KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!





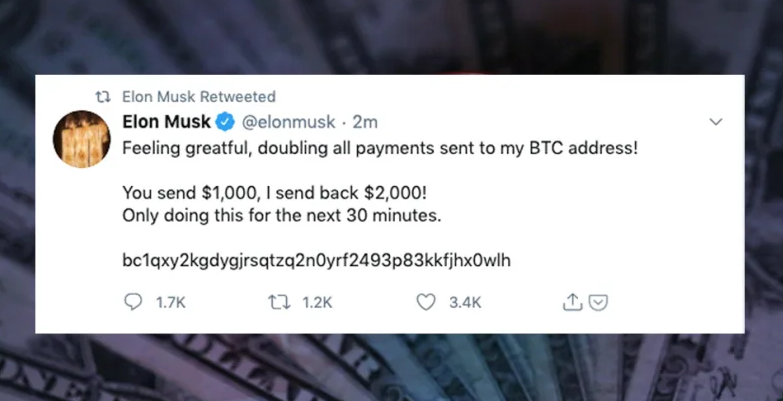

Something normal happened on Twitter earlier this afternoon. Someone claiming to be Elon Musk started tweeting an obvious scam to entice his loyal bootlickers to send bitcoin to a random cryptocurrency wallet. This happens all the time, but the strange thing about today was that the tweets were coming from Musk’s verified account. And nearly identical tweets were coming from accounts of people like Bill Gates, Jeff Bezos, Kanye West, Joe Biden, Barack Obama, Warren Buffett, every major crypto-exchange, and I’m quickly losing track of all of ‘em.
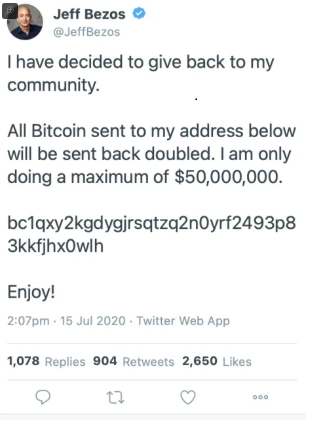
This is obviously the result of a Twitter hack the likes of which we’ve never seen before. A spokesperson for the social network told Gizmodo that they are aware of the situation and will issue a statement shortly, which they did right before publication.

The hackers appear to be using a number of different wallets but the address being used on tweets from Musk and Gates has received around $59,000 worth of bitcoin so far.
The sudden flurry of activity seems to be calming down. Apple, for instance, is back to its usual standard of having zero tweets after it tweeted the scam just moments ago. But the list of prominent users who were affected continues to grow and now the fake screenshots are taking over so we’ll probably never sort out all the people who were hit by the attack.
Also read: How to Register Data Protection Officer (DPO) in ACRA Bizfile+
This is an ongoing story and we’ll continue updating this post as we receive more information.
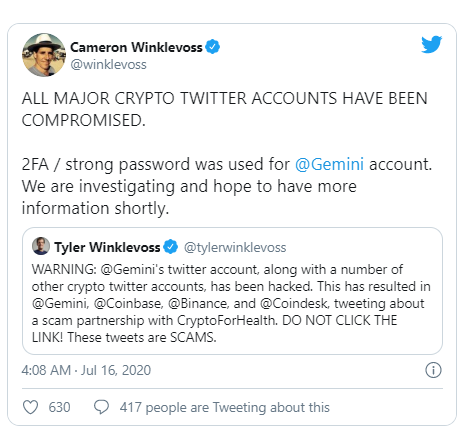
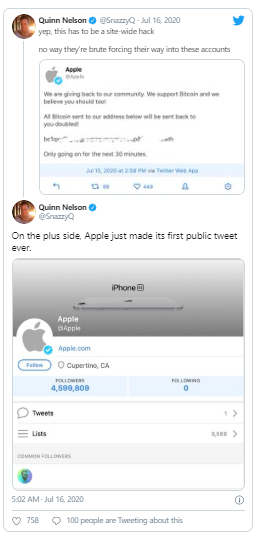
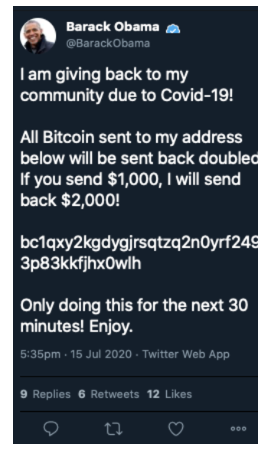
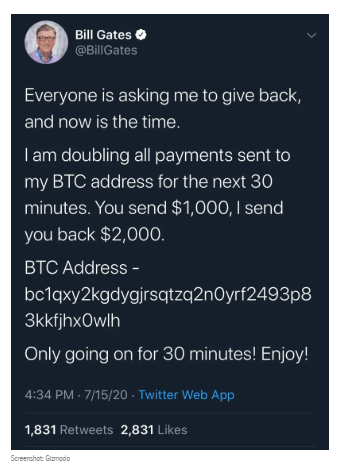
Update 6:45pm ET: Twitter, apparently in an effort to stave off the embarrassing hackfest, has blocked many verified accounts from tweeting, which is probably for the best.
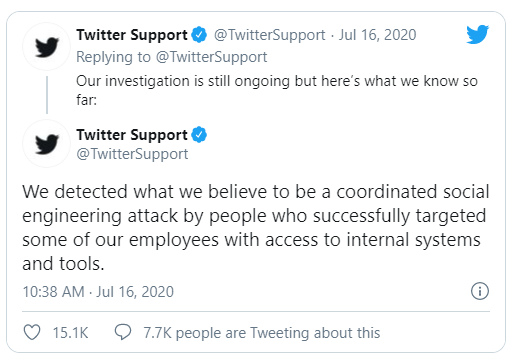
Also read: Policies For Security Procedures Examples