KEEP IN TOUCH
Subscribe to our mailing list to get free tips on Data Protection and Cybersecurity updates weekly!







Microsoft has released Sysmon 14 with a new ‘FileBlockExecutable’ option that lets you block the creation of malicious executables, such as EXE, DLL, and SYS files, for better protection against malware.
This feature is a powerful tool for system administrators as it allows them to block the creation of executables based on various criteria, such as the file path, whether they match specific hashes, or are dropped by certain executables.
For example, if you have a list of known malware hashes, you can configure Sysmon to block the creation of executables matching those hashes. Or, if you want to prevent malicious Office attachments from dropping malware, you can stop the creation of executables from Word or Excel.
Also Read: Accountability Obligation: What every Organization should know
For those not familiar with Sysmon, or System Monitor, it is a free Microsoft Sysinternals tool that can monitor systems for malicious activity and log events to the Windows Event Log.
Sysmon will monitor basic events such as process creation and file time changes by default to Event viewer. However, it is possible to create a custom configuration file containing advanced options that determines what Sysmon monitors or blocks.
Users can find the complete list of directives in the Sysmon schema, which can be viewed by running the sysmon -s command at the command line.
The current Sysmon schema is version 4.82, which now includes the ‘FileBlockExecutable’ configuration option to block the creation of executables based on their path, name, hash, and the program trying to create the files, as shown below.
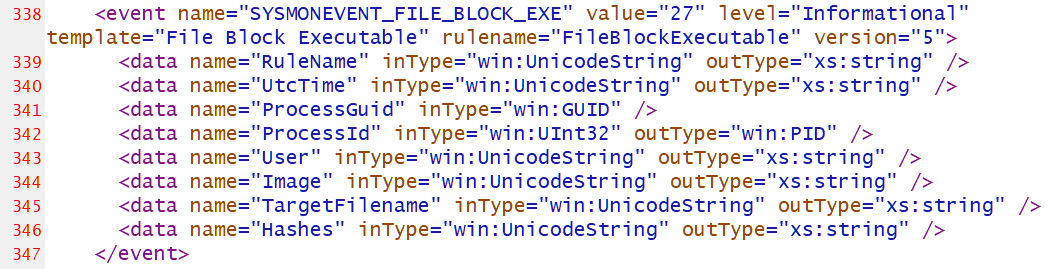
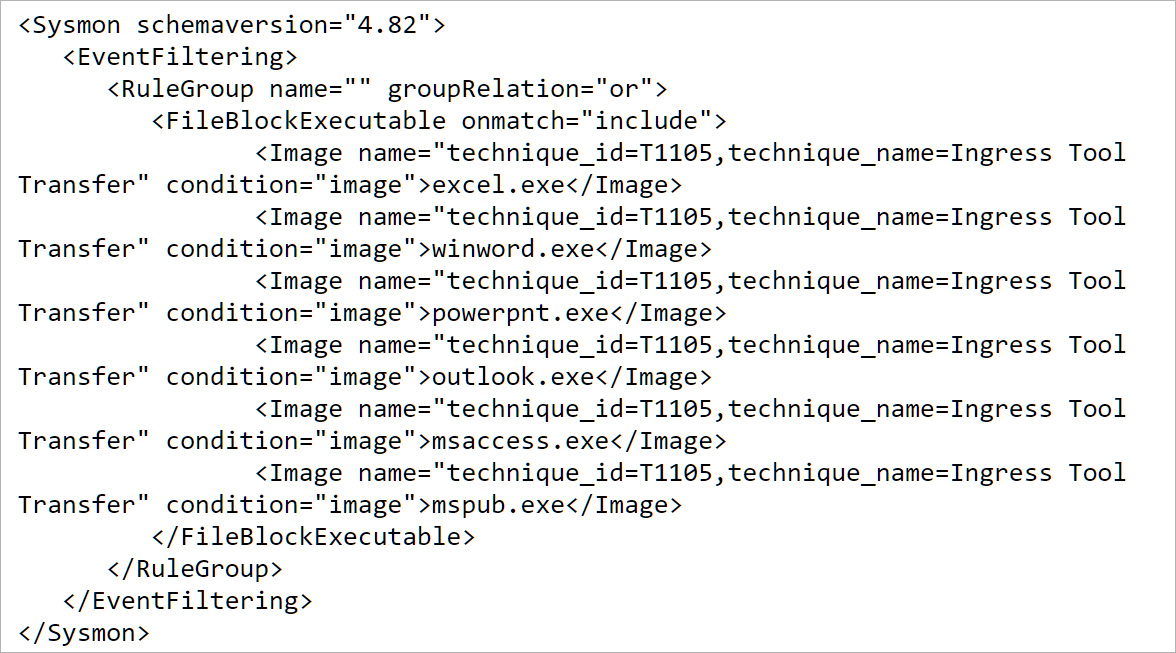
For example, to prevent Microsoft Office applications from creating new executable files, you can use this rule shared by Olaf Hartong in his great writeup on the latest version of Sysmon.
