KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Germany’s federal cybersecurity agency today urged iOS users to immediately install the iOS and iPadOS security updates released by Apple on May 20 to patch two actively exploited zero-click security vulnerabilities impacting the default email app.
“Due to the criticality of the vulnerabilities, the BSI recommends that the respective security update be installed on all affected systems immediately,” the BSI (Bundesamt für Sicherheit in der Informationstechnik) said.
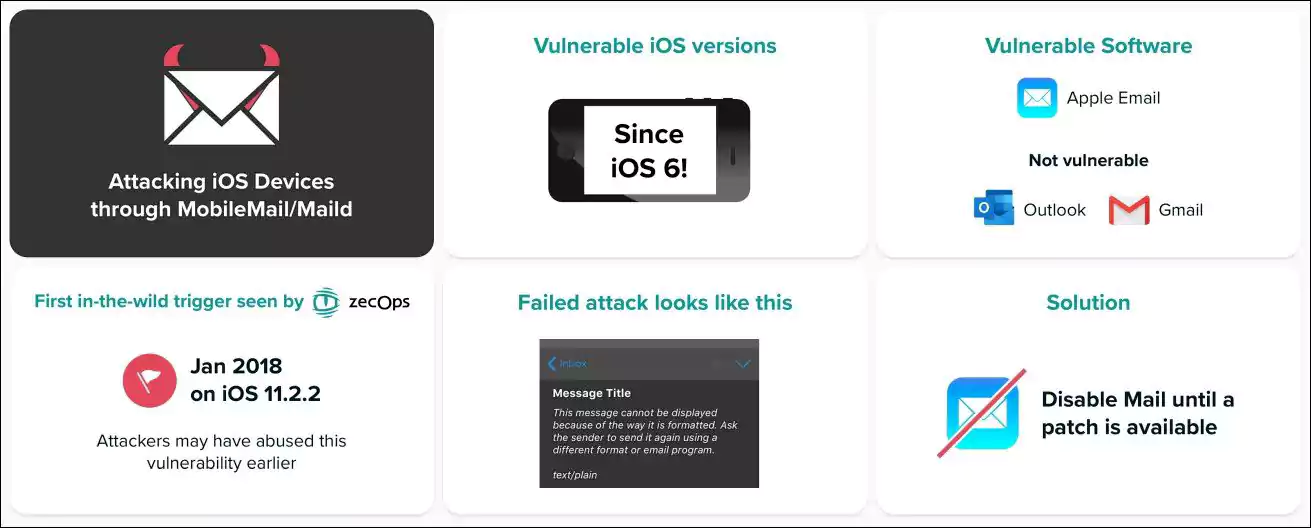
Cybersecurity startup ZecOps disclosed the bugs (zero-days at the time of the disclosure) after discovering ongoing attacks that targeted iOS users since at least January 2018.
The two no-click vulnerabilities are a memory consumption issue tracked as CVE-2020-9819 that may lead to heap corruption and an out-of-bounds write issue tracked as CVE-2020-9818 which may lead to unexpected memory modification or application termination, both of them triggered after the Mail app processes a maliciously crafted mail message.
The MailDemon security flaws were addressed by Apple with the release of iOS 13.5 and iPadOS 13.5 which come with improved memory handling and bounds checking.

“We believe that these attacks are correlative with at least one nation-state threat operator or a nation-state that purchased the exploit from a third-party researcher in a Proof of Concept (POC) grade and used ‘as-is’ or with minor modifications,” ZecOps said at the time.
Luckily the attacks ZecOps mentioned were directed at against high-profile targets which means that regular users won’t be directly targeted until exploits for the two bugs fall in the hands of threat actors with less ambitious goals.
According to the iOS 13.5 security release notes, the vulnerabilities found by ZecOps affect iPhone 6s and later, iPad Air 2 and later, iPad mini 4 and later, and iPod touch 7th generation.
Based on ZecOps’ analysis of the two bugs, all devices running iOS 3.1.3 up to 13.4.1 are exposed to potential attacks that would make it possible to run remote code on compromised iPhone and iPad devices, and providing access to, leak, edit, and delete emails.
As ZecOps’ founder and CEO shared, “these vulnerabilities also existed since the first iPhone (iPhone 1 / iPhone 2G) and since at least iOS 3.1.3.”
In an official statement shared after ZecOps disclosed their findings, Apple disputed the researchers’ claims of ongoing attacks:AD
Apple takes all reports of security threats seriously. We have thoroughly investigated the researcher’s report and, based on the information provided, have concluded these issues do not pose an immediate risk to our users. The researcher identified three issues in Mail, but alone they are insufficient to bypass iPhone and iPad security protections, and we have found no evidence they were used against customers. These potential issues will be addressed in a software update soon. We value our collaboration with security researchers to help keep our users safe and will be crediting the researcher for their assistance.
ZecOps responded with the following:
According to ZecOps data, there were triggers in-the-wild for this vulnerability on a few organizations. We want to thank Apple for working on a patch, and we’re looking forward to updating our devices once it’s available. ZecOps will release more information and POCs once a patch is available.