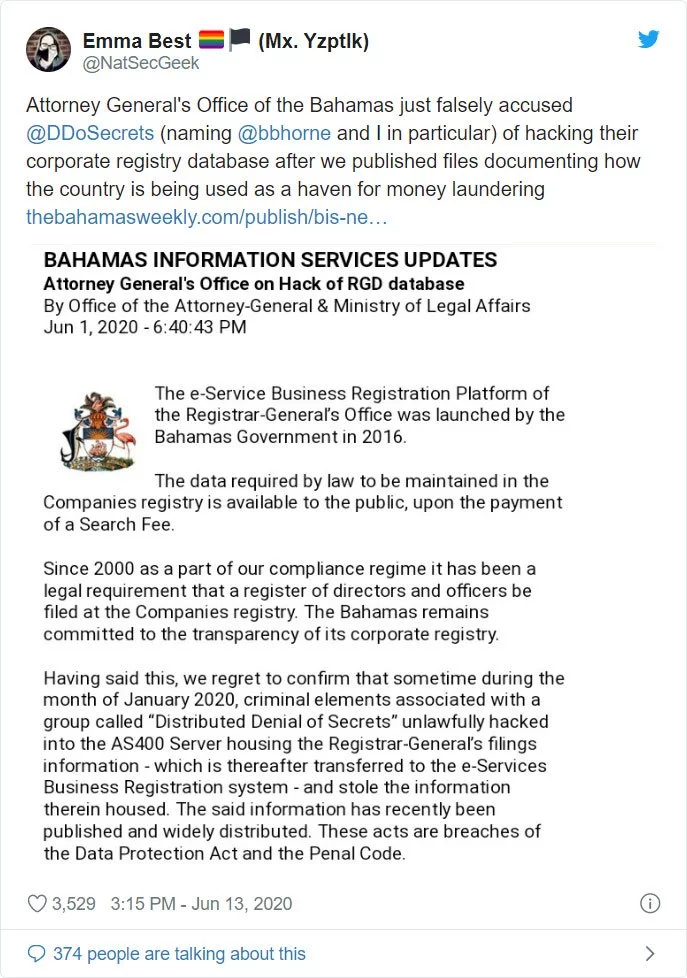
“DDoSecrets was formed [in] December 2018, not December 2019. This was reported by the AP at the time and can be easily determined by looking at our website or simply Googling the issue. The data isn’t from [January] 2020. Our members are openly listed on our site.”
“Actually, December 2018 was only our public launch. The Architect and I soft-launched in November and started working on the project even earlier,” added Best.
As of now, the giant 269 gig dump is being analyzed by journalists and various professionals for what all information has it exposed, and more updates will follow should any important bits of information come to light.
Suffice to say, a data leak this scale, targeting over 200 law enforcement departments, is a first of its kind.
Also read: 7 Client Data Protection Tips to Keep Customers Safe