Also Read: 13 phishing attack types and how to protect your business against them
This rule, shown below, will block the creation of any executable by Excel, Word, PowerPoint, Outlook, Access, or Publisher and log any events to the Event Log under the name “technique_id=T1105,technique_name=Ingress Tool Transfer.”
To start Sysmon and direct it to use the above configuration file, you would execute the sysmon -i command and pass the configuration file’s name.
In our example, the configuration file’s name is msoffice-fileblock.xml, so we would use the following command from an Administrative Command Prompt to start Sysmon:
sysmon -i msoffice-fileblock.xmlOnce started, Sysmon will install its driver and begin collecting data quietly in the background.
All Sysmon events will be logged to ‘Applications and Services Logs/Microsoft/Windows/Sysmon/Operational‘ in the Event Viewer.
With the FileBlockExecutable feature enabled, when an executable is created and matches a rule, Sysmon will block the file and generate an ‘Event 27, Sysmon’ entry in Event Viewer.
For example, when testing this feature, we specified not to allow the creation of executables in the C:\ProgramData folder, which is commonly done by malware droppers.
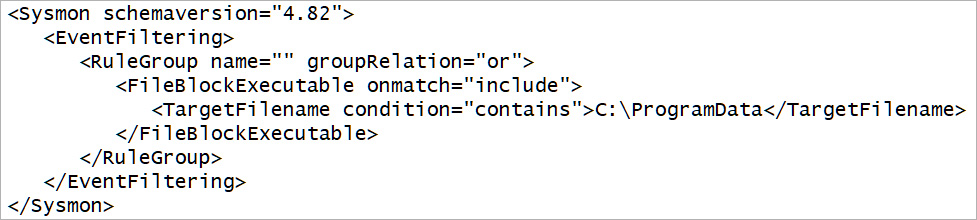
We then attempted to copy C:\Windows\notepad.exe to C:\ProgramData, triggering the following event log when the file creation was blocked.
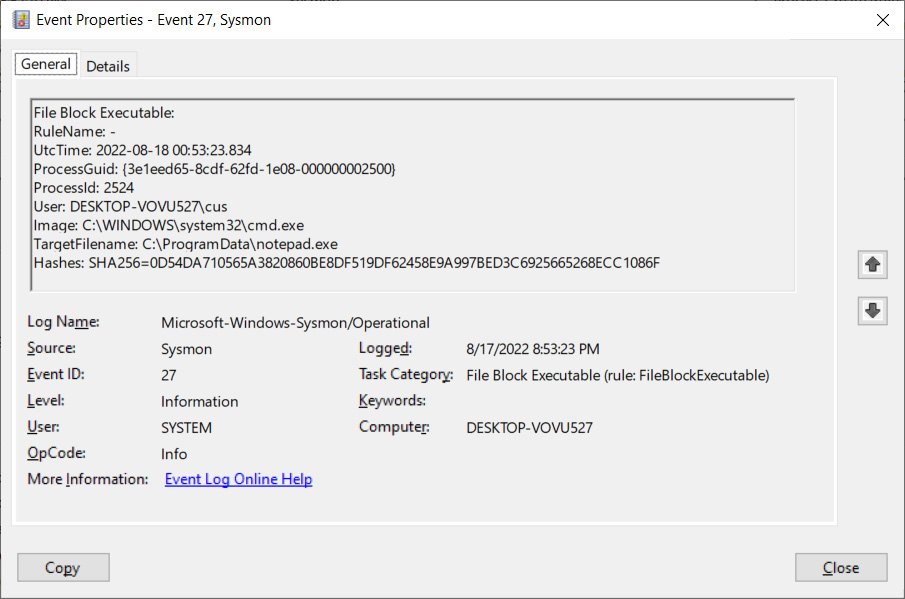
The created Event Log entries will contain a lot of valuable information, explained below:
Hartong says that Sysmon will determine if a file is an executable based on the file header. Therefore, Sysmon will also block DLL and SYS executables as they utilize the same MZ file header.
For those who want a premade Sysmon configuration file that uses this feature to block known malware and hack tools, you can use one created by security researcher Florian Roth.
While this is a very useful feature, it should not be seen as 100% secure, as security researcher Adam Chester has already come up with a method to bypass the FileBlockExecutable directive.
Therefore, while it’s useful for monitoring and blocking malware, it should not be the only protection you rely on.
For those who want to learn more about Sysmon, it is strongly recommended that you read the documentation on Sysinternals’ site and play around with the various configuration options.
Unfortunately, Sysmon is not a well-documented program, requiring users to play with the various directives to see how they work and what events are written to the event log.
It is also highly recommended to read Olaf Hartong’s blog posts about Sysmon, as he documents the new features as they are released.
Finally, admins can use or read through the premade Sysmon configuration files from Florian Roth and SwiftOnSecurity to see how directives can be used to block malware.