KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Chrome version 104 accidentally introduced a bug that removes the user requirement to approve clipboard writing events from websites they visit.
This functionality isn’t limited to Google Chrome. Safari and Firefox also allow web pages to write to the system clipboard, yet they have gesture-based protections in place.
Chrome developers have identified the problem but a fix has yet to come, so it persists in current versions of the Google Chrome browser for mobile and desktop.
Also Read: Battling Cyber Threats in 4 Simple Ways
The system clipboard is a temporary storage location on operating systems. It’s typically used for copy-pasting and it can involve sensitive information such as banking account numbers, cryptocurrency wallet strings, or passwords.
Overwriting this temporary storage space with arbitrary content puts users at risk as they could become victims of malicious activity.
Threat actors could lure users to specially crafted websites impersonating a legitimate cryptocurrency service. When the user tries to make a payment and copies the wallet address to the clipboard, the website can write to the clipboard the threat actor’s address.
On some websites, when the user selects text to copy from a web page, additional content is appended to the clipboard (typically the page URL). In this case, though, the clipboard fills up with arbitrary content without any visible indication or user interaction.
Developer Jeff Johnson highlights in a blog post that explores the topic, all web browsers that support clipboard writing have poor and inadequate safeguards.
User gestures that give a web page permission to use the clipboard API include the keyboard shortcut for copying content (Ctrl+C), but in many cases, merely any interaction with the website is enough.
Johnson tested on Safari and Firefox and found that pressing the down arrow key or using his mouse scroll wheel to navigate on a site gave clipboard writing permission to the loaded web page.
Also Read: What is Smishing? How Can We Prevent It? Explained.
Considering how common these actions are, this permission is sufficiently risky to deserve a fix.
“While you’re navigating a web page, the page can, without your knowledge, erase the current contents of your system clipboard, which may have been valuable to you, and replace them with anything the page wants, which could be dangerous to you the next time you paste. Why did web browser vendors ever allow this?” – Jeff Johnson
Thankfully, Johnson’s tests confirmed that websites could not abuse this permission to read clipboard contents, which would be detrimental to user privacy.
To determine if this issue impacts your web browser, you can visit “webplatform.news” and then “paste” your clipboard contents into a text app, like Windows Notepad.
If you see the following message, your browser is vulnerable to permission abuse.
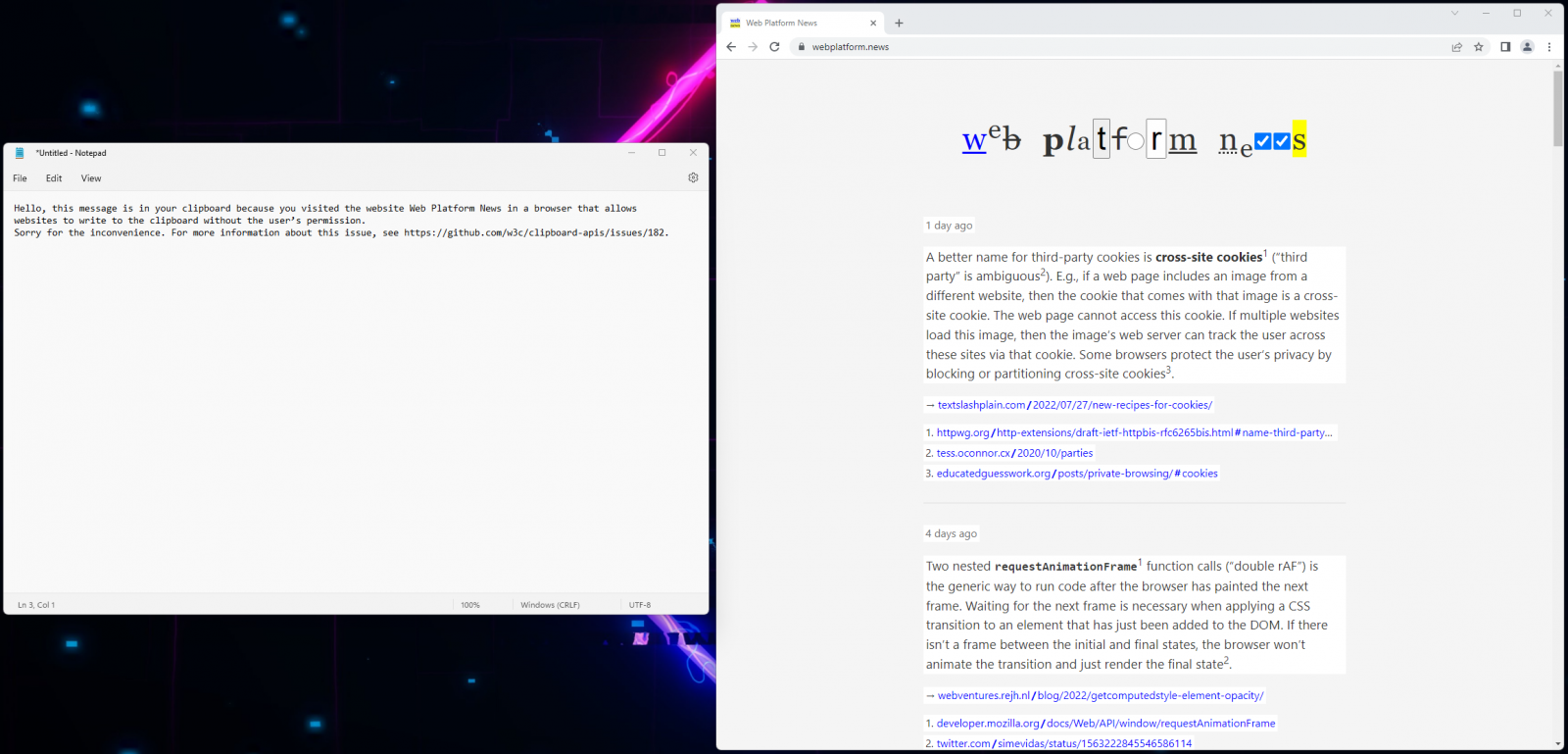
Not all Chromium-based browsers are impacted by this issue, though. In tests from BleepingComputer, Brave didn’t give the testing site permission to overwrite the clipboard.
However, Johnson’s embedded test box that fills the visitor’s clipboard with website navigation actions worked on all browsers, so the cause of the discrepancy is unclear.
Johnson says that users overly worried about this problem can use his ‘StopTheMadness‘ extension but warns they will still not be 100% protected from arbitrary clipboard overwrites in all circumstances.